I bought this toy few years back, and while having a blast with it, I managed to break the motors completely. I haven't found exact replacements so I figured -- I can hack it a little bit as manufacturer thoughtfully left SWD pads on the bottom side of the board. The board is equipped with:
- STMF031K4 - microcontroller
- Invensense mpu 6050 - Gyro + Accelerometer
- HS6200 - 2.4 GHz RF module
- four transistors, led, and power supply regulator
 lb5tr
lb5tr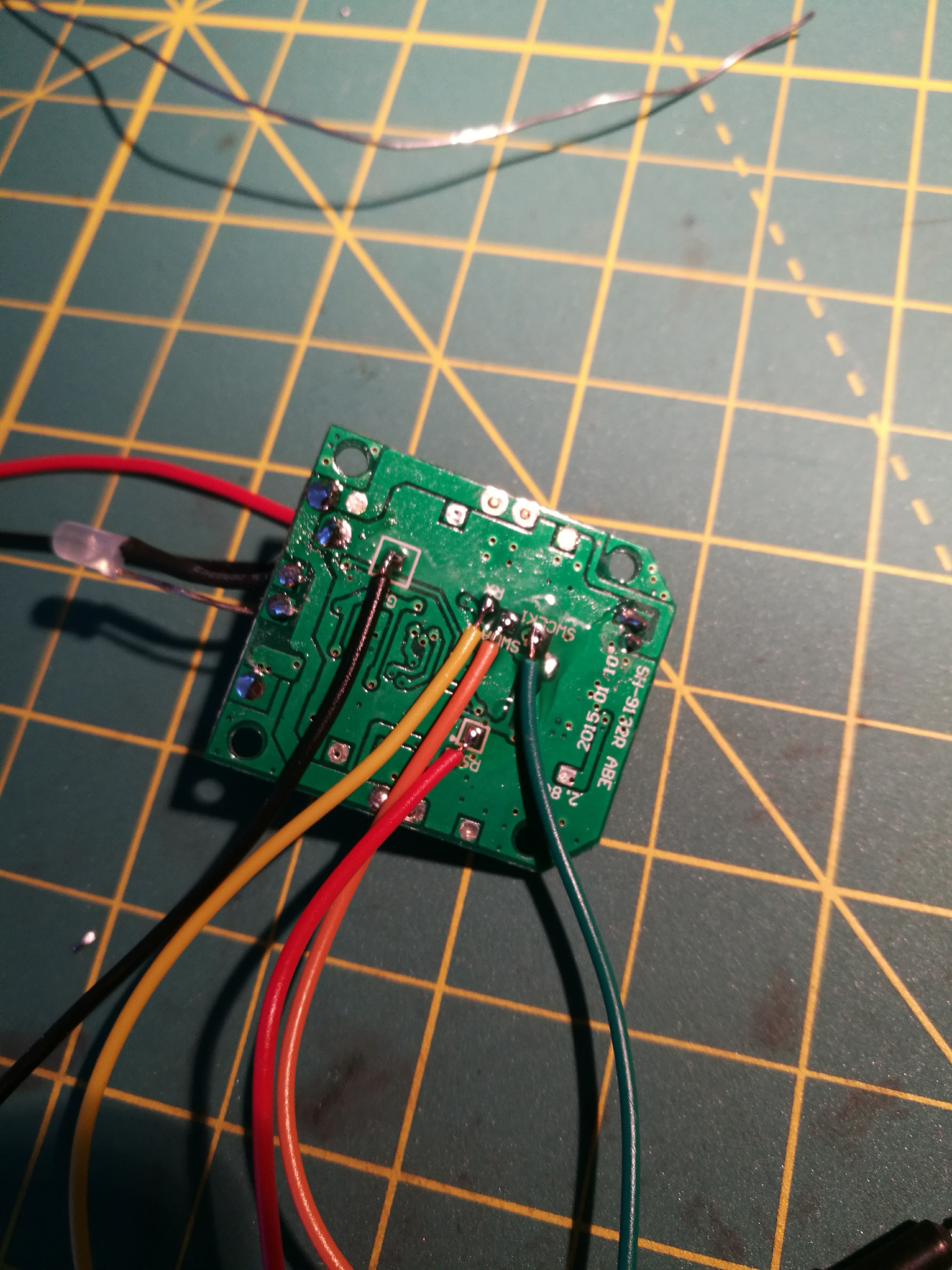

 Chance Reimer
Chance Reimer
 Ken Yap
Ken Yap
 Christoph
Christoph
 Vedran
Vedran