I got a bunch of Beaglebone Black sitting around since my friend cleared out his garage. In my eyes, these are rather outdated compared to the vast fellowship the Raspberry Pi has - me too included.
But having these and not doing anything with them was an itch I constantly felt, so eventually I decided to do a bit of a learning project that was set to accomplish three goals:
- Learn Python - this was long overdue!
- Learn how to work with the Beaglebone Black / White / Pocket
- Identify an elegant way to "recover" the supervisor password in my own (not bios locked) Lenovo Thinkpad X201 Tablet
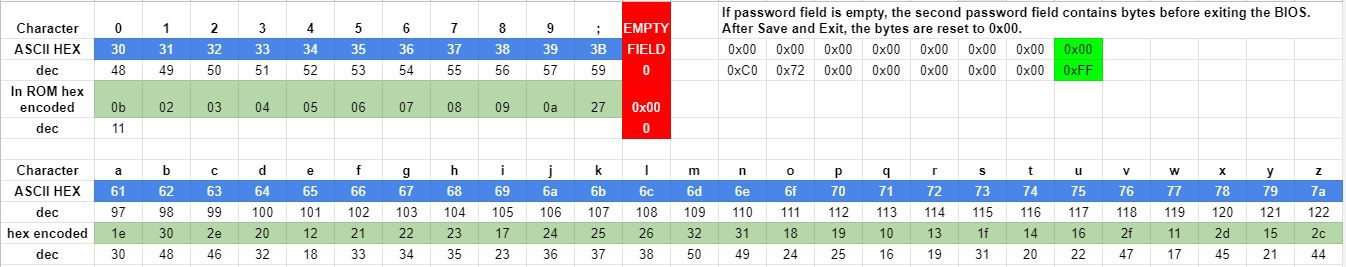
Using a non-locked laptop was mandatory for this idea because the password, if set, is/can be encrypted. Can't enter an encrypted password into the password prompt, can I? Therefore I needed to develop the encryption table by hand - but I'm getting ahead of myself.
The rest of the documentation can be found in the various log-entries of this project.
 Timo Birnschein
Timo Birnschein




 danjovic
danjovic
 Voja Antonic
Voja Antonic
can you do this on a EC chip on a newer laptop?