After receiving the card I took a look at the website and saw a firmware update utility (FAFWUpdateTool_v10004) and from my previous research this was possibly the key to figuring out more to this device. So I installed it and read through the documentation provided on the site.
Before actually running the utility however I figured I would look at the card as it opens on my Windows 8.1 laptop.
The first thing that I noticed was that it was formatted in FAT32 and it looked like your regular sd card, with one exception.. some hidden folders.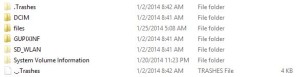
Particularly the hidden one named "SD WLAN", which once opened had one file that really intrigued me, the "CONFIG" file. After opening it up I noticed there were many options and after Googling, many more Official Here andMore Here. So I went about editing it to see what would happen. I wanted it to connect as a client on my network, so I didn't have to connect to it, as the default setting is access point, so I changed APPMODE to 5, changed APPSSID to match mine, and changed APPNETWORKKEY to also match. Next, I found that the unofficial sources stated that there was also a COMMAND function, so I figured "help" might be a good start. I then left everything else alone, then saved and safely removed and reinserted.
My config file looked like the following:
CIPATH=/DCIM/100__TSB/FA000001.JPG
APPMODE=5
APPSSID=MYNETWORKSSID
APPNETWORKKEY=NETWORKKEY
VERSION=F24A6W3AW1.00.04
CID=02544d53573038470750031fac00cc01
PRODUCT=FlashAir
VENDOR=TOSHIBA
COMMAND=help
*note that network key will automatically be *'d out on reboot of card.
After rebooting the card I noticed it showed up on my network, at this point I accessed its web page and was greeted
with the webpage, which was useless.. I wanted to know where the command output was being written to, after digging through the files, I went back to Google, which led me back to the unofficial link above for extrud3d.com (thanks for your help guys).
Anyways, after navigating to /IPADDRESSOFFLASHAIR/eva.cgi, I was presented with a list of the commands:
> help
help show help
version show version
mod Modify Memory
dump Dump Memory
stat show status
ip Address Setting
ping ping
reboot reboot system
macsend MAC frame send
setup TELEC command
send TELEC command
stop TELEC command
show TELEC command
deauth deauth command
print console output
srom SPI ROM access
sleep sleep setting
fat file system
wlan Wireless LAN control
dhcpd DHCP server
dhcpc DHCP client
nbios NetBios service
wps Wi-Fi Protected Setup
sd SD Card Access
http HTTP Client
httpd HTTP Daemon
rfic set RF-IC serial data rfic
iperf Measuring performance
sysclk change System clk
ps ps [on/off] pw pw
pio pio
netlog log
d
followed by what looked like a startup log. Now I was getting somewhere..
So I tried a number of the commands, but I had little luck here and there as they appeared to be very limited as I could not see what the arguments/flags were as appending "-h" or "?" almost never returned anything. It is also a pain because you have to edit the CONFIG file, save, safely remove, pull out, put back in, wait for it to reconnect to the network, then refresh the page each time you want to run a command.
From the interesting ones above, what I could get to run and ascertain:
help command showed the above commands.
version command printed version information.
mod command appeared to be a write function. (I believe this and dump is to some flash storage because it returned all 0's)
dump command returned what appeared to be memory addresses and lengths followed by raw binary output.
stat command returned wlan stats, like signal strength, rx and tx packets etc.
ip command appeared it was to setup ipaddress settings.
ping command pinged address in argument.
fat can do mkdir, cp commands etc, so it is access to the sd card flash system.
all the other ones for the most part required arguments and/or flags that I did not know or returned nothing..
Next thing to do was update the firmware and see what would happen, just as I had researched it added a file which gets deleted on...
Read more » Chris Jones
Chris Jones

 Nathan
Nathan
 fdufnews
fdufnews
 Elbert
Elbert