USING THE HUAWEI E3531 USB DONGLE FOR ELEPHANT DETECTION DEVICE MOBILE CONNECTIVITY
Earlier we looked at setting up the Huawei E303 USB dongle for mobile connectivity. Here we'll look at setting up the E3531 model in two modes. These dongles are really low-cost compared to HATs! This one was only £21!
1.
So first of all let's get started by setting this as HiLink CDC-Ether mode for PPP via eth2 over 2G/3G to connect to the internet. Then we can change it to serial modem if we want later on.
The E3531 will then have the following ID in this case: 12d1:14dc , with 12d1 being the vendor ID, and 14dc being the HiLink CDC-Ethernet model/mode ID.
Let's connect the E3531 to the USB port on the pi! Now run the 'lsusb' command to list usb devices attached to pi. Hopefully you'll get the following:
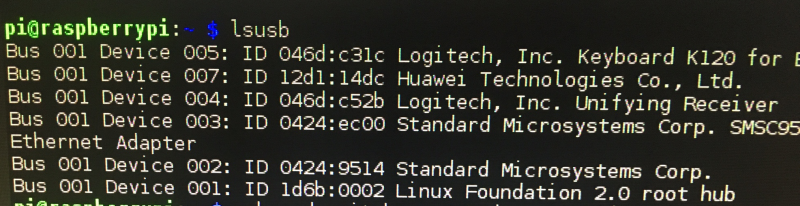
As you can see we got ID 12d1:14dc so that's great. It's in HiLink-CDC-Ethernet mode! That's supposed to be the default state for the E3531 so you don't need to worry about it being stuck in mass storage mode like the E303.
Now we can use the Huawei HiLink to set everything up to connect to our carrier. Go to the web-browser, and access http://192.168.8.1 . Then you'll get the home html file giving your status:

Then you can go along to settings and enter your carrier information. So once you get connect, you are all ready to access the internet using PPP via eth1! That was all quite easy!
2.
Next, let's switch it to a serial modem so we can send AT commands to get out SMS messages in lower connectivity scenarios. We'll be wanting to access it as tty/USBx
We need to switch our E3531 mode from 12d1:14dc to modem mode i.e. 12d1:1001 with 3x virtual serial ports. Let's get started by downloading and installing usb-modeswitch:
sudo apt-get install usb-modeswitch
No let's make a file containing our switch mode instructions. The instructions are:
TargetVendor=0x12d1
TargetProduct=0x1f01
MessageContent="55534243123456780000000000000011062000000100000000000000000000"
The message content depends on the firmware of your E3531, so honesty, the above might not work and you'll have to experiment/research to find a message that does :-(
Right, so let's make the file for usb-modeswitch to use:
sudo nano /etc/usb_modeswitch.d/12d1:1f01
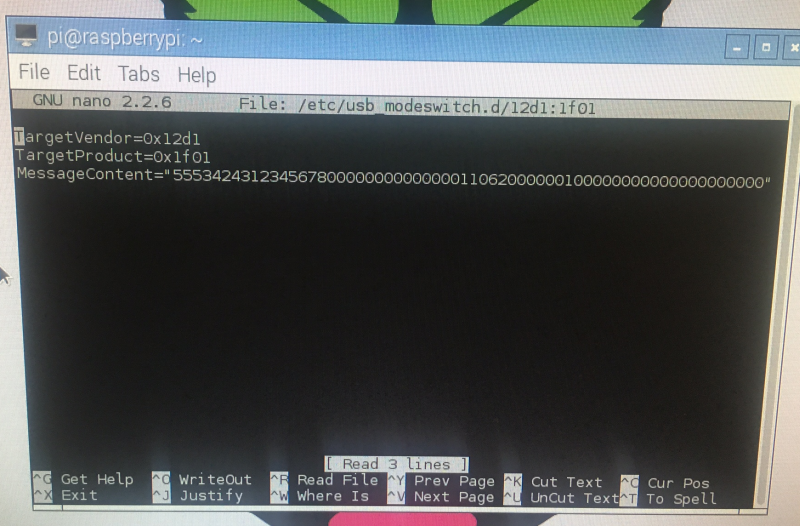 and add those instructions to the file! Then save it. Then reboot the pi.
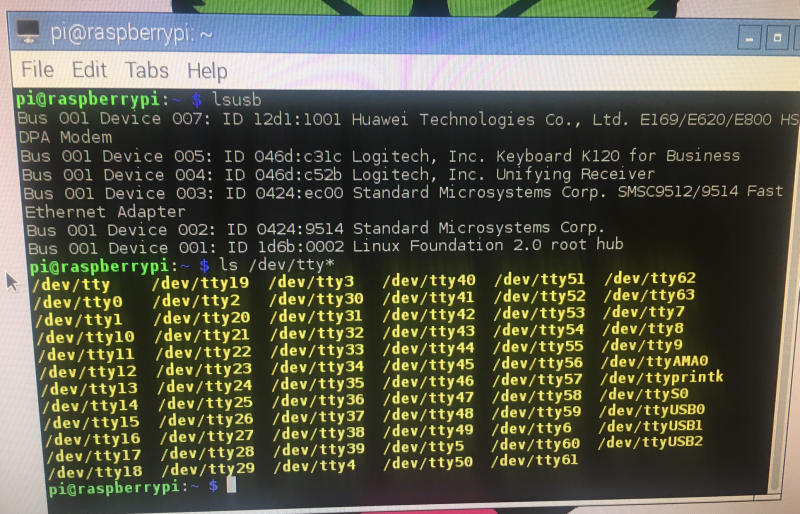
and add those instructions to the file! Then save it. Then reboot the pi.Now after reboot, we can issue the following command: 'lsusb' and we should see the new ID as 12d1:1001 so the E3531 has switched to serial modem mode!
If we issue the command ls /dev/tty* we'll see our virtual serial ports: ttyUSB0, ttyUSB1 and ttyUSB2! Great!
3.
Now we can go ahead and connect to the virtual serial ports and issue some AT commands! I used cu "call up another system" (https://linux.die.net/man/1/cu) to do this.
sudo apt-get install cu
So after you've installed it, execute it with following arguments to connect to ttyUSB0:
cu -l /dev/ttyUSB0
Now I went ahead and sent some AT commands. Sadly they don't echo, so you can't see them!
The first was 'AT' and I got back OK. Then I issued 'AT+CMGF=1' which tells the modem to act in SMS mode, and got back CMS ERROR 302, which is operation not allowed. Then I tried to send an SMS with 'AT+CMGS="+443283870634" <CR>' which returned an error code of CMS ERROR 302 again! These errors are likely due to the SIM card requiring a PIN or PIN2. If the SIM is blocked, the error would be due to SIM required PUK or PUK2 (personal unblocking codes).
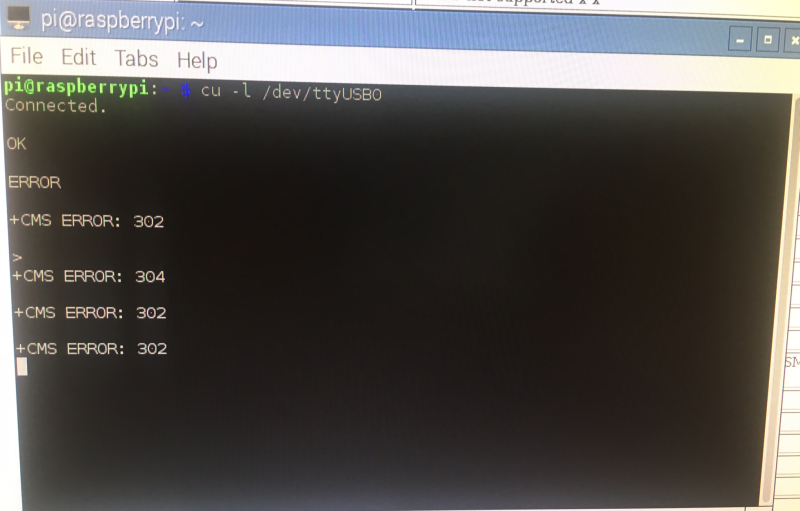
You can send a PIN using AT+CPIN="0000" <CR>. Note that carriers will block the SIM after 3x incorrect PIN attempts, and you will need to use a PUK or PUK2 to unblock it. All the carriers have default PIN codes.
* It turned out that the error was due to me not entering AT+CMGF=1 correctly, not a PIN problem after all!
You can find a full list of error codes here: http://www.smssolutions.net/tutorials/gsm/gsmerrorcodes/
4.
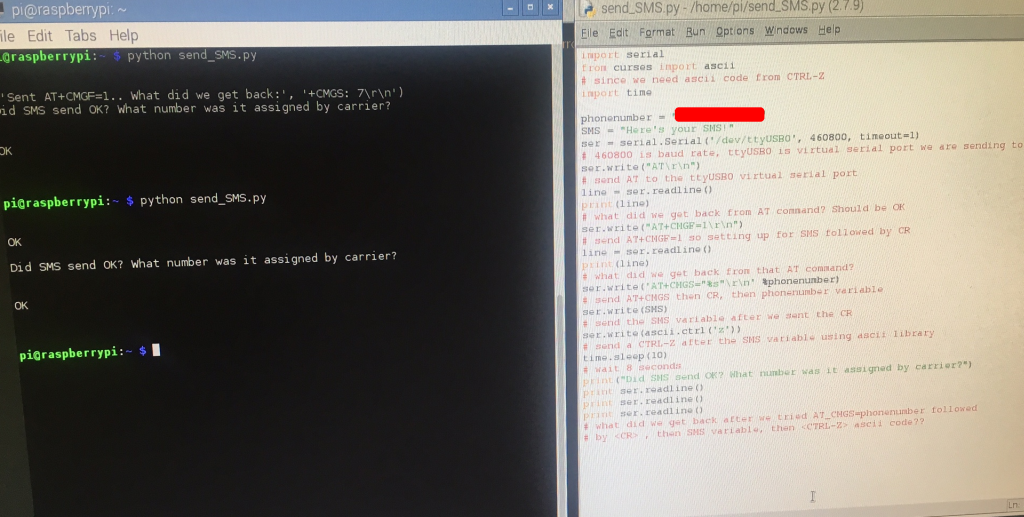
Ok, let's get started with doing this using python instead of cu:
Here's some rough code to send an SMS:
import serial
from curses import ascii
# since we need ascii code from CTRL-Z
import time
phonenumber = #enter phone number to send SMS to
SMS = #enter SMS to send
ser = serial.Serial('/dev/ttyUSB0', 460800, timeout=1)
# 460800 is baud rate, ttyUSB0 is virtual serial port we are sending to
ser.write("AT\r\n")
# send AT to the ttyUSB0 virtual serial port
line = ser.readline()
print(line)
# what did we get back from AT command? Should be OK
ser.write("AT+CMGF=1\r\n")
# send AT+CMGF=1 so setting up for SMS followed by CR
line = ser.readline()
print(line)
# what did we get back from that AT command?
ser.write('AT+CMGS="%s"\r\n' %phonenumber)
# send AT+CMGS then CR, then phonenumber variable
ser.write(SMS)
# send the SMS variable after we sent the CR
ser.write(ascii.ctrl('z'))
# send a CTRL-Z after the SMS variable using ascii library
time.sleep(10)
# wait 10 seconds
print ser.readline()
print ser.readline()
print ser.readline()
print ser.readline()
# what did we get back after we tried AT_CMGS=phonenumber followed
# by <CR> , then SMS variable, then <CTRL-Z> ascii code??
GitHub here: https://github.com/nksheridan/elephantAI/blob/master/test_send_sms.py
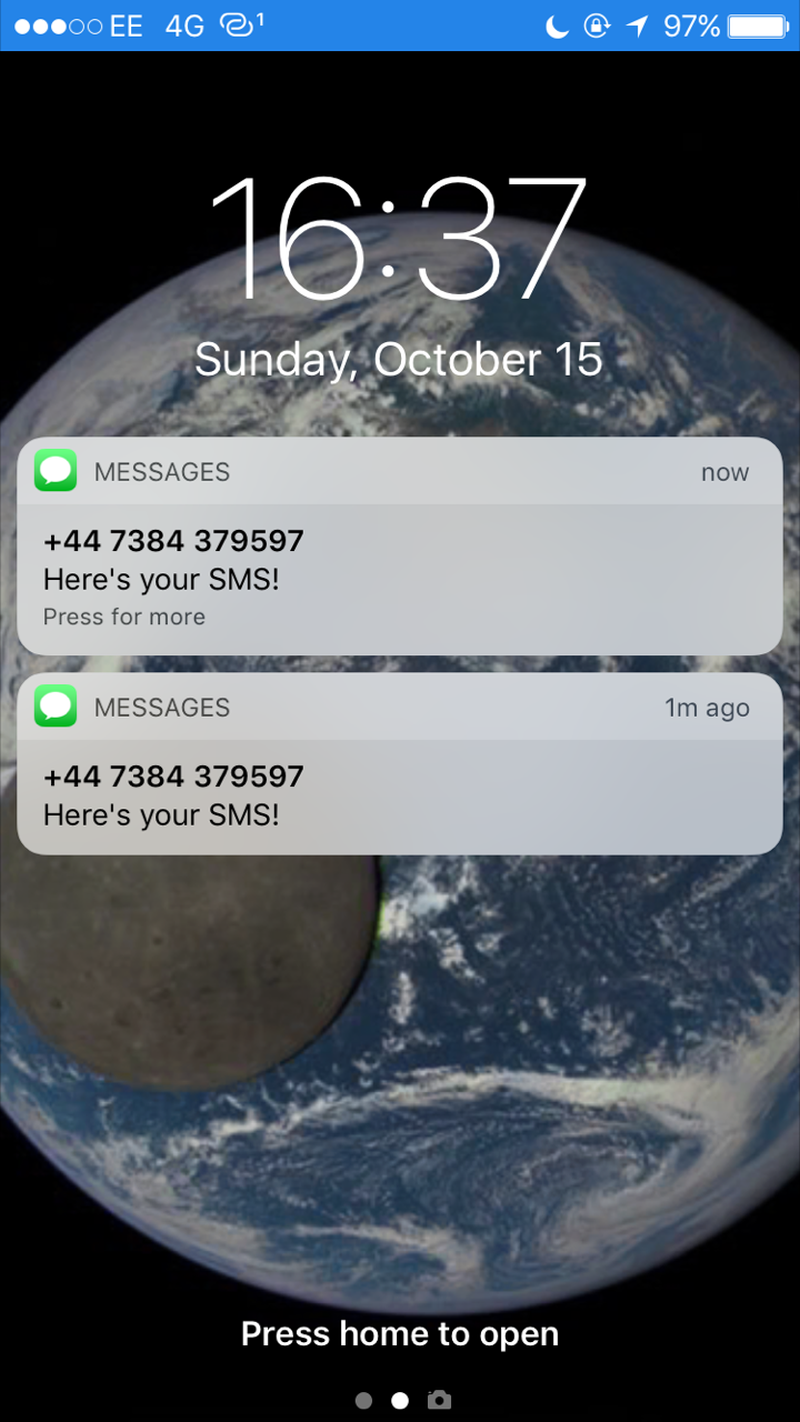
So, after running that, we are able to send an SMS! The phone numbers have to be entered in + then country code, then number format e.g +441234123123
CONCLUSION
So we are all ready to deploy the E3531 as a mobile connectivity solution to the elephant detection devices, and we've got the code we need to notify local people via SMS of elephants being present!
We'll cover using PPP to alert people via twitter in another log (if there's time, or as a future development). In this PPP scenario, we'd could send tweets (or DMs) which included the images of suspected elephants to the local people (users). We could also send this data to a computer in the village that would plot the location of elephants onto google maps/custom maps. In addition, the computer could output to a big physical map sign containing LEDs corresponding to elephant detection devices (these lighting up!). This computer again could comprise a raspberry pi!
In a more advanced PPP scenario I have envisaged, the input of local people could be leveraged to improve the accuracy of our elephant detector by enabled a supervised training system. Here's what it would look like:
1. Elephant detector tweets/DMs image of suspected elephant
2. Local people tweet back with hashtags #yeselephant #noelephant #type_is_lone #type_is_calf
#type_is_herd #type_is_male #type_is_female according to what they identify in the image
3. Database of images containing elephants confirmed by users is created by elephant detection device
4. Images being stored along with their class labels that were provided via the hashtags (e.g. #type_is_calf , #type_is_herd etc.)
5. On a weekly or monthly basis, the elephant detection devices will upload their databases of images to the cloud (e.g. to an Amazon EC2 virtual machine)
6. Transfer learning will be performed on the virtual machine using our existing dataset with these additional images. Thus improving the accuracy of our elephant detector model!
7. The new model will be sent to the elephant detection device from the cloud-based virtual machine, and be used for future detection.
This process will be repeated on a weekly or monthly basis, thus providing on-going improvements in accuracy of the elephant detector!
* please see the future directions log for this and other improvement ideas!
 Neil K. Sheridan
Neil K. Sheridan
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.