I had a Cpanel & I wanted to secure it with a 2FA-OTP but the phone was not secure because if destroyed, formatted, or hacked (because of wifi / 4G) I would lose access to all my services.
Searching for physical OTP on the internet and saw that the price was very expensive, so I decided to make one for myself.
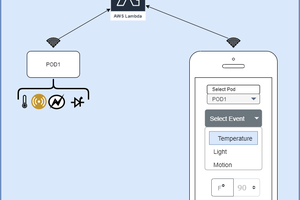
I already had M5StickC, and I also had some experience in developing phone apps so I created the whole system with an Android app.
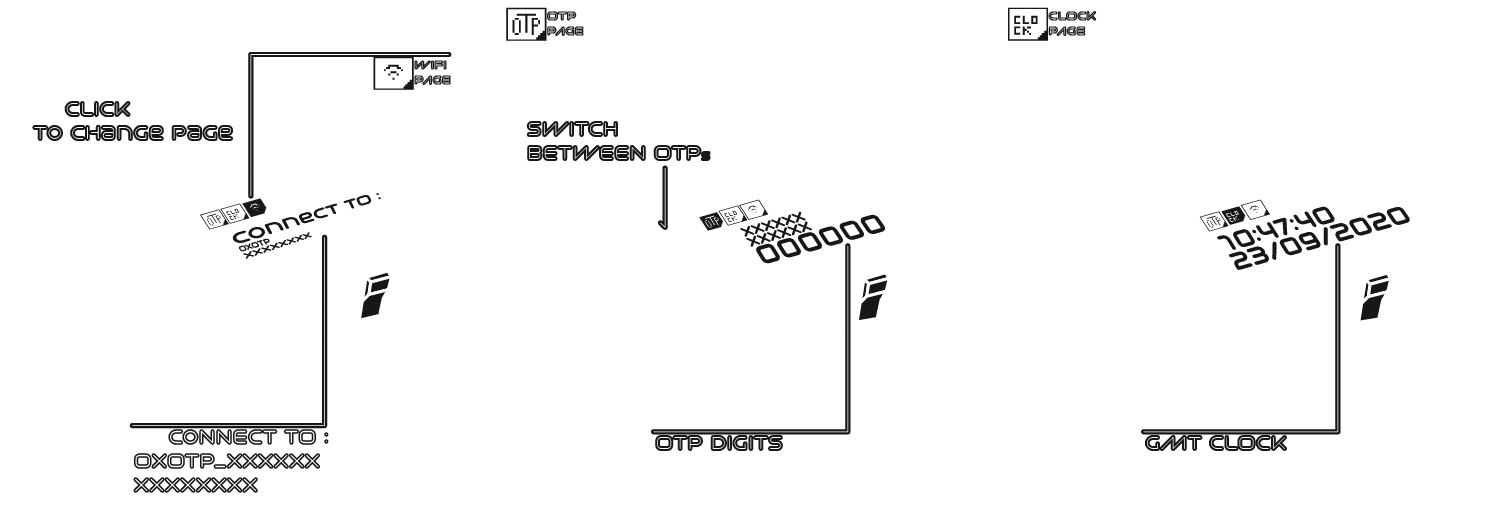
This is the first OTP based on M5StickC, with a cheap price the M5StickC is capable to get up to 30 record OTP.


A secure pin is set at the beginning of the config to maintain security, easy to set hard to hack.
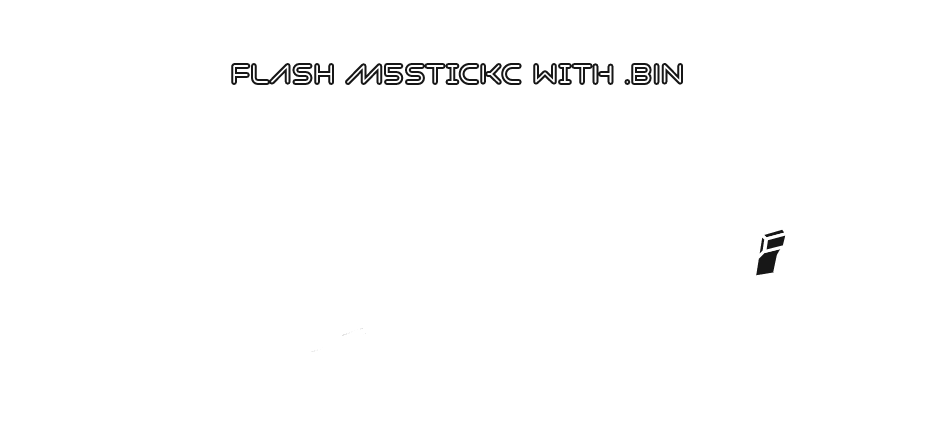
Just flash the bin file,
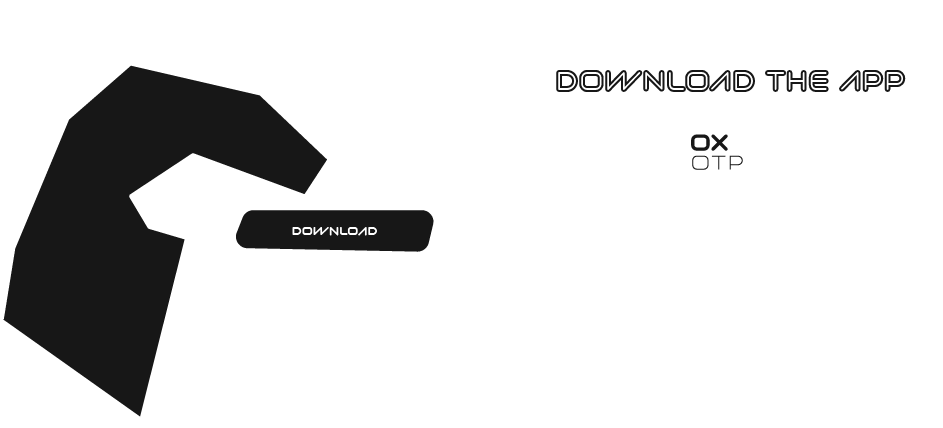
download the app https://play.google.com/store/apps/details?id=com.shox.oxotp
to read more détails check https://github.com/IMSHOX/OXOTP
 Mezghache Imad
Mezghache Imad





 Tyler Moroso
Tyler Moroso
 NaranInc
NaranInc
 Don
Don
Saying that something "Can't be hacked" is a sure-fire way to get hackers to break your security. Might want to remove that claim, lol.