So from the public's POV, you saw this on our Twitter feed. We decided to get the hype train going a little early and threw a game together to give the l337 H@x0r community of DEFCON something to do over the holiday break. BEFORE READING ANY FURTHER, KNOW THAT THIS IS AN UBER SPOILER OF THE CONTEST STEPS. IT HAS BEEN WON ALREADY, BUT IF YOU STILL WANT TO GIVE YOUR SKILLS A SHOT, DONT READ FURTHER...or if you're the kind of person who racked out their NES checklist with a Game Genie to skip past the hard parts so you could have lunchtime bragging rights of the final boss details, by all means keep reading ;) And if you're too young to know what a Game Genie is...sigh...
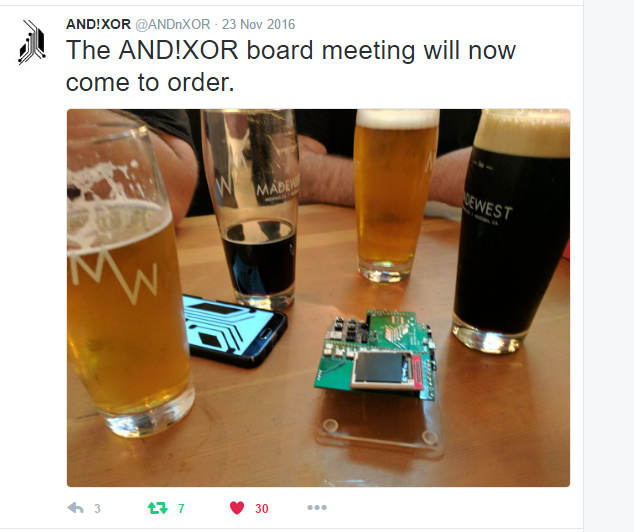
Anyway, about a month ago over a much inebriated brewery board meeting, we locked down a functional baseline of our DC25 badge. At some point, we started thinking of ways to have fun with a contest, and thus this cluster fuck was born. Over a lot of booze.
We figured, since we were going to give away a free badge, you should f-ing work for it. Instead of going the route of a certain genre of our DC interests, we decided to just layer and sandwich a bunch of stuff together. We knew since mid-October-ish (thats a word right?) we were going to do something, so we started tweeting out easter eggs and hiding stuff in youtube videos we knew we could use later on... It could have been the booze talking too...

Now at the same time when the contest started, we were running a booster campaign. https://www.booster.com/andnxor Designing and Prototyping badges isn't cheap. It costs us a lot of money. So we we're boosting with shirts that contained a silhouette of the badge design. It had a cryptic message: 42 59 54 45 20 4d 59 20 53 48 49 4e 59 20 4d 45 54 41 4c 20 42 41 44 47 45 21

Okay so, in step by step, lead you by the hand fashion, here's a typical way someone could have gone about winning the contest.
- It was hidden somewhere on the internet....try our web page
- There's only a couple of images, if one tried to download MANBEARPIG (which we referred to a ridiculous amount of times on Twitter) you would notice you cant. We blocked it out with CSS.
- View Page Source
Well looky here, there's the name of the style sheet "andnxor.css". Lets type that in...
- Looks like someone updated the manbearpig.png with a new version "v2" thats odd. Lets download it. Now that we know the file name, you can just type it in the browser address, and save as. Wow that took forever right? Well most people wouldnt notice cuz their interweb speeds are so fast. But look at the file properties. Isn't it a little odd that you have a BLACK AND WHITE PNG image that's 800kb?
- Steganography - the practice of concealing messages or information within other nonsecret text or data. Now this is where paths can diverge on solving the puzzle. You could verify something is hidden the proper way, load it in a hex editor, and notice the regularly unused bits of the image have data in them. Or just hack around. There's many steganography applications out there, even fewer are free and open source
- Load the Image in OpenStego
- Given the shit I've put you through thus far, you should assume its just not that easy. Of course we damn well password protected it. There were many hints thrown out on twitter, youtube and chats...
- I even blurted out "C1E169852F1D95CC2DA7AA791E5F4EFF"
- All signs point to the password being "EXCELSIOR!"
- Cool, so you now have a PNG with something hidden inside of it, OpenStego, and a password. Extract it and what do you get...
![]()
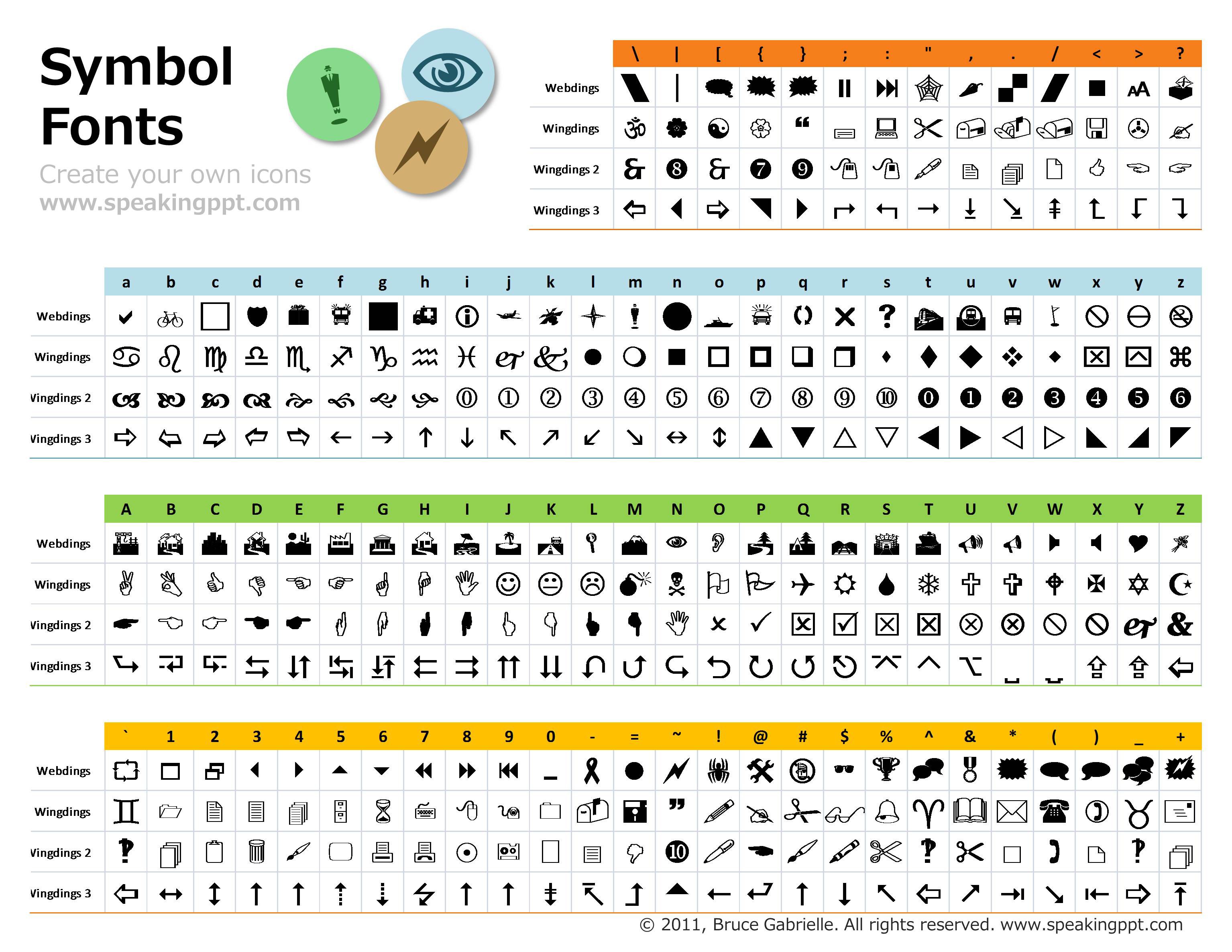
- Well shit there's the badge art which we will be screening on to the PCB. Awesome right? Well, we hope you think its awesome. But this was a contest to win a free badge and you had to tweet the secret word. And we're some god damn assholes that put something in wingdings.
- Translation Time
![]()
- Be careful, its not so easy to visually translate images. You lack the luxury of copy/paste and OCR doesnt work on wingdings.
- GJRRG @NAQaKBE "QRNQORRS" SVEFG CREFBA JVAF N ONQTR
- Cypher Time
- So at this point we didnt really try too hard, we figured who made it past the steganography it would just be a race at this point. So ROT13 it is !
- TWEET @ANDnXOR "DEADBEEF" FIRST PERSON WINS A BADGE
We'll kids, thats it. Give a shout out to @compukidmike. And just as important, let us know what you think in the discussion section below. This was my first attempt at creating a puzzle that literally hundreds of people were competing over and messaging us non stop over the holiday. Even more so, what do you guys think of the badge art? Until further project updates, this is Hyr0n - signing off.
 Hyr0n
Hyr0n

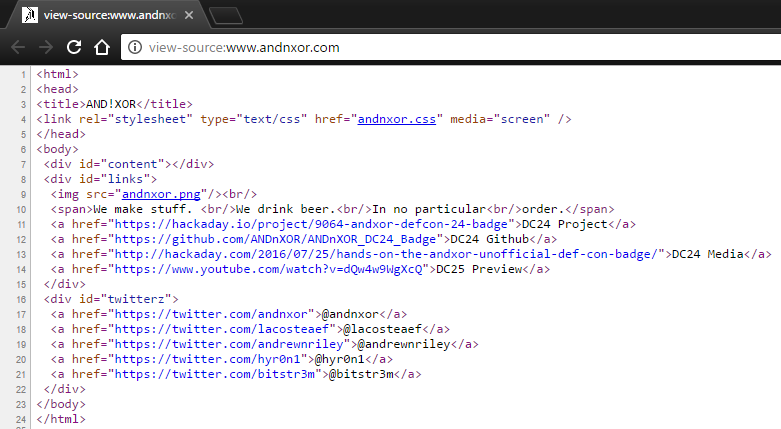 Well looky here, there's the name of the style sheet "andnxor.css". Lets type that in...
Well looky here, there's the name of the style sheet "andnxor.css". Lets type that in...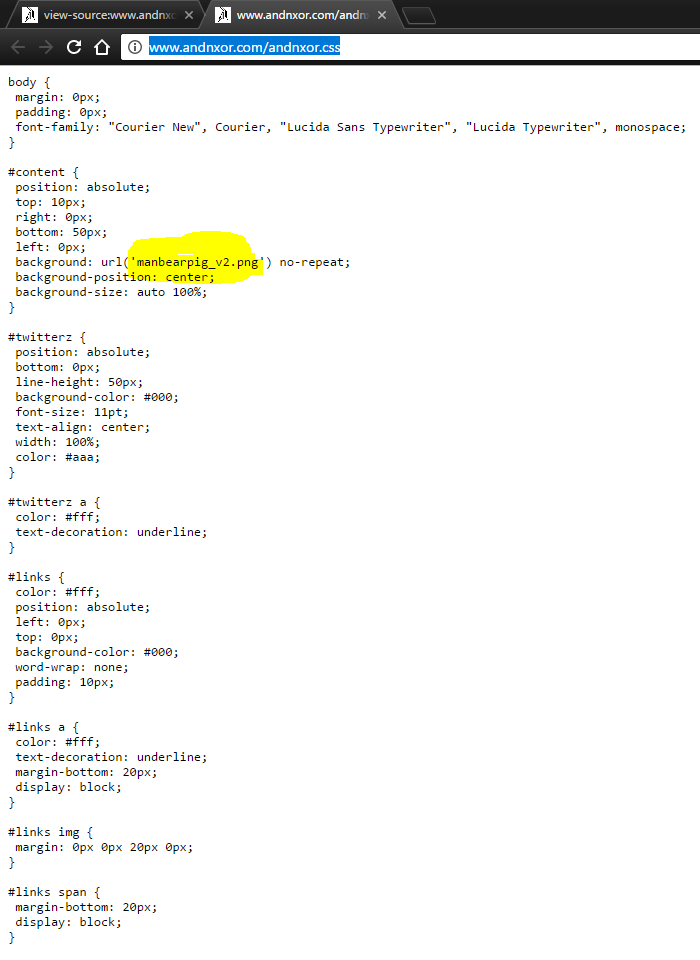

 We'll kids, thats it. Give a shout out to
We'll kids, thats it. Give a shout out to
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.
Incase you're wondering, "DEADBEEF" refers to error_code = 0xDEADBEEF, which is from the Nordic softdevice stack.... ;) Hint hint....
Are you sure? yes | no