The PassKey logins to your favourite websites using the stored passwords (that are never revealed to your browser computer, just to the website), achieving an unprecedented level of security without requiring any change in the Internet authentication infrastructure. We have prototypes already working for the major websites. See it in action:
Traditional password managers are designed to be used only on trustworthy computers. You cannot securely plug your pendrive containing your password list on a Cybercafe computer, without risking your digital identity and digitally controlled assets. Sometimes, you should assume your password has been compromised as soon as you type it on an untrusted keyboard.
The following diagram shows the inner workings of the PassKey and the login and browsing flowchart:
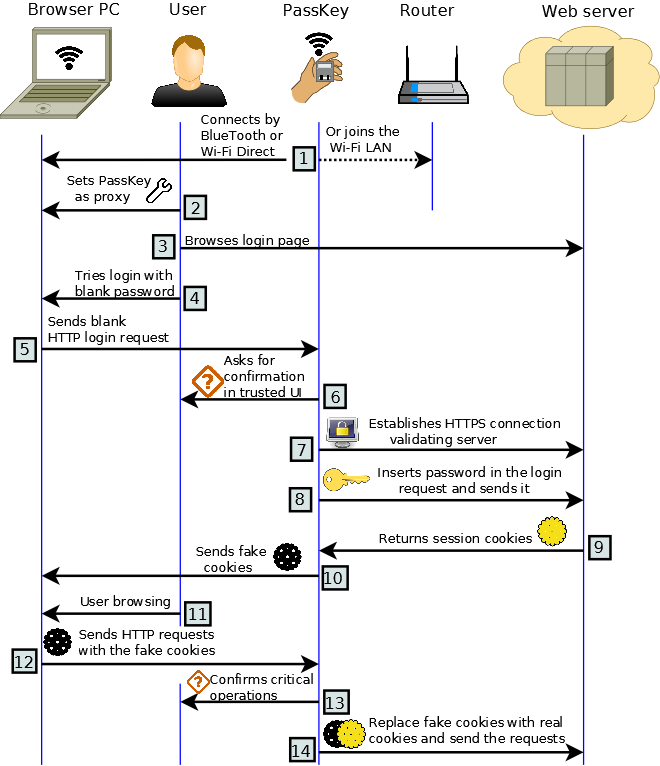
The Identiva PassKey is the only device that allows you to log in using any untrusted computer with high security and no risk. And also, it is compatible with any password-enabled website in the world. The innovations are protected by patents pending in US and Europe.
The proof-of-concept hardware/software platform used for testing was a wifi-enabled smart-watch running the Android operating system and adapted for being able to simultaneously run a GNU/Linux distribution. The software was implemented in Python. For the production device, we will target a single-purpose security-hardened hardware platform such as a secure micontroller, which will just require adding a display, buttons and the battery. Also the PassKey supports password backups in the cloud. The requirements for the cloud servers are simple to met since the password backup service can be implemented on all of the standard web development languages, platforms and frameworks. We plan to make all the software open source for ease of auditing.
The Identiva PassKey wireless device concept was fully implemented and tested using a smart-watch platform. Nevertheless we plan to increase its security by using a single-purpose low-cost, power-efficient computing platform, such as one based on a secure microcontroller or IoT board. The platform must have a Wi-fi and/or blue-tooth connectivity, an LCD display, a battery and a simple user interface having two confirmation buttons (see below)

The core computing operations performed by the device are storing a password database, opening secure connections to external websites (or the computer) using the SSL/TLS protocol suite, verifying authentication certificates, and sending passwords in encrypted form. Also the PassKey is able to intercept the traffic between the untrusted computer and the website and provide the authentication tokens when needed, without disclosing them. Last, the PassKey can offload downloading or uploading large files to the untrusted computer without disclosing sensitive information, to preserve the device battery life. These operations are performed by a single software component that resides in the PassKey. On the computer side, the PassKey requires a simple two-step configuration process that does not require administrative privileges and involves configuring the PassKey as an Internet proxy and installing a root certificate provided by the PassKey. An optional user-mode software component can be run on the untrusted computer to multiplex Internet streams and reduce the CPU-load of the PassKey, increasing its battery lifetime.
For secure-critical operations, such as changing a password, updating your personal data or making a bank transaction, you’ll be able to configure the PassKey to require specific confirmations. Your can use your PassKey today, because it is compatible with all your favorite websites like no other authentication system. Having a simple user interface with a single confirmation button makes the PassKey login process secure, easy and natural.
Read more » Sergio Demian Lerner
Sergio Demian Lerner




 Ilia Baranov
Ilia Baranov
 dariocose
dariocose
 James P.
James P.
 Arcadia Labs
Arcadia Labs
Hi, is there any chance to revive this project? It seems a great idea, and I would be interested in some updates about it, if anyone still has any plans of continuing it.