Power Consumption
When not measuring/transmitting data, Canique Climat roughly draws 1.87 µA at a voltage of 1.5V in hardware revision 0.6, and only 1.02 µA in hardware revision 0.7. We're going to have a look at revision 0.6 here.
What does this amount of consumption mean for battery life? Powered by a single AA cell with a typical capacity of 2500mAh, we can expect the following theoretical battery lifetimes at ~ room temperature - the estimated battery self discharge rate is specified in brackets:
| Transmission intervall | Battery Life Time @ High TX Power | Battery Life Time @ Low TX Power |
| 30s | 11* years [15%] | 16* years [20%] |
| 60s | 20* years [20%] | 27* years [20%] |
*) The values beyond 10 years are theoretical values since a typical alkaline battery itself has a shelf life of 10 years. Hence the real estimated battery life time is about 10 years.
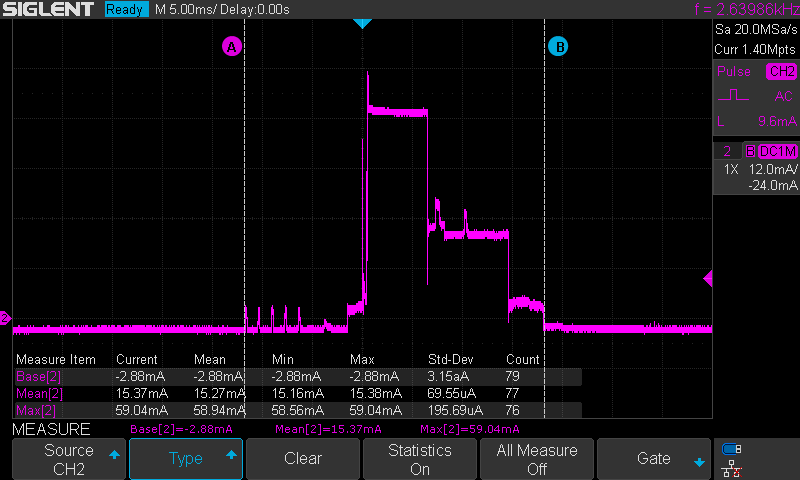
In the lowest TX power setting, measuring/transmitting takes about 30ms and consumes 11.6 mA on average. In the hightest TX power setting (see image below) the 30ms stay unchanged but the average consumption goes up to 18.2mA. The image shows the current drawn from a 1.25V lab power supply - using a uCurrent in mA setting.
On the image you can see the different stages after wakeup:
- Sensor measurement
- Encryption
- TX @ 13dBm
- RX of acknowledgment
- Decryption
Something that has even a bigger influence on the battery is temperature. When the temperature is very low, battery capacity might drop by 50%. At -20°C you can expect a bad performance from any typical alkaline battery. This is also due to the fact that the internal battery resistance increases at low temperatures.
But there is a simple solution to this problem: non rechargable lithium batteries. They are available in AA size, and they have no troubles at extremely low temperatures, as low as -40°C!
So, what would the estimated theoretical battery lifetime be with a 3000mAh AA sized Energizer Ultimate Lithium?

| Transmission interval | Battery Life Time @ High TX Power | Battery Life Time @ Low TX Power |
| 30s | 14 years [15%] | 20 years [15%] |
| 60s | 25* years [15%] | 35* years [15%] |
This time the battery itself has a shelf life of 20 years (!), besides the battery will run at very low temperatures, and on top of that it has an increased capacity of 3000mAh. So you can expect a battery life of 20 years using a 1 minute transmission interval.
All these figures are related to the revision 0.6 of the Canique Climat. (I posted different figures earlier this week that have improved with this latest revision)
Reducing message size
So, how to achieve this low level of power consumption?
The one thing is hardware - selecting components that are ultra low power. The second thing is software: Canique Climat makes use of low power modes excessively. It also keeps transmitted messages as short as possible.
Just 1 example from the software perspective: Say you want to send a temperature measurement of 23.54°C and a humidity level of 69.12%. How would you send this data?
A beginner might send characters, each character is enclosed in brackets here for readability:
[2][3][.][5][4][*][6][9][.][1][2]
That's 11 bytes in total.
Now you could leave away the 2 dots and the asterisk, because the message always has the same format - first the 4 digit temperature, then the 4 digit humidity. Then the message size would still be 8 bytes.
Sending bytes instead of characters would signficantly reduce payload size. We could send 23 as 1 byte, 54 as 1 byte, 69 as 1 byte and 12 as 1 byte. So we'd have cut the message size to a total of 4 bytes.
The alternative would be to look at the temperature as 2354 centi degrees. This would also fit into a 2 byte integer. Same thing for humidity: 6912 %*100. But we'd still be at 4 bytes total message length.
We started at 11 bytes and shrank the message to 4 bytes.
Canique...
Read more » canique
canique







 Christian Moll
Christian Moll
 mihai.cuciuc
mihai.cuciuc
 Kris Winer
Kris Winer
Is the Radio-Protocol open? I'am interested in integrating multiple CaniqueClimat-Nodes in my setup.