What are the Lulz Quizzes?
These are small point value Q&A. If you get it right +5, if you get it wrong -10. How do you dig out of that hole? Well different flags are provided if you got it "right" vs "wrong." So you reset the badge, re-randomize the CTF, go find them again...grind grind grind... and you can mitigate -10 to -5 worst case. Come out +5 points for each, best case. Some complained that our results for the lulz were subjective. This is hardly the case, because we are right and you are wrong :)
LULZ QUIZ 0
~LULZ QUIZ~ (0)EMACS (1)VIM (2)NANO
Flag: hack flag wit 1
What Did You Learn Today: VIM DUH!
LULZ QUIZ 1
~LULZ QUIZ~ Did Carole Baskin kill her OM? (0)Yes (1)No
Flag: hack flag wit 0
What Did You Learn Today: Carole Fucking Baskin
LULZ QUIZ 2
~LULZ QUIZ~ Pineapple on pizza? (0)Yes (1)No
Flag: hack flag wit 0
What Did You Learn Today: Its the best kind of pizza
LULZ QUIZ 3
~LULZ QUIZ~ (0)OSX (1)Windows (2)Linux (3)BSD
Flag: hack flag wit 2
What Did You Learn Today: Linux > Windows > OSX > Dumpster Fire > BSD
LULZ QUIZ 4
~LULZ QUIZ~ (0)Red Team (1)Blu Team (2)Purpl Team
Flag: hack flag wit 2
What Did You Learn Today: Your assessments don't mean shit unless you work together to fix it.
LULZ QUIZ 5
~LULZ QUIZ~ (0)Spaces (1)Tabs
Flag: hack flag wit 1
What Did You Learn Today: Finally this debate has been settled once and for all
LULZ QUIZ 6
~LULZ QUIZ~ (0)Drop 0-Day (1)Notify Vendor
Flag: hack flag wit 1
What Did You Learn Today: Responsible disclosure
LULZ QUIZ 7
~LULZ QUIZ~ (0)Hack (1)Slp (2)Et (3)showR
Flag: hack flag wit 3
What Did You Learn Today: Yeah. Shower. For the good of everyone.
LULZ QUIZ 8
~LULZ QUIZ~ (0)tst n devlpmnt (1)tst n production (2)dun tst
Flag: hack flag wit 2
What Did You Learn Today: YOLOSEC
LULZ QUIZ 9
~LULZ QUIZ~ (0)Buffer Underflow (1)Buffer Overflow
Flag: hack flag wit -1
What Did You Learn Today: LOLOLOLOLOLOLOLOL
COMPLETION 100%
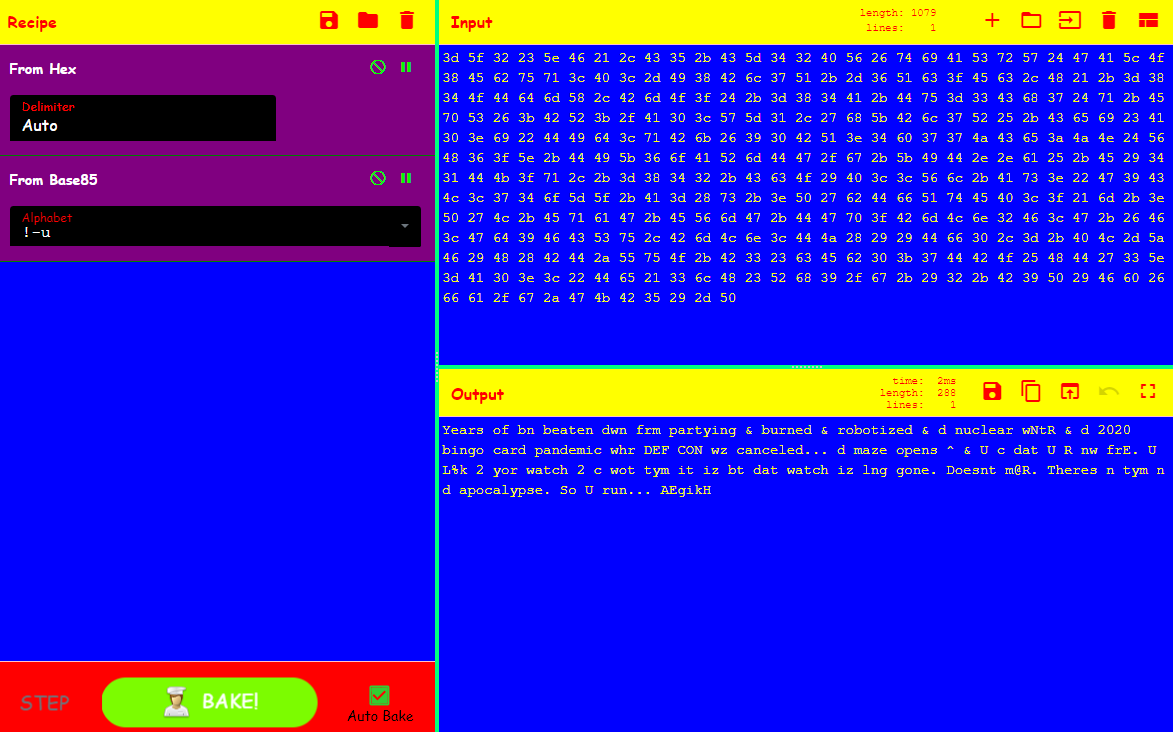
3d 5f 32 23 5e 46 21 2c 43 35 2b 43 5d 34 32 40 56 26 74 69 41 53 72 57 24 47 41 5c 4f 38 45 62 75 71 3c 40 3c 2d 49 38 42 6c 37 51 2b 2d 36 51 63 3f 45 63 2c 48 21 2b 3d 38 34 4f 44 64 6d 58 2c 42 6d 4f 3f 24 2b 3d 38 34 41 2b 44 75 3d 33 43 68 37 24 71 2b 45 70 53 26 3b 42 52 3b 2f 41 30 3c 57 5d 31 2c 27 68 5b 42 6c 37 52 25 2b 43 65 69 23 41 30 3e 69 22 44 49 64 3c 71 42 6b 26 39 30 42 51 3e 34 60 37 37 4a 43 65 3a 4a 4e 24 56 48 36 3f 5e 2b 44 49 5b 36 6f 41 52 6d 44 47 2f 67 2b 5b 49 44 2e 2e 61 25 2b 45 29 34 31 44 4b 3f 71 2c 2b 3d 38 34 32 2b 43 63 4f 29 40 3c 3c 56 6c 2b 41 73 3e 22 47 39 43 4c 3c 37 34 6f 5d 5f 2b 41 3d 28 73 2b 3e 50 27 62 44 66 51 74 45 40 3c 3f 21 6d 2b 3e 50 27 4c 2b 45 71 61 47 2b 45 56 6d 47 2b 44 47 70 3f 42 6d 4c 6e 32 46 3c 47 2b 26 46 3c 47 64 39 46 43 53 75 2c 42 6d 4c 6e 3c 44 4a 28 29 29 44 66 30 2c 3d 2b 40 4c 2d 5a 46 29 48 28 42 44 2a 55 75 4f 2b 42 33 23 63 45 62 30 3b 37 44 42 4f 25 48 44 27 33 5e 3d 41 30 3e 3c 22 44 65 21 33 6c 48 23 52 68 39 2f 67 2b 29 32 2b 42 39 50 29 46 60 26 66 61 2f 67 2a 47 4b 42 35 29 2d 50
When your completion is at 100% (All Main & Lulz Challenges) a bit.ly/2Aw1s9C link appears.
HEX -> BASE85
BONUS CHALLENGES & EASTER EGGS
DEF CON MUD Bonus Challenge
EvilMog was quite a sport and we collaborated a bit between BENDERPISS and the MUD. If you head to the mog.ninja and follow instructs, you can play the DEF CON MUD which is amazing. BENDER draws a lot of its roots from text based adventures and MUDs.
The flag is simple, yet difficult. Head to the woods in the north where you have a quest to hunt animals in the woodland maze. There you will find... hyr0n the gerbil!
"A small light brown furry gerbil. He has a white tummy, and very sharp claws. He is very cute, and quite friendly but scared of strangers. He will probably run from you if you come near him."
Don't fight him, he'll kick your ass! Just look and you will see a flag tied to him. Oh, and he's kinda quick and only remains in a each sector for 1 second. Act quickly...
Slackbot Bonus Challenge
Did you notice some other words were triggering that asshole Slackbot?
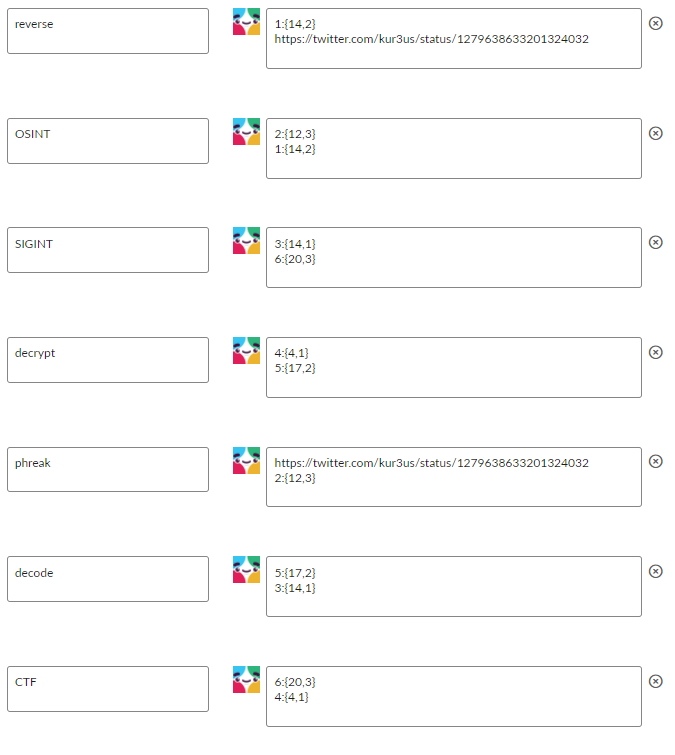
What do these have in common? They are all hacking words...they are related to the challenges on the badge...AND most of these are all in the same paragraph in the RTFM.
Each trigger word would randomly print one of two responses.
If you were lucky enough to see all the responses and put them in order, you'd have this list:
https://twitter.com/kur3us/status/1279638633201324032
1:{14,2}
2:{12,3}
3:{14,1}
4:{4,1}
5:{17,2}
6:{20,3}
If you go to that tweet, there are 3 rows of 20 characters.
Take the first clue...1:{14,2}. Go to the 14th column and the 2nd row, and you have a j.
For the second clue...2:{12,3}, go to the 12th column and 3rd row, where you'll find a p.
Continuing in this fashion, you'll get the complete 6 letter flag: jpK99x Enter this into the badge decoder for a scoreboard flag!
Taco Corp Support Line
Did you like the phone system setup by Penguin?
Alethe and Ryan put A LOT of effort in to keeping everyone entertained and navigating the call server.
There were 2 Main Challenges from the badge (Ext 4177 & 2323) and a Bonus Challenge (Ext 1337).
The easter eggs...are still for you to find, as there are a total of 27 other extensions for your enjoyment...
LayerOne Challenge
DG & JK were kind enough to put together a challenge we would expect, since they are bonified MFPs.

The following is a copy / paste from the walkthrough sent to us from DG, slight edits have been made to make it read properly as a HaD writeup...
Info not for public release / solution walkthrough:
Hyr0n I dream of combing your beard and talking about binary RE over rootbeers.
This challenge is a mixture of file format shenanigans, esoteric programming languages, and reverse engineering. If you had to give it a single category it should probably be "Reverse Engineering", but "Misc" would also be reasonable. I would rank this as a Hard challenge.
Challenge starts with a PNG file promoting LayerOne. Cause we're mad shady like that. There's some easter eggs and red herrings hidden in the PNG itself for folks that try to go down the stego/image metadata route, but what anyone with PNG experience should see is that the file is bigger than it should be for the size of image defined. This could be because we modified the PNG header to not display the full image, but that's not the case (can be verified by basic math on the PNG data stream). PNG is a chunk format that allows anything after the PNG to be appended to the file and ignored by PNG parsers(similar to "slack space" in traditional disk/filesystem forensics). A naive look through strings/etc data would show normal PNG things, but if you look closely its duplicated; there are two PNGs within the one file. This can be carved out manually or using and file carving tool like binwalk, scalpel, foremost, etc.
The second file is a valid PNG with no discernible starting points based on image metadata / similar things to image 1. As before, there is no stego, watermarking, or anything like that - but there are some more red herrings and easter eggs in these places to annoy and or amuse people. Looking at the image itself, its got a variety pixels in a variety of colors around the edges; looks like static or random colors. This could be some complex data formatting, but it is instead a programming language called Piet. Piet works by having a direction pointer (an arrow) and the color transitions between pixels or blocks of pixels defines the operations that should happen. There's some rules behind this but the end result is things like "no change in hue, but +1 change in darkness == PUSH instruction". Sounds pretty weird but it's a pretty well-known language as far as esoteric languages go - not quite Brainfuck but up there in our opinion. There's no big challenge here other than identifying that it is Piet and running it in a Piet interpreter (we thought the rest of the challenge was enough RE to go around). Running the second file through a Piet interpreter will produce a binary data blob. There's quite a few Piet interpreters online, but we used the main one, npiet, for verifying things worked.
It should be pretty obvious that the output of the Piet code is a x86_64 ELF executable file. From here it can be executed, run through IDA/Ghidra/whatever. There are some anti-decompilation, anti-disassembly, and anti-debugging features that should make it a little more complicated than running Decompile in Ghidra to see what the flag should be. The gist of this problem is that the executable wants to validate input in a variety of ways (e.g. not a single password entry) to verify they solved it and can have the flag - all of which should require a bit of reversing to understand. The requirements to get the flag are:
1. argv[0] must be a specific value ('L'). Rename the binary OR harness the binary with Python/whatever to modify argv.
2. argv[1] must be a specific value('m'). Supply it on the command line / harness on execution.
3. The environment variable ('the third letter') must be a specific value ('d'). Supply it on the command line / harness on execution.
4. A single character can be entered as a "Enter the flag: " on execution; it must be a specific value ('3').
5. The binary itself must be modified so that a specific NOTE segment of type (0x420) name ('flg\x00') and desc ('second char = 1') is present. This can be done with a hex editor.
6. The command line used to run the program must be a specific value ('../../thelastcharacteris/0'). This is distinct from argv[0].
This sounds extremely complicated, but all of it can be bypassed in a debugger - only non-debugger methods are noted above. The issue there is that they might skip some code that sets the flag properly, resulting in an incorrect flag printed at the end. This should be fun for you when they are complaining their flags don't work.
Assuming all steps were followed properly the flag 'L1d3m0' is printed out with a message saying it's the correct flag.
 Hyr0n
Hyr0n
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.