Manufacturer Android App can be found here : https://play.google.com/store/apps/details?id=com.gx_exploration_ufo&hl=en&gl=US
Review Video of Product which displays App and Drone.
In the photos I have added the Blue chip connects the camera and WiFi while the Green chip appears to receive communication from the Blue chip to control the motors
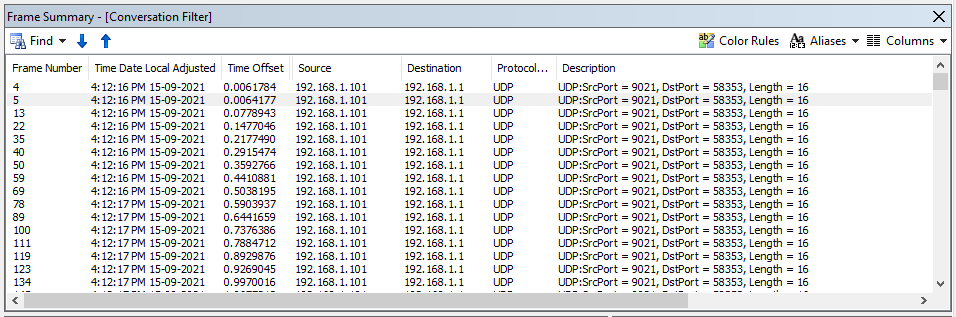

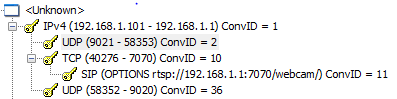
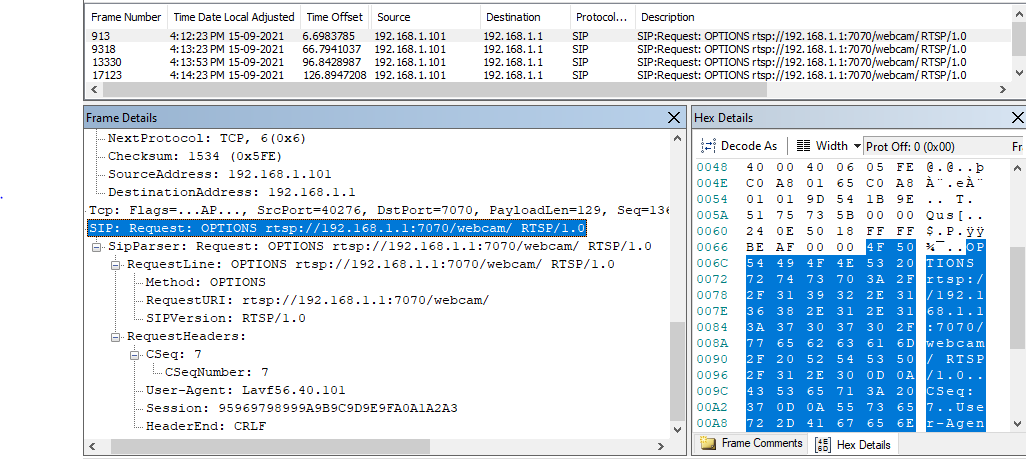

 Blecky
Blecky
 Dominic DeMarco
Dominic DeMarco
 Arthur Guy
Arthur Guy
 Kurt Kiefer
Kurt Kiefer