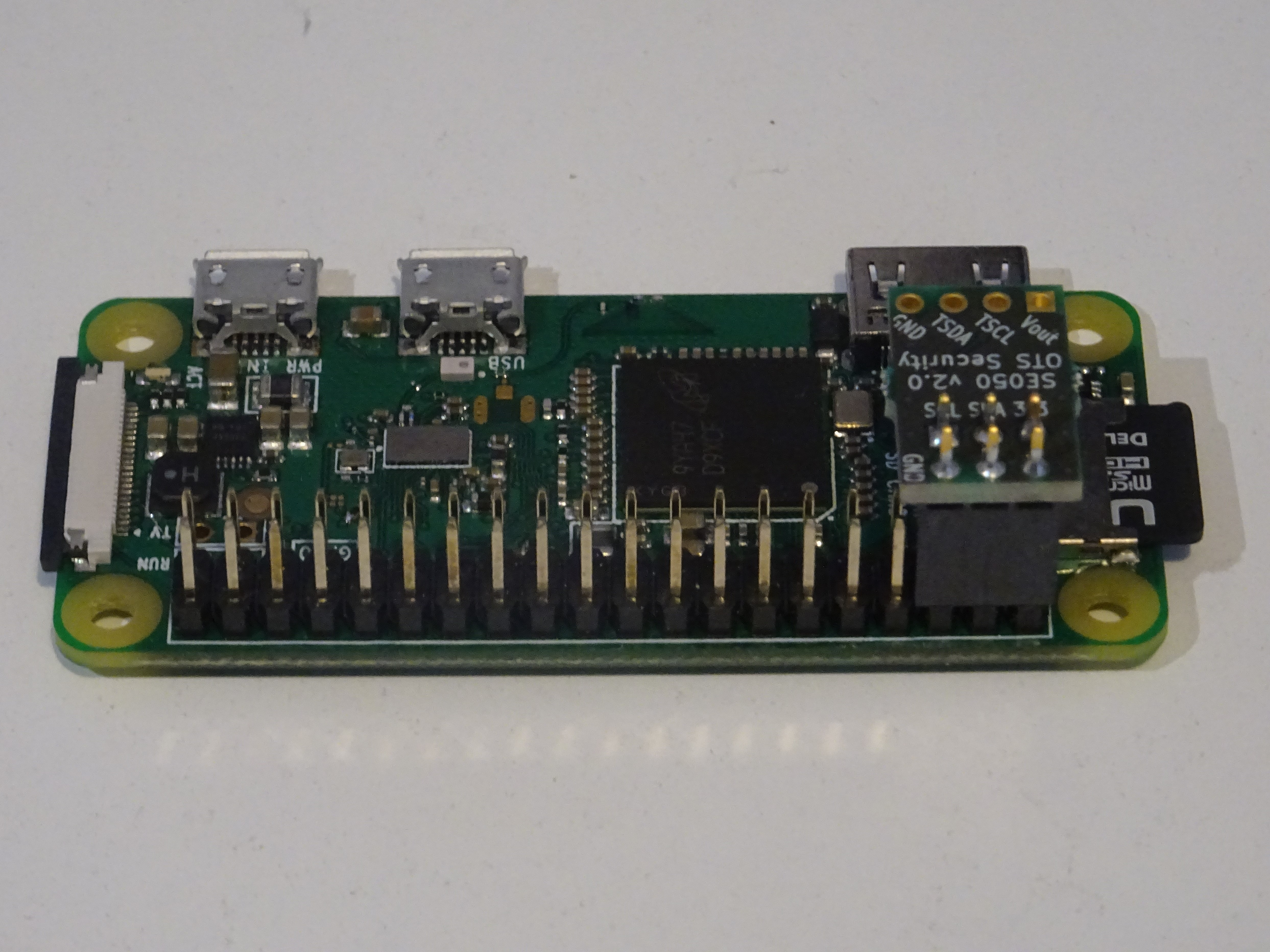
This product is a breakout board for SE050 Secure Element from NXP. It can be used to secure your IoT device against both remote and physical attackers.
Key Benefits
- Easy to use, just plug to your RPi and follow tutorials from NXP. Easier to use than SE050 dev board from NXP which requires wire jumpers.
- Ready-to-use examples available in Plug & Trust Middleware
Key Features
- CC EAL6+ based HW and OS running NXP IoT applet
- RSA and ECC Signature/Verification
- AES Encryption/Decryption
- HMAC, CMAC, SHA-1, SHA-2
- Fully encrypted communications between SE050 and RPi
- Open source library from NXP
- Attestation of outputs from an I2C sensor connected as a slave
Use Cases
- Secure connection to clouds (Amazon AWS, Microsoft Azure, Google GCP, IBM Watson),
- Wi-Fi Credential protection,
- Anti-cloning
- I2C sensor data protection



 Staf Verhaegen
Staf Verhaegen
 Pedro Minatel
Pedro Minatel
 Joey Shyu
Joey Shyu
 Hosein Movahedian Attar
Hosein Movahedian Attar
My engagement with the project has brought significant value, and I'd like to extend this insight to the https://hmrentacardubai.com/ajman-rent-car/ rent a car in ajman company team. This way, they can gain from it as well and consider integrating innovative approaches.