TLDR
Spoiler Alert! This is a walk through for the Badge Enabled Non Directive Enigma Routine (B.E.N.D.E.R) v2.0. Major storyline and context is left out because it's assumed you have a badge, have given up, and just want to learn WTF was going on (and we encourage you to try this stuff as well). Let this be your guide and we assume you read the previous log on how to play B.E.N.D.E.R.
North Village
This challenge requires that the player exploit a buffer overflow to execute a command which requires root privileges to run. You are in a bathroom.

Main Puzzle
Looking at SHITTER_STALL_3 hints at the need to "flush" the toiler as it is about to "overflow" and that your gag sounds "ekoz" throughout the bathroom. EKOZ is a lulz version of ECHO and susceptible to a buffer overflow. By echoing a very long string > 24 characters, it overflows and executes the SYSTEM call command with root privileges.
and!xor $ EKOZ 123456789012345678901234 FLUSH
With great power comes great responsibility.
Your super 1337 badge computer executes a flush.
Almost everything goes down the hole, except a few remaining letters: CYBERPATHOGENS
Something must be clogged as everything begins to flow back and fill up the bowl.
Now that you know the letters in the toilet spelled out "CYBERPATHOGENS" one would think that this is the hidden password in the area that you need to yell into the GLORYHOLE
and!xor $ HACK GLORYHOLE WITH CYBERPATHOGENS
After yelling the password you hear a faint reply...
CONDOM...COMBO...IM...A...TEAPOT...
Now you are given a hint that the combination to the CONDOM_VENDING_MACHINE is related to "I'm a teapot," -> HTTP Status 418
and!xor $ LOOK AT CONDOM_VENDING_MACHINE
Always play it safe, even in the apocalpyse! The dispense knob wont turn, it requires a quarter.
However gum is jammed in the coin slot (we hope its gum).
There's also a 3 wheel COMBO_SPINNER for maintenance.
and!xor $ HACK COMBO_SPINNER WITH 418
The combination works, the door to the vending panel swings open, and some new l00t drops on the floor.
North Village Hack: 15% Completion Earned
The reward loot: USB_CONDOM
Easter Egg
There is a hidden phone number in SHITTER_STALL_2 which is revealed by looking at the tagging.
and!xor $ LOOK AT SHITTER_STALL_2
A nuclear winter toilet stall. Nothing here but a bunch of bathroom stall TAGGING.
and!xor $ LOOK AT TAGGING

4 GUD TIEM CALL 805-203-6888
YELL NAYM IN GLORYHOLE
Calling the phone number and listening to the voicemail plays a SSTV encoded photo. Decoding that photo is DICKBUTT.
Yelling this in to the GLORYHOLE per its instructions unlocks the easter egg points.
South Village
This challenge requires that the player decode a punch tape, debug the instructions, and submit a patch. You found the internet...a series of tubes...
Main Puzzle
Looking at the aptly titled binder "RTFM" provides instructions on how to look at the MASTER_TAPE and how to patch. Initially the player must look at the MASTER_TAPE and decode it to determine why the TACO_NET is offline. Tip of the hat to the TyMkrs for inspiring this puzzle from CypherCon 4.0.
and!xor $ LOOK AT MASTER_TAPE
Here's what your copy of the current master tape looks like...
-^-^-^-^-^-^-
| .O..O*..O |
| OO..O*OO. |
| .O..O*..O |
| .O.O.*O.. |
| ..O..*... |
| O.OO.*... |
| ....O*O.O |
| O...O*O.. |
-^-^-^-^-^-^-
Initially it should confuse the player given punched holes "O" are 1's on tape and dots "." are zero's. Translating this to a table, removing the parity bit, and finally to hexadecimal reveals its ASCII value.
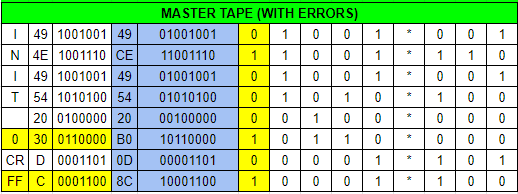
"INIT 0 CRFF" The errors are highlighted in yellow. No wonder it won't start. This needs to be changed to "INIT 5 CRLF" in addition to fixing the parity error given ASCII requires an EVEN parity; right now it is ODD which is EIA formatted. The following patch would fix this.
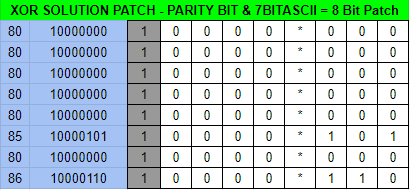
Ensure you have the TAPE_PUNCH first, which is obtained from the EAST_VILLAGE as a freebie item.
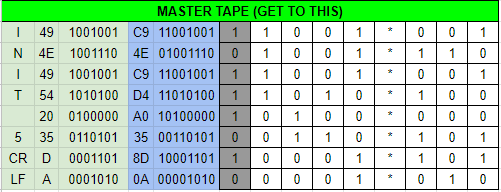
and!xor $ HACK PUNCH_TAPE WITH 8080808080858086
You carefully punch your patch on a blank tape strip and submit it in to the PNEUMATIC_TUBE_SYSTEM.
SHOOOMF! (Thats the sound pneumatic vacuum tubes make)
-^-^-^-^-^-^-
| O....*... |
| O....*... |
| O....*... |
| O....*... |
| O....*... |
| O....*O.O |
| O....*... |
| O....*OO. |
-^-^-^-^-^-^-
Patiently you wait and a copy of the patched master tape is returned to you...
-^-^-^-^-^-^-
| OO..O*..O |
| .O..O*OO. |
| OO..O*..O |
| OO.O.*O.. |
| O.O..*... |
| ..OO.*O.O |
| O...O*O.O |
| ....O*.O. |
-^-^-^-^-^-^-
The patch works! This machine which is the TACONET comes back to life!.
Also a taxidermied squirrel appears wedged in the tube now...who sent that through?
New l00t awaits you as well, for all your ancient hackery.
South Village Hack: 15% Completion Earned
Easter Egg
The instructions say to hack the PUNCH_TAPE with the patched code. By simply hacking it with a TAPE_PUNCH and just poking holes for fun, the following happens.
and!xor $ HACK PUNCH_TAPE WITH TAPE_PUNCH

Easter Egg Hack: 4% Completion Earned
Look at you not following directions. Just blindly punching tape for the shit of it.
Marching to the beat of your own drum...That's worth some points.
East Village
This challenge requires that the player to create a hardware implant to save Joe Fitz's life. You are in a cryogenic lab.
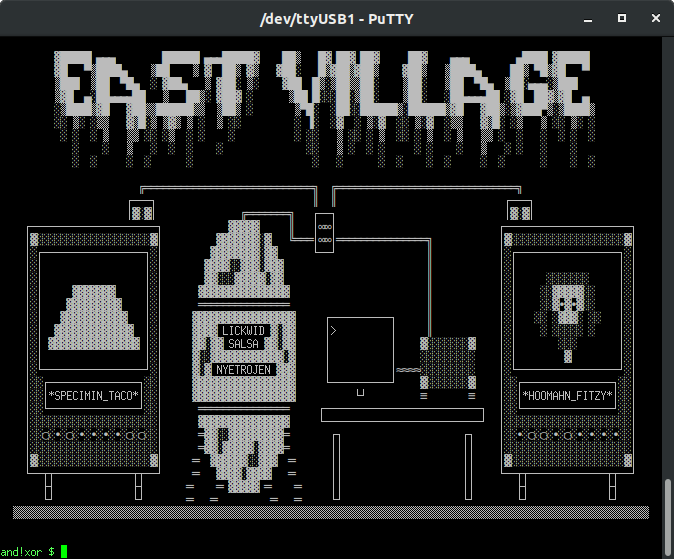
Main Puzzle
The CIRCUIT_BOARD has exposed TPM debug pinouts...and if the player has actually looked at the back of their badge... They will notice there is a TPM 1.337 for SEKURITTY; the TTY being a hint that perhaps this is all done on serial. 82 is ASCII "R" - 84 is ASCII "T" - 71 is ASCII "G" - For Tx, Rx, and GND respectively. Looking closely you can see there is a loop back net tie. This trace has to be cut with an exacto knife. Once the puzzle is complete one can solder a bridge back or put a couple male header pins with a jumper. Once the cut has been made and probes attached to the Tx, Rx, and GND lines we can proceed. In the photos below, I chose to cut the traces and solder on male header pins.
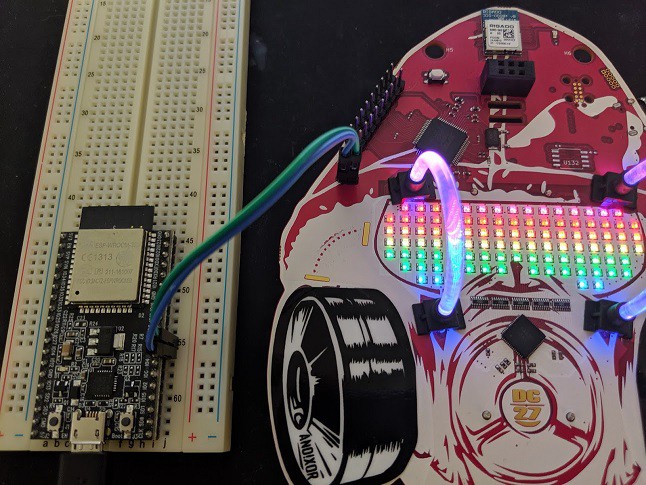

By hooking up a logic analyzer, another 3.3v debugger microcontroller (Teensy, ESP32), or FT2232, you can see the serial traffic on boot when the player hacks the reset button with their finger.
In a passive state the message across the serial line appears as follows:
TPM=1_AX3$7_
From here the player should infer that TPM=1 means encryption is enabled, " _ " is a message delimiter, and "AX3$7_" is some encrypted junk on the end. From here they should make an implant to read this serial string, change TPM=1 to TPM=0 and see what happens. The following is an Arduino sketch doing such that (note I used an ESP32 and Teensy to verify since they run on 3.3V logic, a normal Arduino Uno runs 5V logic and would require a level shifter... fuck that). Essentially this is your run of the mill Arduino serial "echo" code. Only parse the Rx input and if it is of a certain value (bounded by preexisting delimiters or conditions) change it before sending it out the Tx line.
//Board = ESP32 Dev Module
#define HWSERIAL Serial1
#define RXPIN 16 //ESP32 RX Pin on Serial1
#define TXPIN 17 //ESP32 TX Pin on Serial1
int count = 0; //For Counting how many bytes have been recieved
bool echo = false; //For toggling pass through vs MITM implant mode
int buffer[6]; //I know all message blocks are 6 characters long
void setup() {
Serial.begin(9600);
HWSERIAL.begin(9600, SERIAL_8N1, RXPIN, TXPIN);
}
void loop() {
int incomingByte; //For storing what is recieved over UART
if(echo){ //Act as a passthrough
if (HWSERIAL.available() > 0) {
incomingByte = HWSERIAL.read();
Serial.print("RX/TX: "); //So I can watch what's going on
Serial.println((char)incomingByte); //So I can watch what's going on
HWSERIAL.print((char)incomingByte); //Pass through what I saw
}
}
else{ //Act as a MITM implant
if (HWSERIAL.available() > 0) {
incomingByte = HWSERIAL.read(); //Store what was received
Serial.print("RX: ");
Serial.println((char)incomingByte);
buffer[count]=incomingByte;
count++;
if(count == 6){ //Modify the message block
//Turn off the TPM Module so nothing is encrypted
if((buffer[0]==84)&&(buffer[1]==80)&&(buffer[2]==77)&&(buffer[3]==61)&&(buffer[4]==49)&&(buffer[5]==95)){
//TPM=1_ : 84 80 77 61 49 95 / TPM=0_ : 84 80 77 61 48 95 / Enable or Disable Encryption
buffer[4]=48; //Encryption from enabled (1) to disabled (0)
}
//Send the modified message block
for(int i=0; i<6; i++){
Serial.print("TX: "); //So I can watch what's going on
Serial.println((char)buffer[i]); //So I can watch what's going on
HWSERIAL.print((char)buffer[i]); //Send the modified data
}
count = 0; //reset the counter
}
}
}
}
Once doing this we can now see the serial message, with TPM off, and the serial traffic in full flavor.
TPM=0_274=1_
So now we see the encrypted messaged means 274=1, but WTF does that mean? By typing "look at HOOMAHN_FITZY" it is explained that he drew a figure 8 on the glass. That is a hint at the ANSI art blinky lights on the cryogenic chambers are identified in Octal.

The octal under the taco translates to 274. Fitzy translates to 457. At this point the player has many implant options. Set 274=0 and thaw the taco. Set 457=0 and save Joe's life. How about 457=1? I'll save these alternate endings for the devoted player to hack and find out, for now lets free Mr. Fitz.
//Board = ESP32 Dev Module
#define HWSERIAL Serial1
#define RXPIN 16 //ESP32 RX Pin on Serial1
#define TXPIN 17 //ESP32 TX Pin on Serial1
int count = 0; //For Counting how many bytes have been received
bool echo = false; //For toggling pass through vs MITM implant mode
int buffer[6]; //I know all message blocks are 6 characters long
void setup() {
Serial.begin(9600);
HWSERIAL.begin(9600, SERIAL_8N1, RXPIN, TXPIN);
}
void loop() {
int incomingByte; //For storing what is recieved over UART
if(echo){ //Act as a passthrough
if (HWSERIAL.available() > 0) {
incomingByte = HWSERIAL.read();
Serial.print("RX/TX: "); //So I can watch what's going on
Serial.println((char)incomingByte); //So I can watch what's going on
HWSERIAL.print((char)incomingByte); //Pass through what I saw
}
}
else{ //Act as a MITM implant
if (HWSERIAL.available() > 0) {
incomingByte = HWSERIAL.read(); //Store what was recieved
Serial.print("RX: ");
Serial.println((char)incomingByte);
buffer[count]=incomingByte;
count++;
if(count == 6){ //Modify the message block
//Turn off the TPM Module so nothing is encrypted
if((buffer[0]==84)&&(buffer[1]==80)&&(buffer[2]==77)&&(buffer[3]==61)&&(buffer[4]==49)&&(buffer[5]==95)){
//TPM=1_ : 84 80 77 61 49 95 / TPM=0_ : 84 80 77 61 48 95 / Enable or Disable Encryption
buffer[4]=48; //Encryption from enabled (1) to disabled (0)
}
if((buffer[0]==50)&&(buffer[1]==55)&&(buffer[2]==52)&&(buffer[3]==61)&&(buffer[4]==49)&&(buffer[5]==95)){
//274=1_ : 50 55 52 61 49 95 / Freeze the Taco (current state, nothing happens its already frozen)
//Modify nothing - The computer resets nothing happens
/*
//274=0_ : 50 55 52 61 48 95 / Free the Taco
buffer[4]=48;
*/
/*
//457=1_ : 52 53 55 61 49 95 / Freeze the Fitz
buffer[0]=52;
buffer[1]=53;
buffer[2]=55;
//No need to change buffer[3] since it is "=" (61)
buffer[4]=49;
buffer[5]=95;
*/
//457=0_ : 52 53 55 61 48 95 / Free the Fitz (Lets do this)
buffer[0]=52;
buffer[1]=53;
buffer[2]=55;
//No need to change buffer[3] since it is "=" (61)
buffer[4]=48;
buffer[5]=95;
}
//Send the modified message block
for(int i=0; i<6; i++){
Serial.print("TX: "); //So I can watch what's going on
Serial.println((char)buffer[i]); //So I can watch what's going on
HWSERIAL.print((char)buffer[i]); //Send the modified data
}
count = 0; //reset the counter
}
}
}
}
Running this now results in the following on the serial line. Note that RX signifies what was received by the implant and TX is what our implant sent.

And the grand finale...
and!xor $ HACK RESET_BUTTON WITH FINGER The computer resets. Something happens... The HOOMAHN_FITZY pod opens and Joe is released. High fives for celebration but he doesn't want to stick around. Would you? Before he leaves he tapes up a photo of himself in the pod window to trick his captors... Why does he keep life size photos of his face? Dunno but it works out. Joe tosses a care package for your troubles on the ground and then bolts. East Village Hack: 15% Completion Earned
Finally, we can close the circuit with a jumper (to be clean about it) or solder the net tie bridge on the back of the badge which was cut. I chose the jumper. FWIW I technically did not need an extra micro-controller. I could have used the FT2232 and written a program in C or Python to do the same thing. I was lazy and re-used implant code I already had written on Arduino. Want to help me out? Post the code using the FTDI with PyFTDI library or in C, I'll buy you a beer.
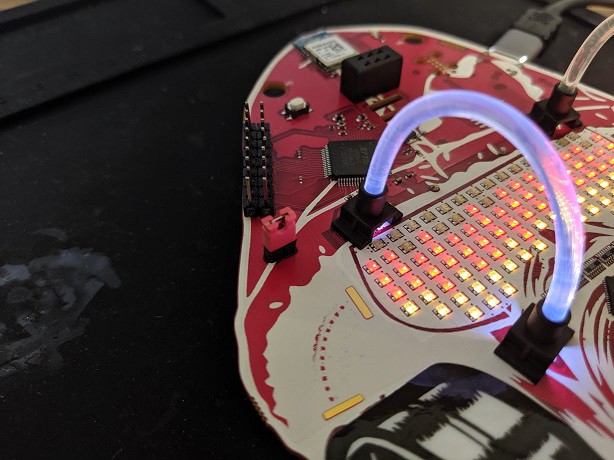
Alternatively, if you had a DOOM SAO, the same can be achieved by using the code within the custom application section. Also given the hints that the DOOM SAO can be used for Serial and I2C bus passive and active hacking... go with it! Note, when writing this I realized the spelling error in the DOOM SAO code "...appliaction()" I could do a pull request to fix it. Or I could leave it to the community to fix it. Given its Arduino code, it's expected to leave shit in the wild.
The Doom SAO Github Link: https://github.com/LonghornEngineer/DOOM_SAO
void mode_5_custom_appliaction()
{
// TODO - This section is for others to add their own code for custom functionality
if(menu_display_5)
{
SerialUSB.println("**Hardware Implant Mode**");
SerialUSB.println("Connect the source's serial TX to the SAO RX Pin PB23");
SerialUSB.println("Connect the target's serial RX to the SAO TX Pin PB22");
SerialUSB.println("Press Q to quit back to the main menu.\n");
menu_display_5 = false; //this prevents infinite printing of the menu in loop
}
//Enable Serial
if(!sao_serial_baud_selection){
SAOSERIAL.begin(9600);
sao_serial_baud_selection = true;
}
int implant_incoming_byte; //For storing what is recieved over PB23
if (SAOSERIAL.available() > 0) {
implant_incoming_byte = SAOSERIAL.read(); //Store what was recieved
SerialUSB.print("RX: ");
SerialUSB.println((char)implant_incoming_byte);
buffer[count]=implant_incoming_byte;
count++;
if(count == 6){ //Modify the message block
//Turn off the TPM Module so nothing is encrypted
if((buffer[0]==84)&&(buffer[1]==80)&&(buffer[2]==77)&&(buffer[3]==61)&&(buffer[4]==49)&&(buffer[5]==95)){
//TPM=1_ : 84 80 77 61 49 95 / TPM=0_ : 84 80 77 61 48 95 / Enable or Disable Encryption
buffer[4]=48; //Encryption from enabled (1) to disabled (0)
}
if((buffer[0]==50)&&(buffer[1]==55)&&(buffer[2]==52)&&(buffer[3]==61)&&(buffer[4]==49)&&(buffer[5]==95)){
/*
//274=1_ : 50 55 52 61 49 95 / Freeze the Taco (nothing happens)
//274=0_ : 50 55 52 61 48 95 / Free the Taco (game over)
buffer[4]=48;
//457=1_ : 52 53 55 61 49 95 / Freeze the Fitz (game over)
buffer[0]=52;
buffer[1]=53;
buffer[2]=55;
buffer[3]=61;
buffer[4]=49;
buffer[5]=95;
*/
//457=0_ : 52 53 55 61 48 95 / Free the Fitz (you win)
buffer[0]=52;
buffer[1]=53;
buffer[2]=55;
buffer[3]=61;
buffer[4]=48;
buffer[5]=95;
}
//Send the modified message block
for(int i=0; i<6; i++){
SerialUSB.print("TX: "); //So I can watch what's going on
SerialUSB.println((char)buffer[i]); //So I can watch what's going on
SAOSERIAL.print((char)buffer[i]); //Send the modified data
}
count = 0; //reset the counter
}
}
}
Easter Egg
There is a small debugging breakout on the CIRCUIT_BOARD about the size of a grain of rice.
The player needs to hack it with the GRAIN_OF_RICE they obtained in the West Village brewery.
and!xor $ HACK CIRCUIT_BOARD WITH GRAIN_OF_RICE

Easter Egg Hack: 4% Completion Earned
Slipping the tiny grain of rice on to the circuit board easily looks like a hardware implant.
Functionally...it does nothing...Might as well publish a story about it.
West Village
This challenge requires that the player reverse engineer a binary, break the hash, and hack a license file together to activate the brewery software. You are in a craft beer brewery.
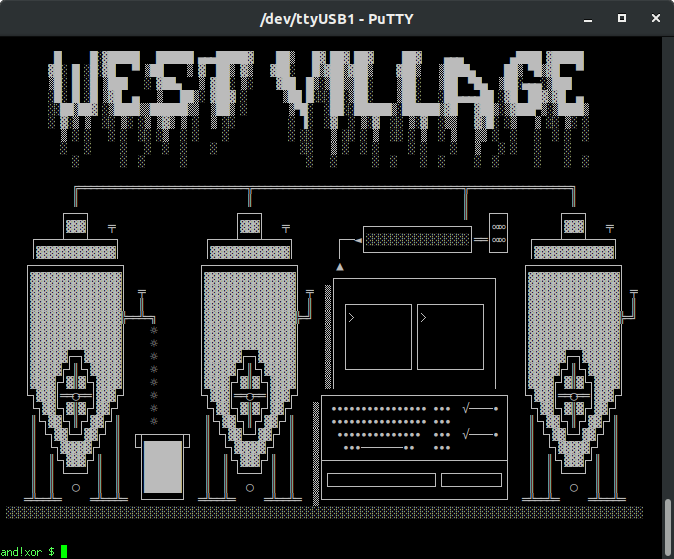
Main Puzzle
Initially the computer is offline, looking for a FLOPPY_DISK to boot from (obtained from North Village); doing this will provide easter egg points. Once bringing the computer online, the following is learned by looking at the MONITOR_1:
and!xor $ LOOK AT MONITOR_1
Looking at the first monitor, all you see is the message ACTIVATION FAILED.
You quickly pound out a pwd and check the logs to find: hbs@linux~$ /var/log/brewOS
It was sent off site somewhere, but it has a link: http://bit.ly/2HWwd7z
With that file, you could surely figure out the license key and hack the KEYBOARD with it...right?
All this brewery is making you b00ze hangry. You just want to NOM on delicious craft brew...
Going to http://bit.ly/2HWwd7z downloads a binary "brewOS - Once executing the program the following is displayed:
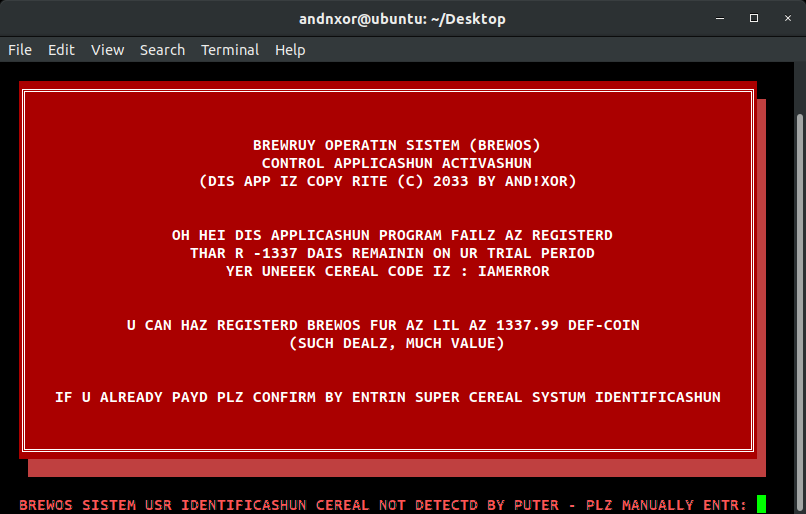
If the player read the Hackaday Manual on the system commands, they would hopefully notice the key hints of: CEREAL, SYSTUM... By looking up their unique badge serial number via the CLI they can then input that in to brewOS. The following is only applicable to Hyr0n's development badge and makes this puzzle unique per each badge as the activation code only works with a salted hash of the serial number.
and!xor $ SYSTUM CEREAL
0x29090bbdc1cf4488
Removing the "0x" we know that in this case, the unique system serial number is "29090bbdc1cf4488" Now it's time to get our hands dirty and fire up your RE tool of choice, we will use Ghidra. We wrote a very detailed post on using Ghidra with our CypherCon free badge challenge, use that for reference in setting up and running with your environment. Once the file has been loaded, lets focus on the decompiled (not disassembled) since it is pretty straight forward. Looking through the code and annotating the control flow graph, we see the following...
Essentially the program does the following
- Display splash screen & declare variables
- Get the user id as input from the user
- Generate a string using Hyr0n's handy dandy string dump obfuscation
- Concatenate the input with another string on the end
- Run an MD5 hash on the new string
- Open a hidden license file ".license_cache"
- If the contents of the license file match the salted user id, it tells you that its activated
For reference here is a copy pasta of the decompiled code to follow along with...I heart Ghidra.
undefined8 main(void)
{
int iVar1;
size_t sVar2;
long lVar3;
FILE *__stream;
undefined8 uVar4;
long in_FS_OFFSET;
int local_11c;
int local_118;
int local_114;
undefined4 local_ec;
byte local_e7 [7];
undefined8 local_e0;
undefined4 local_d8;
undefined8 local_d4;
undefined4 local_cc;
char local_c8 [48];
undefined8 local_98;
undefined8 local_90;
undefined8 local_88;
undefined8 local_80;
undefined local_78;
undefined8 local_68;
undefined8 local_60;
undefined8 local_58;
undefined8 local_50;
undefined local_48;
char local_38 [40];
long local_10;
local_10 = *(long *)(in_FS_OFFSET + 0x28);
gfx_splash();
printf(" BREWOS SISTEM USR IDENTIFICASHUN CEREAL NOT DETECTD BY PUTER - PLZ MANUALLY ENTR: ");
__isoc99_scanf(&DAT_00102095,local_c8);
local_d8 = 0;
local_e0 = 0x4b4338514b53;
local_cc = 0;
local_d4 = 0x190668010e03;
local_11c = 0;
while (local_11c < 6) {
local_e7[(long)local_11c] =
*(byte *)((long)&local_e0 + (long)local_11c) ^ *(byte *)((long)&local_d4 + (long)local_11c)
;
local_11c = local_11c + 1;
}
strcat(local_c8,(char *)local_e7);
local_98 = 0;
local_90 = 0;
local_88 = 0;
local_80 = 0;
local_78 = 0;
local_68 = 0;
local_60 = 0;
local_58 = 0;
local_50 = 0;
local_48 = 0;
sVar2 = strlen(local_c8);
lVar3 = md5(local_c8,sVar2 & 0xffffffff,sVar2 & 0xffffffff);
local_118 = 0;
while (local_118 < 4) {
local_ec = *(undefined4 *)(lVar3 + (long)local_118 * 4);
local_114 = 0;
while (local_114 < 4) {
sprintf((char *)&local_68,"%02x",(ulong)*(byte *)((long)&local_ec + (long)local_114));
strcat((char *)&local_98,(char *)&local_68);
local_114 = local_114 + 1;
}
local_118 = local_118 + 1;
}
__stream = fopen(".license_cache","r");
if (__stream == (FILE *)0x0) {
puts(" ERROR: LICENSE NOT FINDZ");
uVar4 = 1;
}
else {
fgets(local_38,0x21,__stream);
fclose(__stream);
iVar1 = strcmp((char *)&local_98,local_38);
if (iVar1 == 0) {
puts(" SUCCES: LICENSE VALID - UR BREW SISTEM SHALL NAO BE ACTIVD.");
puts(
" ERROR: BREW SISTEM PERIFERALS NOT FINDZ - R U RUNNIN DIS SOFTWARE ON TEH RITESISTEM?\n"
);
}
else {
puts(" ERROR: INVALID LICENSE\n");
}
printf("\x1b[0m");
uVar4 = 0;
}
if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) {
/* WARNING: Subroutine does not return */
__stack_chk_fail();
}
return uVar4;
}
So let's dig into how you actually look at decompiled code and figure this out (jump to function MAIN). You may see variable names change because as you figure out roughly what variables are used for, you should ALWAYS CHANGE THEIR NAME TO MAKE SENSE OF IT ALL. ALWAYS. DO THIS. Or don's.
1. Display splash screen & declare variables
2. Get the user id as input from the user
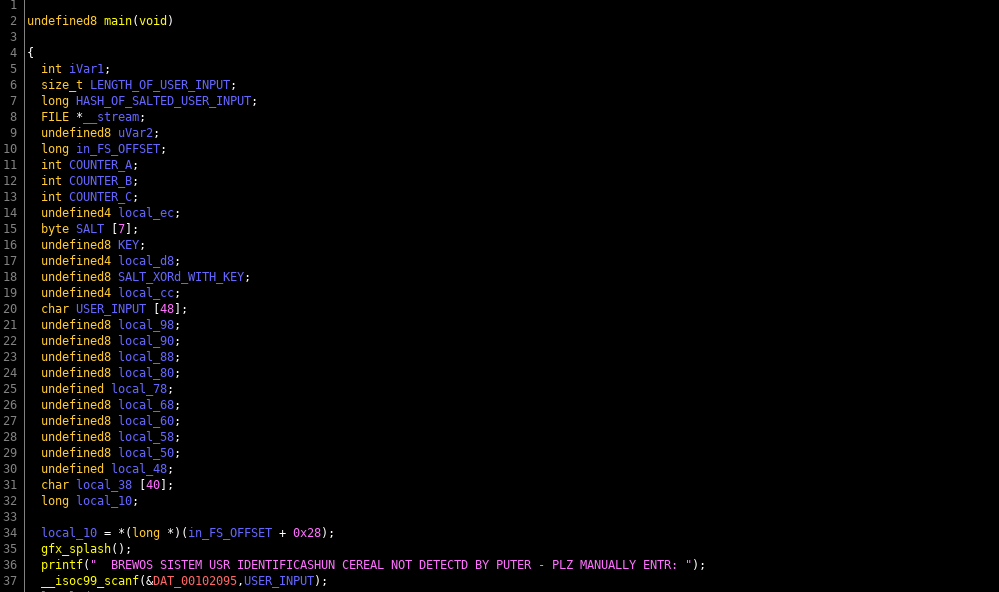
This is pretty straight forward, if you've every programmed, there's not much to explain here. And if you've never programmed in C or C++... RE of binaries is going to be drinking from a fire hose. Learn the basics of software synthesis, before you jump into software analysis.
3. Generate a string using Hyr0n's handy dandy string dump obfuscation
4. Concatenate the input with another string on the end
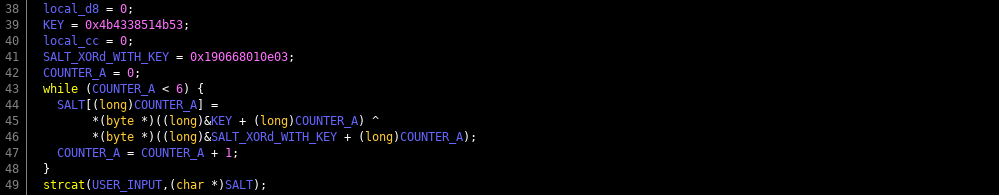
Again if you read the earlier post you know I'm against cheap tricks like running string dumps on a binary. Its super useful, just not for our puzzles really. The basics are like this, instead of having a hidden key as a string, create an array of numbers of your key in ASCII. Then XOR it out of band and make a second "encrypted" message, repeat and change it to ASCII integer values. Then when you need your private key in code all you have to do is XOR ^ the cell of both arrays with one another, and it will decode the message. This is not real encryption, its a cheap obfuscation technique to thwart string dumps. In general you should never put a private key in code. But this is a puzzle, so its okay. So why are we taking this an concatenating it on the end of the user input...it's salt. Always salt your hashes. Only what's super interesting here is compiler optimization. You would have thought that my two arrays would also be arrays in the code. We'll the compiler was like "fuck that" and converted them in to two QWORDS (64 bit unsigned integers) and their values are shown in hex. Be careful, because when you go from integer arrays (which are easy for people to read) into QWORDS (which are easy for computers to read), endianness comes in to play. Specifically little endianness. Seeing as this is denoted with hex, use a quick online HEX XOR tool and see what happens.
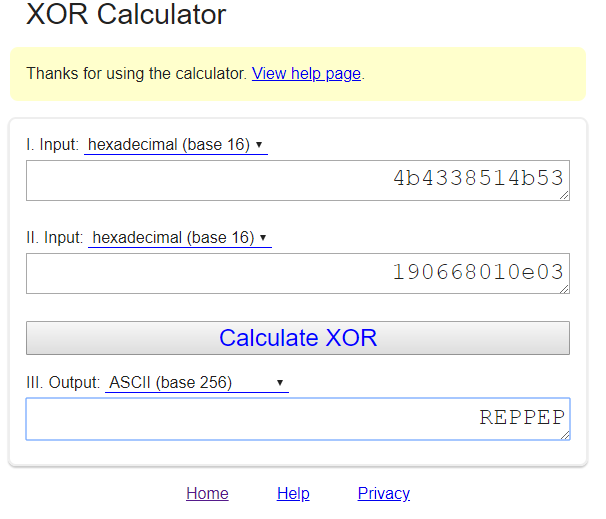
Since it was converted to little endian, displaying the XOR result in ASCII looks backwards, the message I intended we use as hash salt is "PEPPER" (I'm a god damn riot).
5. Run an MD5 hash on the new string
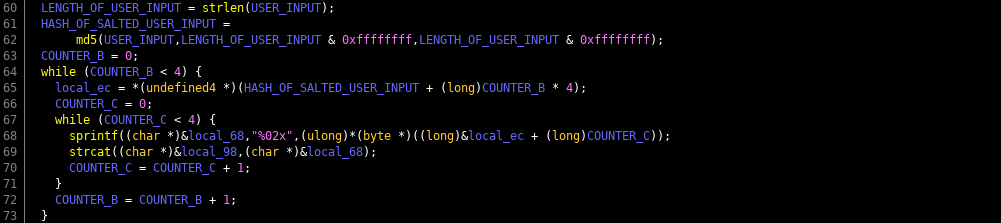
I left debug symbols on so you could see the name of the function was md5. This should really clue you in on, to understand how it's working do some quick homework. But essentially I concatenated the salt "PEPPER" on to the end of the user input of their system serial number. This gets hashed that way a person can't simply just run an MD5 cracker on the hash. However by RE-ing the code, now that you know its an MD5 hash with PEPPER concatenated on the end...are we getting warm? Use an online MD5 hash generator and just add PEPPER on the end of the serial id you obtained.
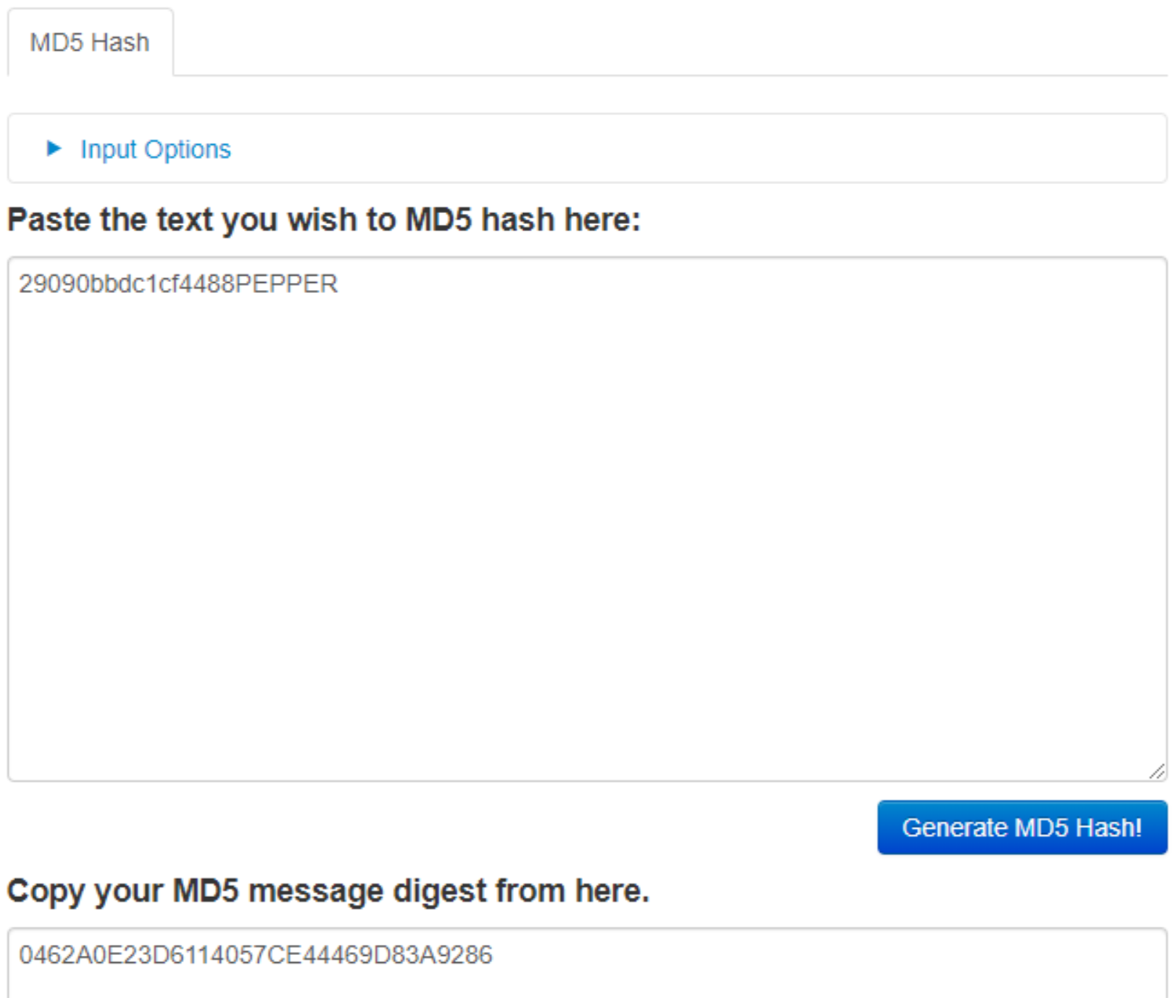
6. Open a hidden license file ".license_cache"
7. If the contents of the license file match the salted user id, it tells you that its activated
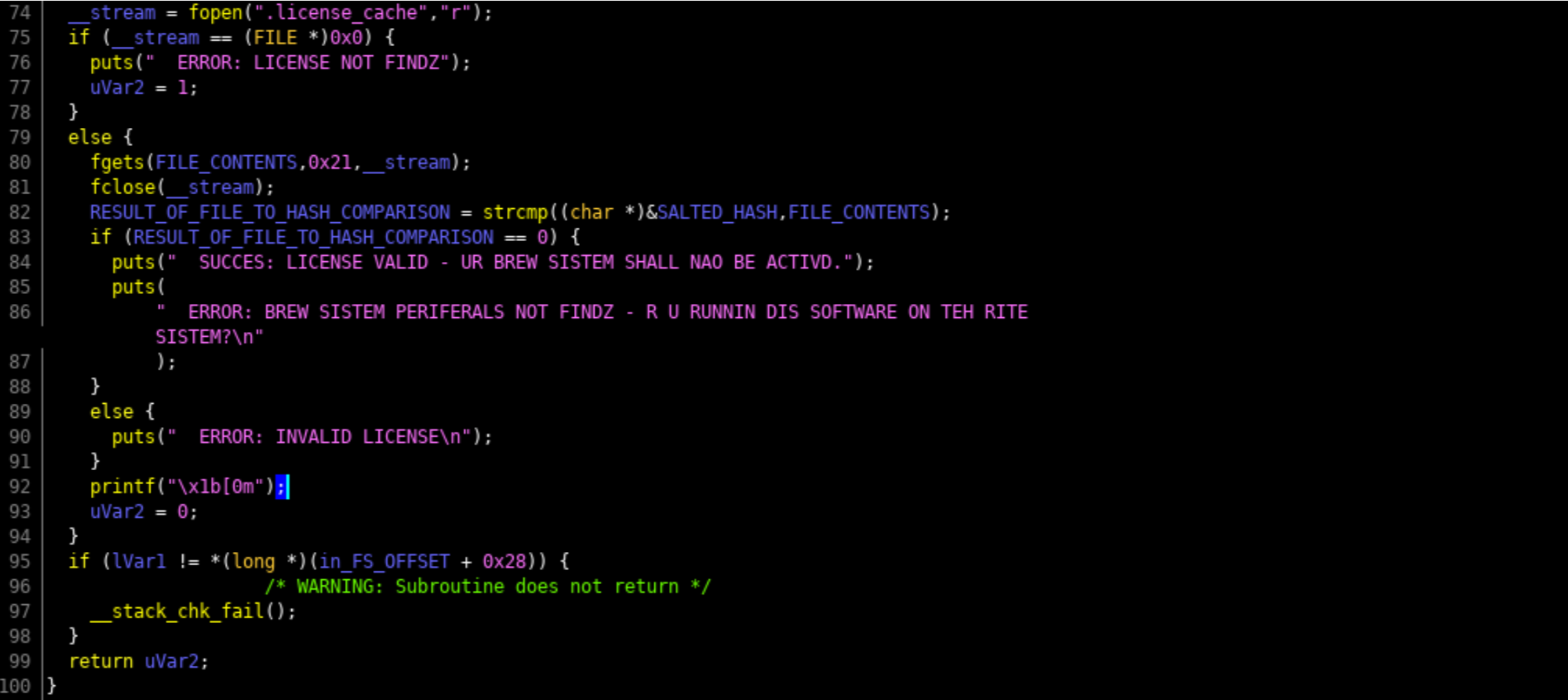
So now you have figure out all of the information. Create a license file and put the contents of your salted serial id in it and run brewOS to confirm that it is correct. However we are running this software on our own computer, not on the brewery computer. Now that you know you have the right activation code, go back in to the badge CLI and hack the keyboard with it. Side note, AWESUM uses the same salted (PEPPER) MD5 logic as the brewOS; by running AWESUM 29090bbdc1cf4488, resulting in a hash of 0462a0e23d6114057ce44469d83a9286. Now why wouldn't you just hammer away trying in the badge instead of safely on your computer? Because you get 3 attempts then I format the badge. DFIU!
and!xor $ hack KEYBOARD with 0462a0e23d6114057ce44469d83a9286 License Accepted! The brewery comes to life and the DRAWER slides open with a little reward as well. West Village Hack: 15% Completion Earned
Easter Egg
This easter egg is freebie points as you can not complete the main puzzle without hacking the floppy drive with the floppy disk first.
and!xor $ hack FLOPPY_DRIVE with FLOPPY_DISK

Easter Egg Hack: 4% Completion Earned The console begins to boot from the FLOPPY_DISK and MONITOR_1 comes to life.
Home Village
This challenge requires that the player have completed all other challenges, collected all items and beers, and drinks to produce a BAC of 0.1337
Main Puzzle
Yes this is a rehash of the DC26 final puzzle, but we love it so much. Collect the beers, drink from all of them, and based on your weight and gender determination... get your BAC to 0.1337. Looking at SOMETHING_FAMILIAR shows a drinking bending robot who father time has not treated well. Your items will help restore him to his former glory. Then you can drink and blow...his breathalyzer. The ABV of each beer is not known, you must use the information superhighway to figure this out.
and!xor $ look at SOMETHING_FAMILIAR Intuition takes over, you quickly douse him with STAR_SAN and the alkaline dissolves. Next you open his locked belly casing with a LOCK_PICK, leveraging the PAPER_CLIP as a tension bar. You pull out his internal 10ft USB cable and bring it to the DJ_COMPUTER for power... But you're not that dumb. NO! Why trust DJ Dead's computer? Always use protection, which is why that USB_CONDOM does just the trick for safe power. The robot comes back to life, extends his BREATHALYZER, and projects instructions on the wall: TO PROCEED YOU MUST ABIDE BY THE FOLLOWING RULES: * HAVE A BLOOD ALCOHOL LEVEL OF EXACTLY 0.1337, ACCURATE TO 4 DECIMAL PLACES * DRINK FROM ALL FIVE CRAFT BEERS COLLECTED * % BAC = ((A x 5.14) \ (W x R)) – 0.015 x H * A = TOTAL LIQUID OUNCES OF ALCOHOL CONSUMED = ABV * VOLUME OF ALCOHOL DRANK * W = PERSONS WEIGHT IN POUNDS * R = GENDER CONSTANT OF ALCOHOL DISTRIBUTION (0.73 FOR MALE, 0.66 FOR FEMALE, 0.695 FOR NON-BINARY) * H = HOURS ELAPSED SINCE YOUR FIRST DRINK (HOPE YOU DIDNT START THE PARTY EARLY) * CLI = hack BREATHALYZER with BREATH
It is best to do this math with a spreadsheet...
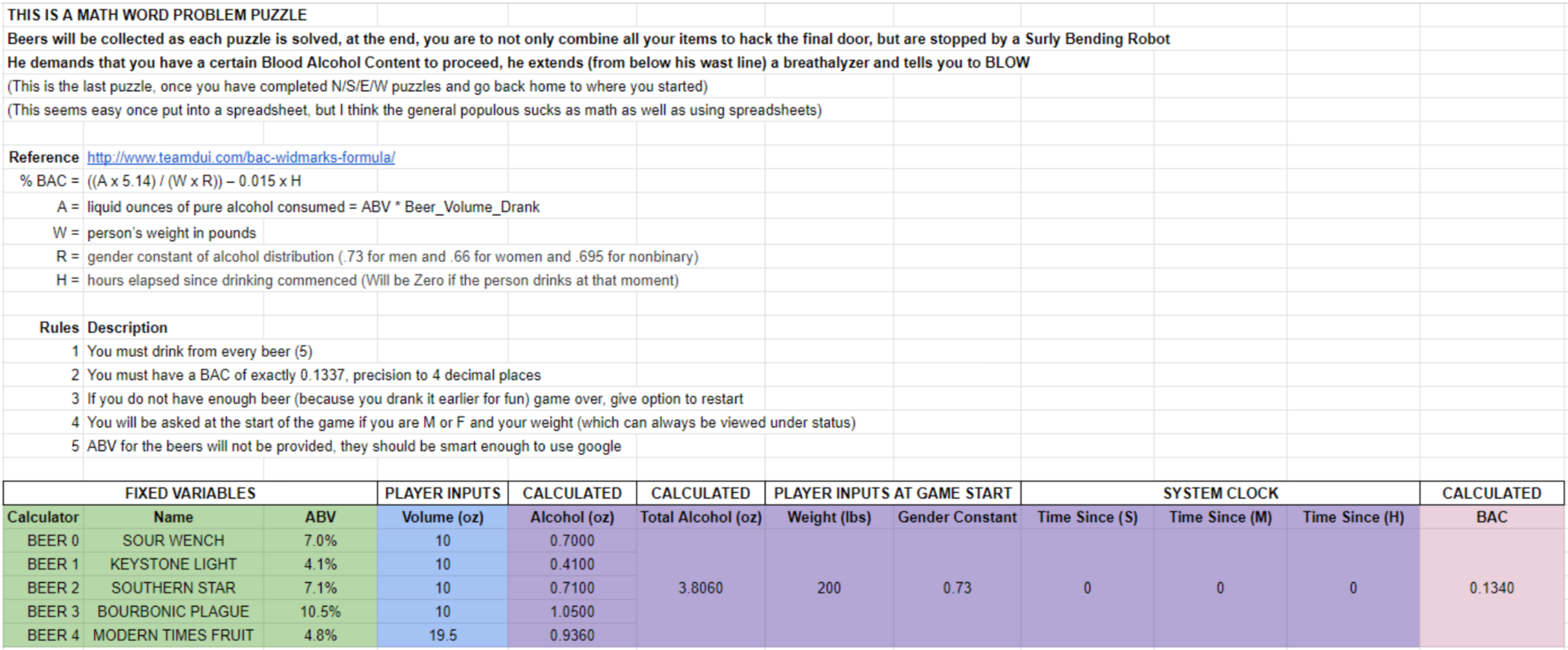
and!xor $ drink BALLAST_POINT_SOUR_WENCH 10 You down some delicious craft b33r Your BAC is now 0.0246 and!xor $ drink KEYSTONE_LIGHT 10 You down some delicious craft b33r Your BAC is now 0.0390 and!xor $ drink SOUTHERN_STAR_CONSPIRACY_THEORY 10 You down some delicious craft b33r Your BAC is now 0.0639 and!xor $ drink CASCADE_BOURBONIC_PLAGUE_2016 10 You down some delicious craft b33r Your BAC is now 0.1008 and!xor $ drink MODERN_TIMES_FRUITLANDS 19.5 You down some delicious craft b33r Your BAC is now 0.1329 and!xor $ drink MODERN_TIMES_FRUITLANDS 1 You down some delicious craft b33r Your BAC is now 0.1345 and!xor $ hack BREATHALYZER with BREATH Your BAC is 0.1343 If its too low, keep drinking... If its too high, wait it out... Regardless, you suck at this game! and!xor $ hack BREATHALYZER with BREATH Your BAC is 0.1341 If its too low, keep drinking... If its too high, wait it out... Regardless, you suck at this game!
As you can see, even I drank a little too much. Just gotta wait it out since the badge uses a real time clock to degrade your blood alcohol content in real time, as it actually would be metabolized in the meat space. But eventually I blew just right.
and!xor $ hack BREATHALYZER with BREATH

YOUR BREATH...YOUR STANKY ASS BREATH...HAS A BAC IS 1.337 AND THE FINAL CHALLENGE IS SOLVED. A BRIGHT LIGHT BEAMS FROM THE NIGHT SKY, SOMETHING DARTING ACROSS VERY QUICKLY. THE RADIO TOWER IS NOW BATHED IN BLINDING LIGHT AND YOU CANT SEE. TO BE CONTINUED... YOU HAVE COMPLETED THE AND!XOR DC27 BADGE CHALLENGE. TYPE BENDER STATUS AND SCREENSHOT IT. CONTACT US ON TWITTER @ANDNXOR && EMAIL HYR0N@ANDNXOR.COM ASAP BEFORE THE CON IS OVER. YOUR STATE WILL SAVE ON A TASK THAT RUNS EVERY DAY, YOU MAY SAFELY DISCONNECT THE BADGE IN 24 HOURS... Home Village Hack: 15% Completion Earned
No, the badge actually saves your state instantly, not in 24 hours. I'm just a dick. Oh yeah if you type "bender status" you'll notice that completing everything results in a completion of 95%. I'm a dick. ¯_(ツ)_/¯
Easter Egg
There is an inception type easter egg, where one has to keep digging to find out the last of the last eggs. Start with the STICKY_NOTE...
and!xor $ look You enter the doorway and it opens to a dusty radio broadcast room. Lets call this HOME for now... A relic of the past, but nostalgia holds a place in your heart. There's a DJ_COMPUTER on a desk, powered up, with a prompt. A pile of mixtapes, discs, and a STICKY_NOTE on a piece of media are in the corner. You peer out the window and to your surprise the world has gone to shit. Like nuclear winter fallout shit. They did it. They finally did it. DEF CON was cancelled and look what happened. From this radio tower lookout you can see two intersecting roads going in to the city. They are perpendicular creating four possible directions: NORTH, SOUTH, EAST, and WEST. Looking back away from the window and back in the room you notice something SOMETHING_FAMILIAR... An item catches your eye for the taking: BOTTLE_OPENER You smell some booze for the drinking: BALLAST_POINT_SOUR_WENCH and!xor $ look at STICKY_NOTE A reminder from a DJ Dead to throw together a MIXTAPE. and!xor $ look at MIXTAPE It's hard to read, the LABEL is very faded. and!xor $ look at LABEL Almost half peeled off but you can see some ENGRAVING from what was written. and!xor $ look at ENGRAVING Tilted in the light the engraving shows http://bit.ly/2HB1Ggg Easter Egg Hack: 4% Completion Earned
One may give up at this point but there is obviously an URL to follow...yeah we Rick Rolled you. But did we JUST Rick Roll you or is there more to it? At about 10 seconds there's some strange noises. Sounds like some Audio Steganography. If you looked at the DJ_COMPUTER it asks that you enter an UNLOCK_CODE. All unlock codes released on Twitter and elsewhere are entered at HOME via "hack DJ_COMPUTER with XXXXXX" So lets unravel this mystery... Analyzing wave forms is best done with an initial look with a spectrogram view.
andnxor@ubuntu:~$ sudo apt-get install sonic-visualiser
Open the new mp3 file, however the image will not be visible in the default view. Press Alt+G to add the Spectrogram layer. Drag left/right to pan.
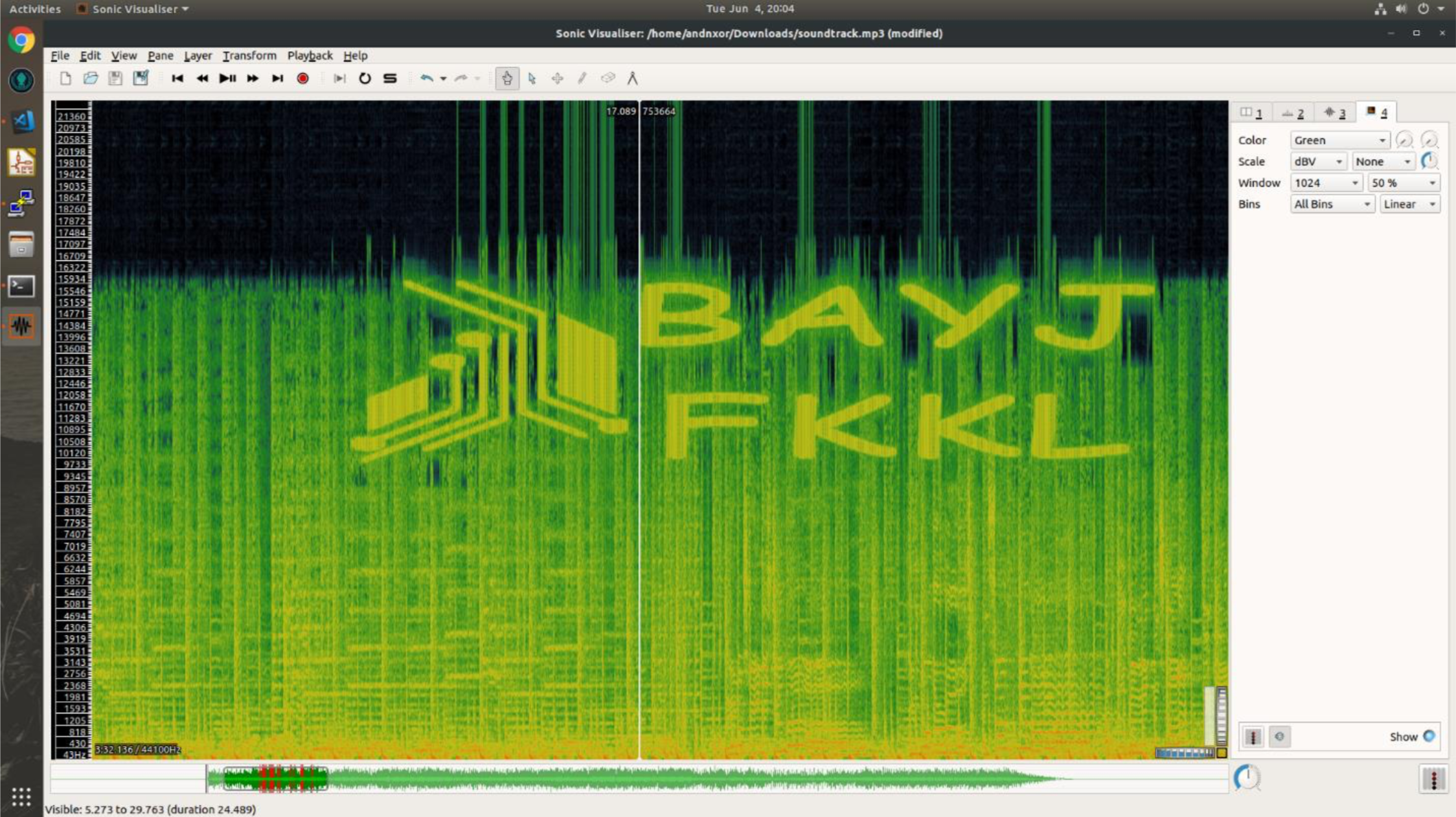
Now that you have the unlock code...
and!xor $ hack DJ_COMPUTER with BAYJFKKL
THATS IT! SEE YOU AT DC28! KTHXBYE!
 Hyr0n
Hyr0n
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.