Botnet
The hackers at AND!XOR have full command and control over all badges in our ad-hoc wireless badge-net. We may dictate the badges send lulz, gifts, ransom-booze-ware, or unleash DDOS havoc on all of our badge holders if they are jerks. Depends on our level of drunkenness...
But oh, you're telling yourself, "There's no way they could do that, those AND!XOR dudes are somewhere in the casino getting hamski'd." Well those badges are acting as badge-net layer 2/3 repeaters. Once you're infected, you're contagious, and a mobile mesh network node executing instructions we have commanded for a duration of time. Given the density of badges in the population and expected foot traffic, we have high confidence we can reach most participating in the game unless they are hiding under a faraday blanket. That's all we are willing to say about the implementation so folks don't figure out how to abuse the system with an SDR or crack our encryption with a ChipWhisperer. Challenge poker chips and beer if you do, unless you're part of some uber fantasy hacking team composed of Mike Ossman, Joe Grand, Colin O'Flynn, and Joe Fitz (which is no fair).
By activating the badge (WE WILL PIN A TWEET WITH A CODE @ANDnXOR) you enable connectivity and consent to participate in the badge Botnet game. If not, please go to settings and enable Airplane mode once the badge has been activated if you did it by accident (or just don’t activate it, your loss)
For those who have concerns, don't forget we rolled our own custom firmware, executables, and packet structure for the badges. These badges cant be used to harm any *real* systems, since the payloads can only be interpreted by the AND!XOR badges (its absolute garbage to any other OS). This is a safe hax0r friendly environment for you to play in. Hope you have fun, we know we will!
So why would we do this? Control complex for one, but more importantly, to inject chaos while our badge holders play a little game...
Game
BOTNET: The AND!XOR feature multiplayer badge game for the security minded. Congratulations you are the new grey hat sys admin of your very own badge! Take the time to assess your badge, find its vulnerabilities, secure it, and exploit those vulnerabilities on other badge holders before they lock it down. All the while a massive botnet attack is keeping you occupied.
Basic Rules
- You must protect the badge from all the l337 hax0rs out there. To do this, it will cost you points.
- You earn points based on how many services you have accessible.
- You do NOT earn points for a service if it is disabled or blocked by a firewall rule.
- You can spend points on enabling, disabling, and patching services.
- You can spend points on modifying firewall rules (allow/deny).
- You can spend points on security research and upgrade of exploits.
- You earn experience (XP) when you successfully attack another badge.
- Service's attack surface increases over time unless patched.
- Exploits strength decreases over time unless upgraded.
- To attack another badge you must use an exploit payload on a service your victim has running, which isn’t blocked by your firewall or theirs.
- If you earn enough XP you will level up and perhaps unlock more features on the badge…
Details
This is the main screen the sys admin will see at botnet. Here's an explanation of the various fields...
- Name
- The name you set to your badge is also your player name. Other badge holders will see this when you attack and when they attack you.
- Level
- Your overall level, it increases as you gain XP
- Points
- The total point pool used for modifying services, firewall rules, patching, or performing security research of exploits.
- XP Bar
- The total experience gained thus far per level. When it fills up you will level up.
- Exploits
- The total number of exploits in your payload cache.
- Avatar
- The avatar people will see when they try to attack you. This can be changed in settings.
- Nearby
- Shows how many AND!XOR badges are nearby for you to attack.
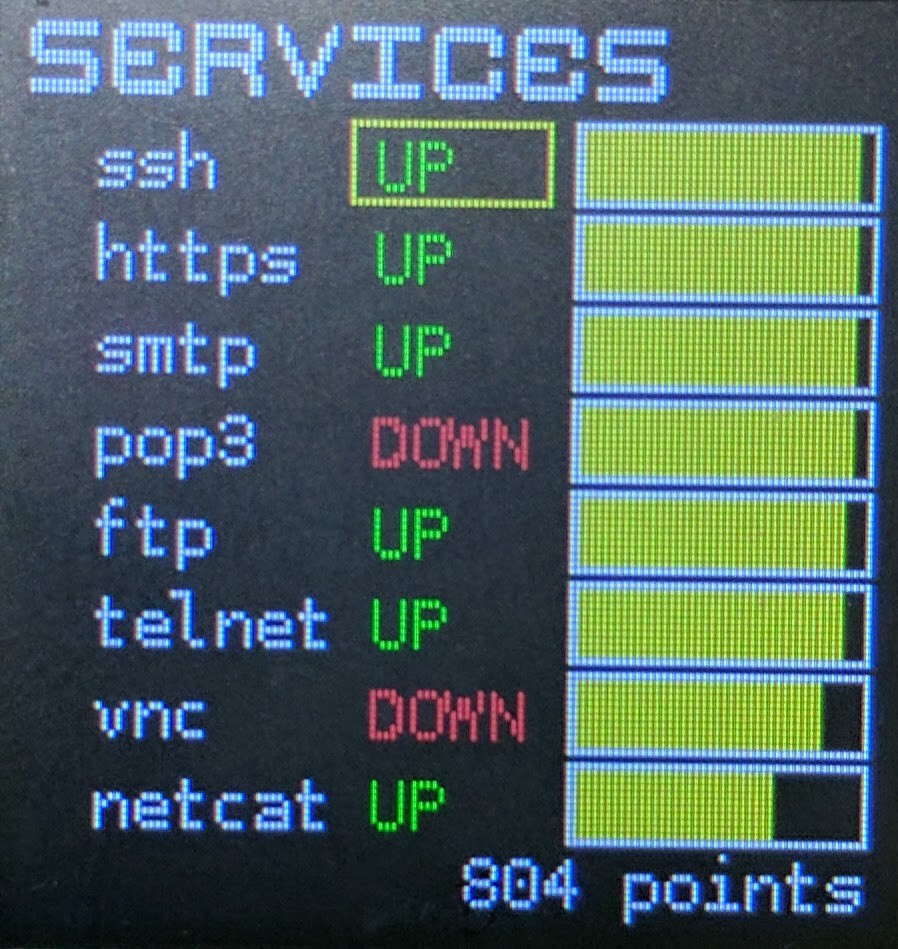
- Service Status
- The inner vertical bar represents whether each service is running (GREEN) or stopped (RED). Keep an eye on these, the backup admin (Scruffy) is really bad at his job and they may randomly change every 15 minutes...
- Firewall Status
- The outer vertical bar represents whether the firewall rule for each service is set to allow (GREEN) or deny (RED). Keep an eye on these, the backup admin (Scruffy) is really bad at his job and they may randomly change every 15 minutes...
- Services
- From top to bottom, the services for your badge are: SSH, HTTPS, SMTP, POP3, FTP, TELNET, VNC, NETCAT
Duh...(More Options) && Further Rules Explained
Allows you to modify (start/stop) Services, change (allow/deny) Firewall rules, Patch all services, View and upgrade your current exploit cache.

- Services
- Shows a detailed status of all services: whether they are up or down and the yellow bar is how secure they are (over time they become more exploitable and the yellow bar drains, SO DON'T NEGLECT YOUR DAMN PATCH CYCLE!). You may also modify a service by selecting it with the UP or DOWN keys and hitting the Action button (far right button on the badge). Don't forget you need services running to earn points. But then you increase your attack surface...choices...
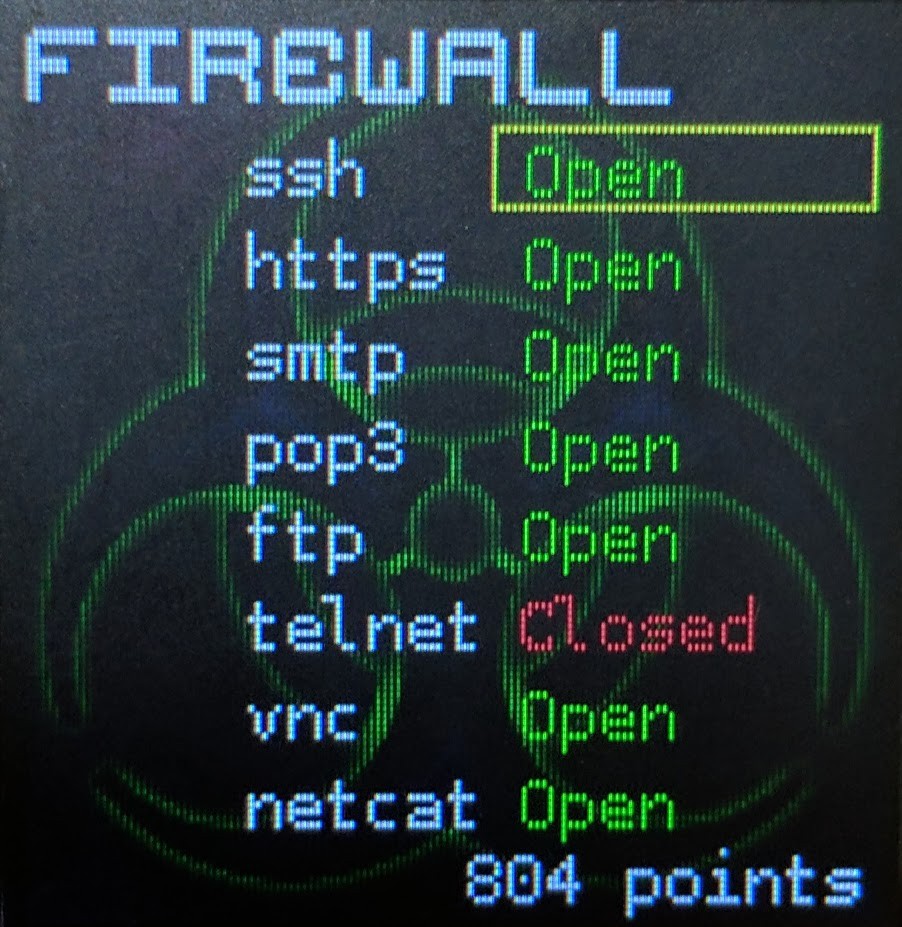
- Firewall
- Shows a detailed status of your firewall rules. If you aren't familiar with this concept...we have problems. But seriously, if the traffic is allowed (green) then the ports/protocols for your particular service are allowed to leave the badge (and traffic for that service may come in to your badge). This is EXTREMELY important to understand. You cant, for example, use an SSH exploit on another badge if your own firewall is blocking SSH. If you attempt something this stupid, we will penalize your points. More importantly, this is a double edged sword: you must open up your firewall to attack others and by doing so you make yourself vulnerable. Every time you modify a firewall rule it will cost you points.
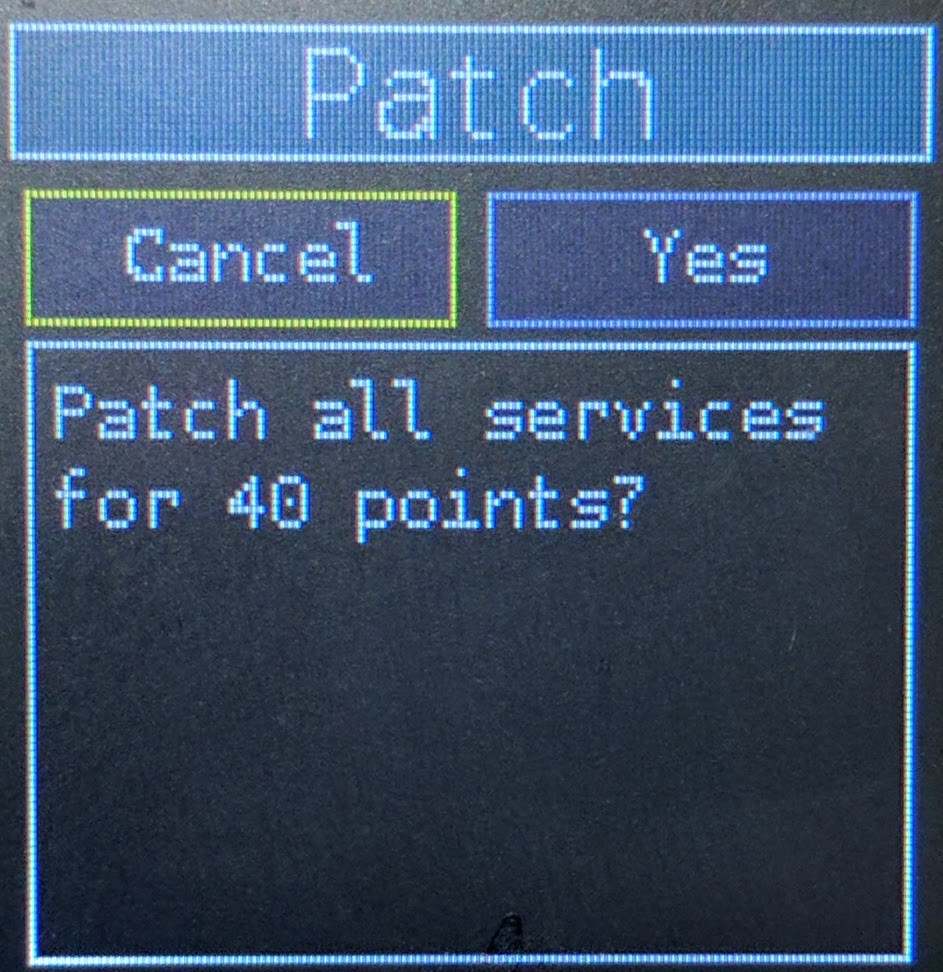
- Patch
- This is how you patch your services to keep them secure. The patch level of a service is critical in determining whether or not exploits will compromise your system. When you see the yellow status bars getting low on the Services detail screen, you should patch.
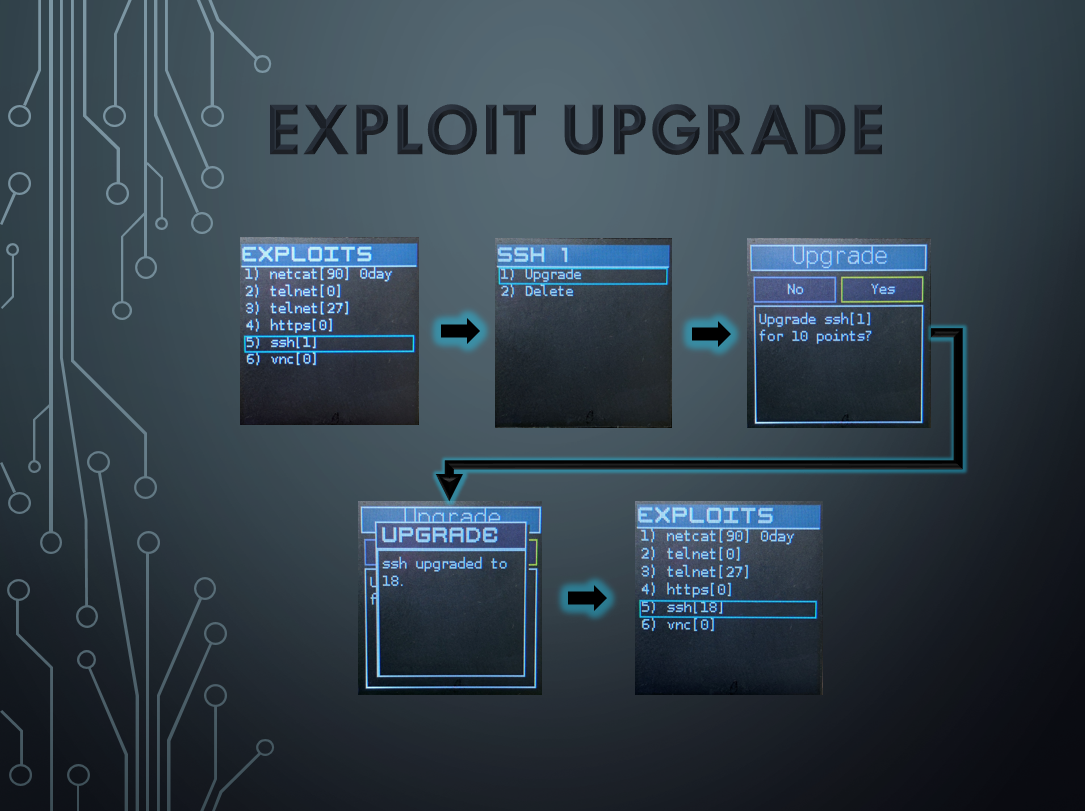
- Exploits
- Shows a detailed list of all payloads in your exploit cache. The number next to the service exploit indicates how strong the exploit is; e.g. telnet[9] means you have a payload which can be used against telnet with a strength of 9/100. When an attack occurs, the strength of your exploit is compared to the strength of the potential p0wnage target's service patch level (which you cant see). If your exploit strength >= service patch level, your exploit is successful.
- You can upgrade your exploits by selecting them with Action and choosing upgrade (it will cost you points). Most exploits are weak once initially researched, so you should spend time upgrading them before launching an attack. You can only upgrade an exploit 4x.
- If you are lucky, you may research upgrades to the point of a Zero Day[100]; denoted with "0day" at the end of the exploit. This attack has the greatest chance of success. Use it ASAP since even zero days lose their effectiveness over time...
- Exploits effectiveness degrade over time due to patch cycles. So if you hold on to it for too long, it wont be as strong as when it was initially discovered. For example, over time your exploit could degrade all the way to [0], this will NOT be successful.
Smartphone Terminal
Remeber the <REDACTED> parts of the Smartphone Terminal update?.. .We'll now you may get it. Read that log for details pertaining to our companion app. The links to download it are in that post.
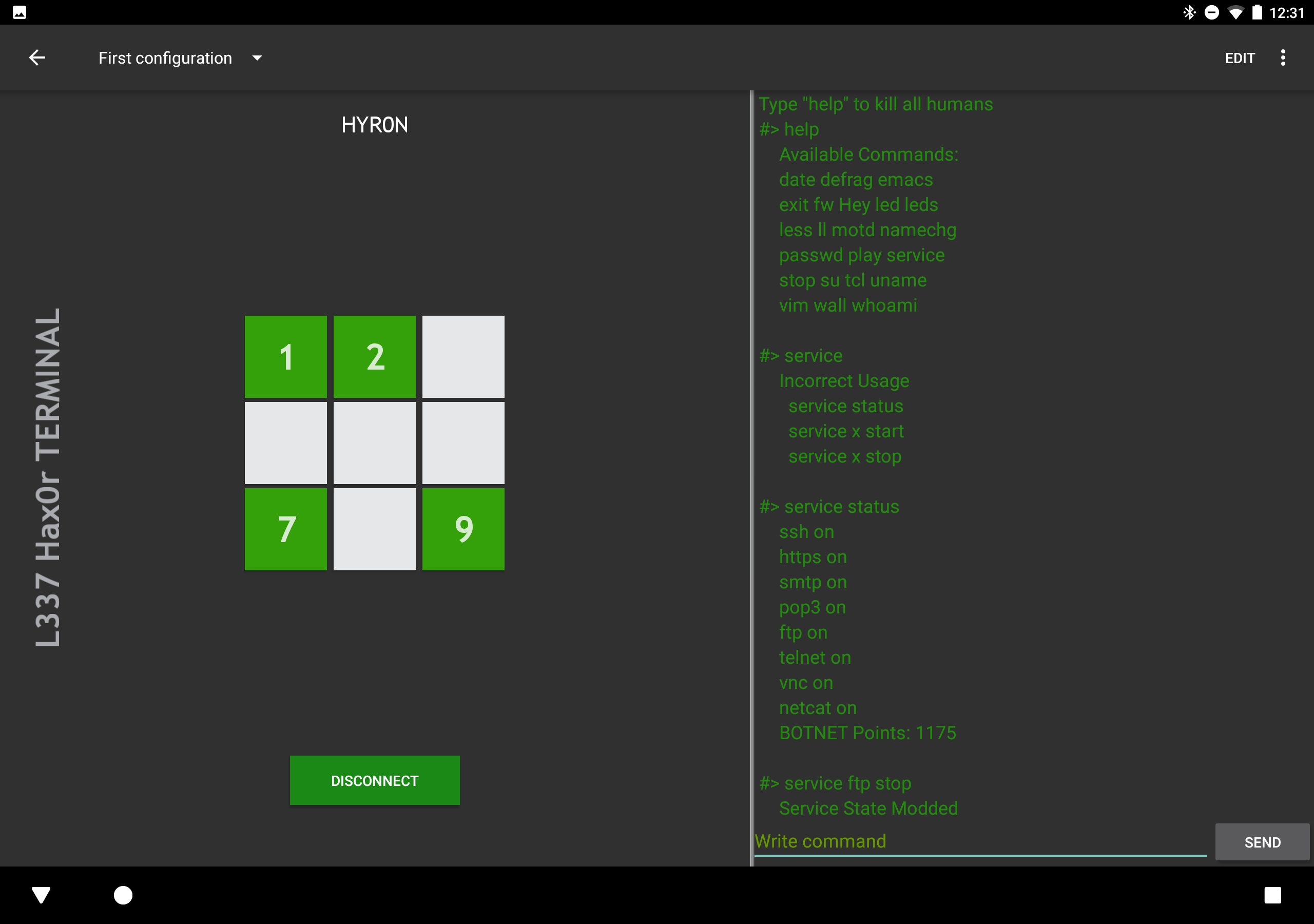
The terminal can be used for many lulz, utility functions on the badge, discovery of unlocks, and modification of botnet services and firewall rules. We've also included a script kiddie toolbox so you can quickly execute commands at the tap of a button (but you have to program it yourself).
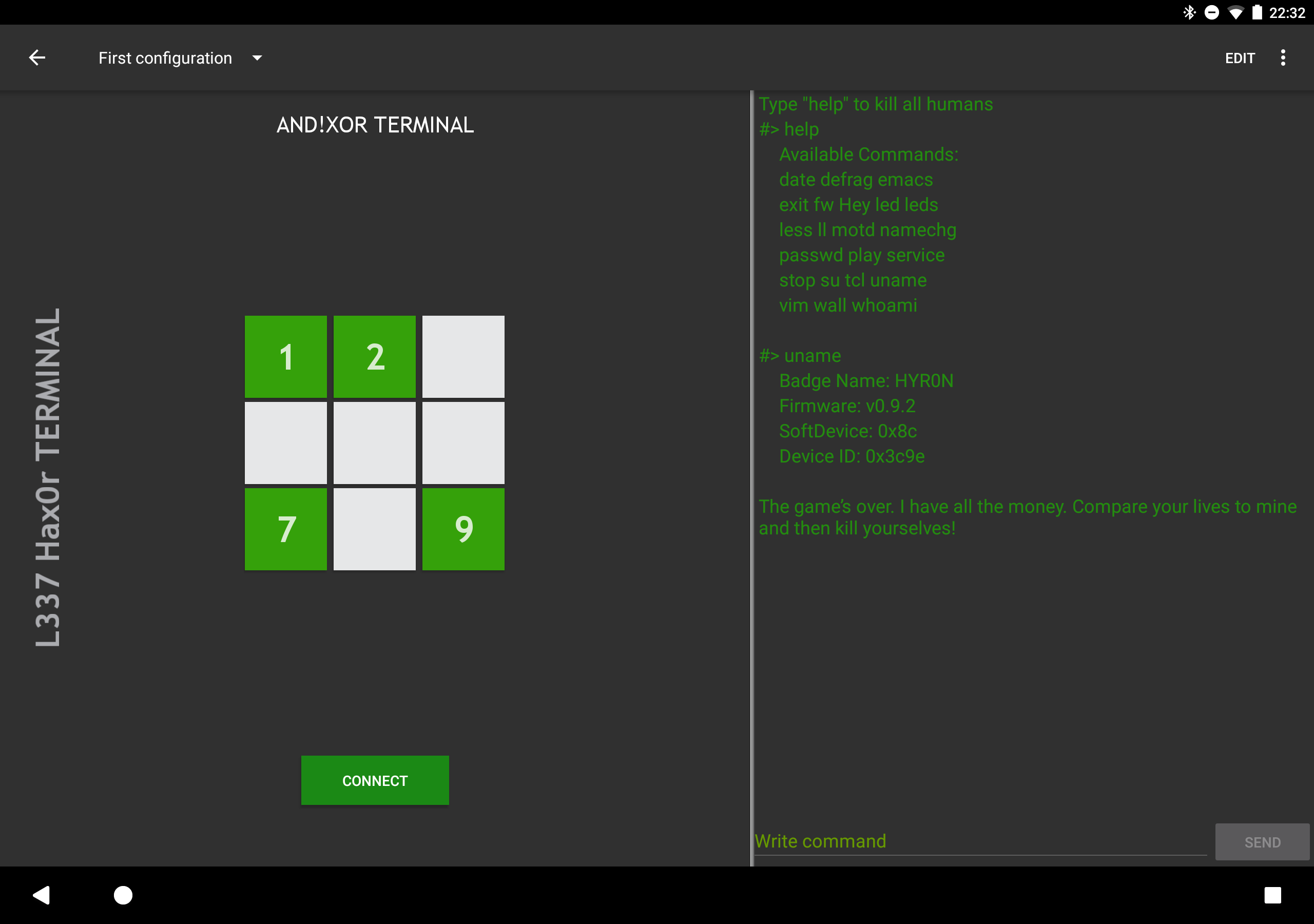
Reminder: While you are logged into the maintenance terminal, the badge is in "MAINTENANCE MODE" (e.g. the badge is offline)
CAUTION
The badges were pushed out early before they could be fully secured... (CVE-AND!XOR-1337) All badges have a default root password enabled. Sys-admins are advised to determine what that password is and change it ASAP! Otherwise malicious unauthorized users may remotely log into your badge via terminal and modify services or firewall settings for the benefit of exploitation ;)
Here's an example of some strategery...
- Attempt to hack someone's badge with your most badass exploit
- Notice they don't have the service enabled or firewall open so you can't use it on them
- Log in to THEIR badge via remote terminal (puts the badge into maintenance mode)
- Escalate privileges* (this is a puzzle all in itself)
- Turn the service on that maps to your badass exploit
- Change the firewall rule so your exploit cant make it through (allow)
- Type exit to de-escalate your privilege (or dont...whahahahah)
- Disconnect from their badge by hitting DISCONNECT on the app (ending maintenance mode)
- Use your badge to successfully p0wn theirs
- (Optional) Leave a message on their wall using the "wall" command, before disconnecting
- (Optional) Open up their entire firewall for the lulz, before disconnecting
- (NEVER OPTIONAL) Have a b33r
Command Line Interface
So there were some commands that we also had <REDACTED> in the previous update as well as some commands that didn't make much sense. Now they do. In addition, you may understand why we provided the script kiddies out there with a quick way to execute commands, perhaps to quickly escalate privileges, modify services, and firewall rules...
- fw
- Allows the display and modification of all firewall rules
- Usage: "fw x allow|deny" where x is the service rule you want to modify
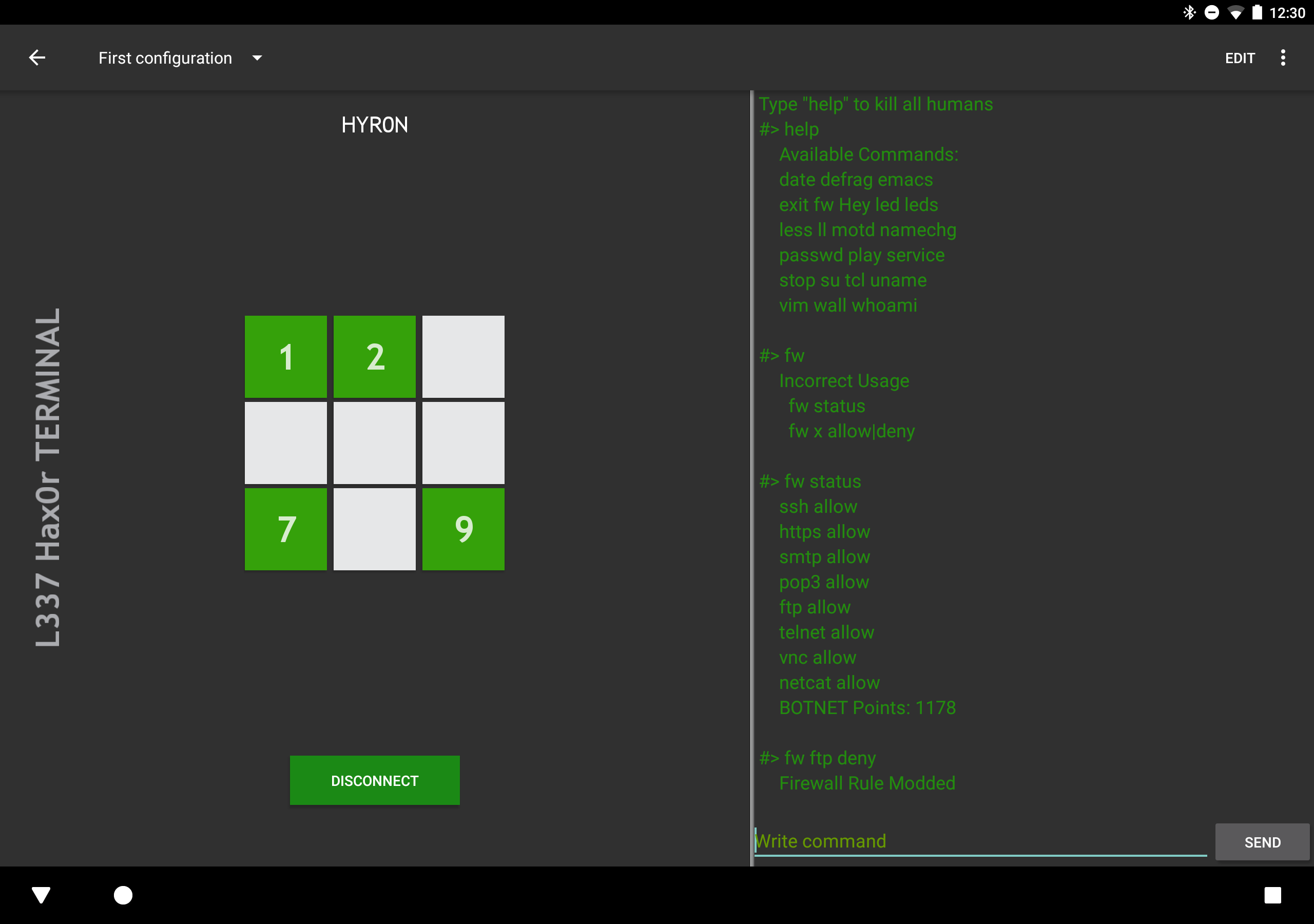
- service
- Allows the display and modification of all services
- Usage: "service x start|stop" where x is the service you want to start or stop
- su
- Allows you to switch to a different user account. Possibly one which has the permission to execute fw and service. HINT HINT you have to figure out the other user account(s) AND their passwords before you can become a command line ninja.
- exit
- Logs out the current user session. Our badge is stateful :) Meaning if you forget to type "exit" once you're in maintenance or root user mode, that's as stupid as walking away from an actual terminal with a privileged user logged in. Don't say we didn't warn you...
- passwd
- Once you figure out what the root password is, you should probably change it. This also means if you take too long to figure this out someone else (actually anyone with a smartphone) may log into your badge, change your root password, and lock you out. Time is of the essence. If your system is compromised, you only have two options (just like in real life):
- 1 - Go to your badge settings and reset it, start from scratch. You'll have to re-unlock features and your BOTNET points will be at ZERO.
- 2 - Hire some l337 BADGE Cyber Incident Response Team (BADGE-CIRT) like AND!XOR to recover your system. We work for beer, however we can't guarantee our availability.
- Once you figure out what the root password is, you should probably change it. This also means if you take too long to figure this out someone else (actually anyone with a smartphone) may log into your badge, change your root password, and lock you out. Time is of the essence. If your system is compromised, you only have two options (just like in real life):
Summary
So you have AND!XOR perturbing the system and injecting chaos via a botnet, all badge holders squaring off with one another via their sys admin interface for some badge like Capture The Flag, and anyone with a smartphone has the ability to gain access through a backdoor remote terminal and p0wn your badge. ENJOY!
 Hyr0n
Hyr0n

Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.