DEF CON was finally canceled due to a pandemic... but that doesn't mean we can't still make a badge and ship drops all around the country for proxy haXors to give them away for free :) This year's badge provides bling, an embedded yet socially distant and inclusive CTF text-based adventure (i.e. if you dont collaborate in Slack you LOSE), and a port of MyBASIC extended to the hardware to make it hackable.
This wouldn't have been possible without our Philanthropist Backers and Generous Sponsors. Show them some love because without them, you hackers wouldn't be getting badges and instead would have to resort to the pool party on the roof:
Project will be open sourced sometime in September.
Links
CTF Public Slack Workspace: https://bit.ly/3eRTR4B
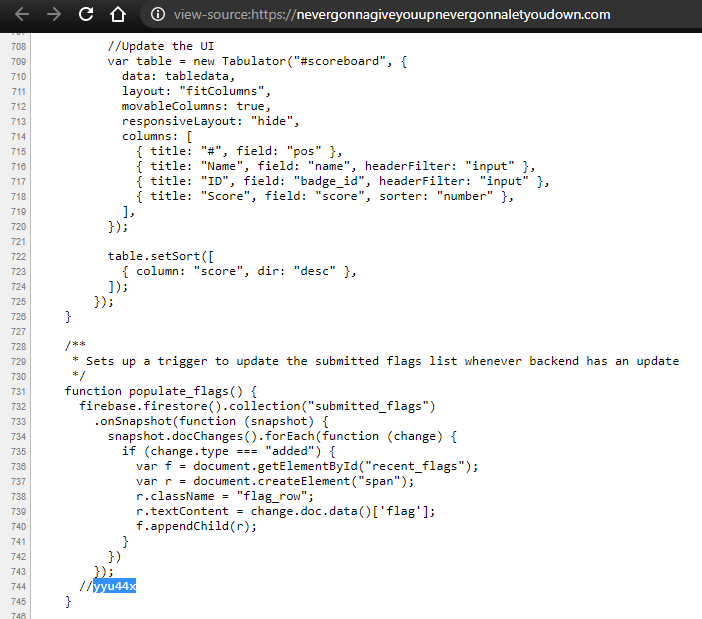
CTF Scoreboard: https://nevergonnagiveyouupnevergonnaletyoudown.com/
Trailer: https://www.youtube.com/watch?v=dY_oJL28QOw&feature=emb_title
T-Shirt: https://www.amazon.com/dp/B08CBSCJH3
 Zapp
Zapp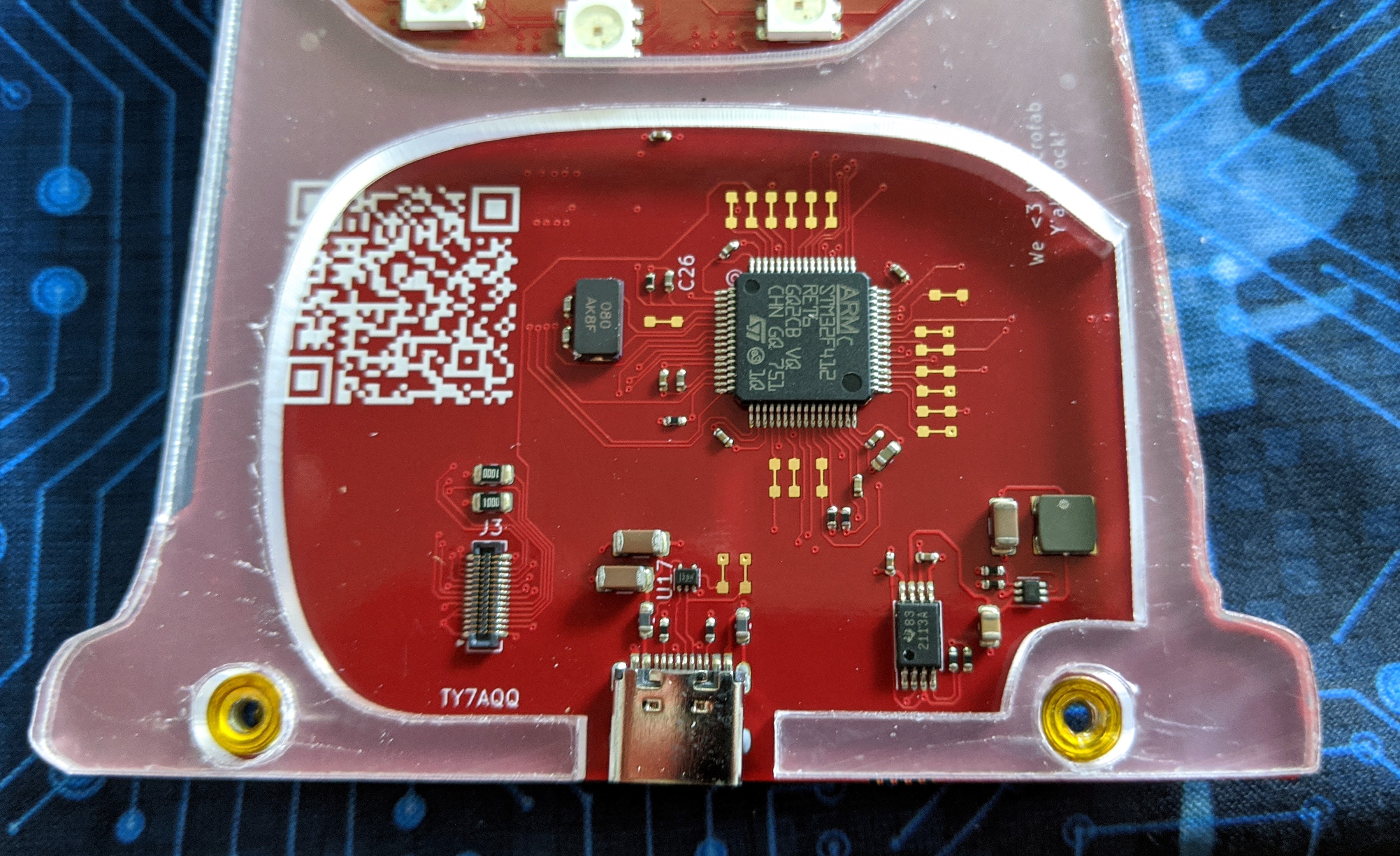




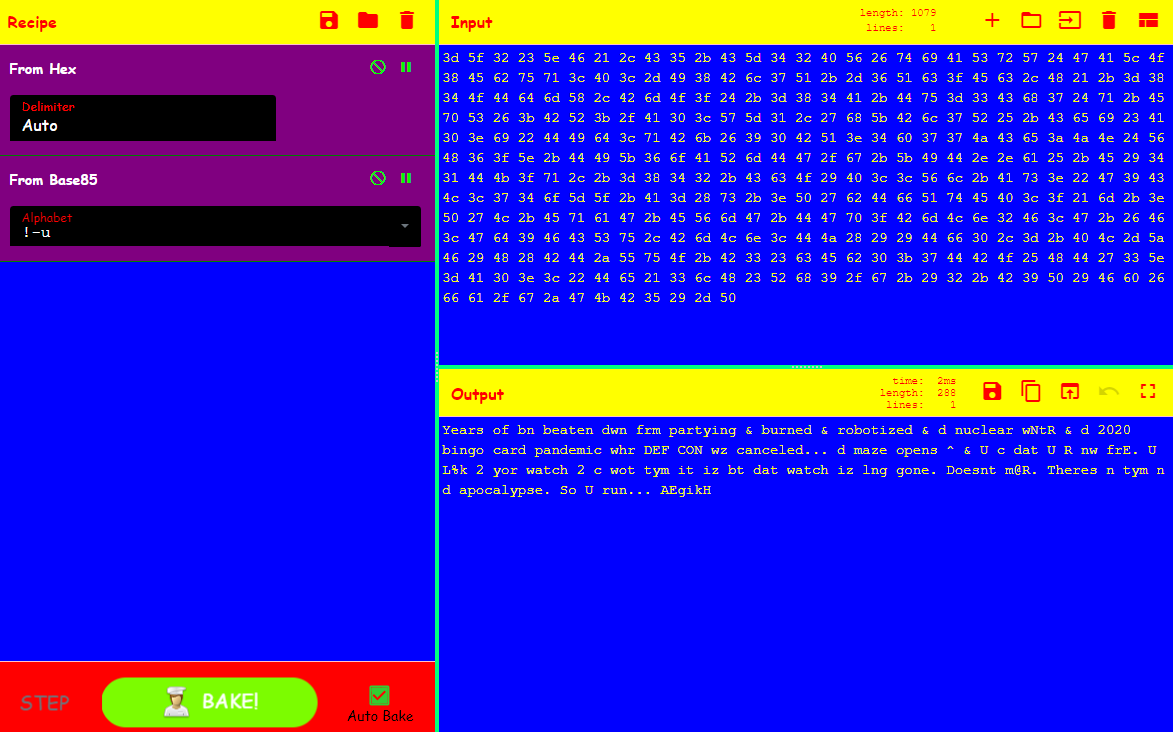
 Super Serial? Think about the least and most significant things? C'mon what better hints could we have given you? Now if you've never worked with serial a quick google on how the protocol works will teach you that charachters are turned into binary, it pads a 0 as the start bit, it INVERTS the LSB/MSB order (so its received correctly), then the end is appended with a 1 as the stop bit. The blink pattern shown would translate to...
Super Serial? Think about the least and most significant things? C'mon what better hints could we have given you? Now if you've never worked with serial a quick google on how the protocol works will teach you that charachters are turned into binary, it pads a 0 as the start bit, it INVERTS the LSB/MSB order (so its received correctly), then the end is appended with a 1 as the stop bit. The blink pattern shown would translate to...
 Jonathan Singer
Jonathan Singer

 Arya
Arya