Physical security is becoming a lot more important. Now that things like cryptocurrency can be hacked from a computer or stolen from a person using a physical wallet through violence (kidnapping etc) a new model of security is required.
It used to be that what was stored on your computer wasn't very important and needed very little security. Unless you were a company who could afford security guards on 24/7 to protect the information, you couldn't get security for your information. Now, we carry access to all of our accounts in our pockets, and they have systems that can defend against basic theft. If someone steals your phone, they probably can't get anything from it due to encryption and security systems.
Bitcoin and other cryptocurrencies have also changed the value of what you carry. Instead of just being private information such as photos and browsing information which only has value to you, your phones and other devices can now carry massive amounts of value in the form of cryptocurrencies. This has changed the calculus of crime. While a hardware wallet can be secure from direct theft, criminals can now simply attack you the person to get into the device.
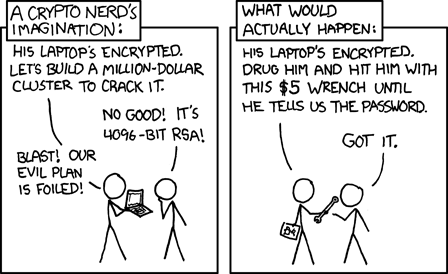


What we need now is not a security model based on secret information which is known by you, but a model based on mechanisms which are self-operating and independently verify their own security systems. In this idea, a computer (or microcontroller) is responsible for it's own security. With this, you might design a system that will lock down in insecure instances and only unlock once the insecurity has been resolved. This has been done, in very expensive systems for corporations and well-off individuals.
Unfortunately, this is also incomplete, since you don't want a system to wipe your bitcoin wallet whenever there is a power outage or if you're friend comes over to water your plants while you're on vacation.
This leads into the security model that I've designed and been using for a few months. I call it the Pinball model because it's designed to keep my systems secure using the concepts of "tilt", "bumpers", "score" and "balls".
Tilt is the most important part of the model. In pinball, it's common to "tilt" the machine if you hit it to hard trying to influence the movement of the ball. The machine has a relatively simple motion sensor inside, which when it detects a trigger it does some set of actions with the effect of punishing the player for the tilt, usually locking out the controls or deactivating the score bumpers for a moment. This effect though is not as simple as "moving the machine is a tilt". Usually there is a window of which the device does not respond to the movement. This flexibility of what occurs with a tilt and what triggers it is the main inspiration for how the model operates.
In my implementation, I have a number of small microcontrollers and sensors connected to my secured system. They connect in various ways including network, USB and even internal. These are all inter-connected and are looking at their own security state. Each one has a key which can be used with a number of others to decrypt the master key.
A major feature of this system is that not all keys are required to decrypt the master key. Effectively each controller can contribute to decrypting the master key, but no one controller is required for it. Each controller then runs it's own security tests. This varies from detecting if the computer they're connected to has been moved, opened, or unpowered, to whether or not the front door is open. Each element of the security network is able to therefore signal a "tilt" when it fails it's security test. Some controllers will also rely on the results of other sensors or controllers out in the network. Enough tilts and a given task becomes impossible to do due to the inability to recover the master key. Each tilt can be recovered only by the original controller and cannot be filled by another controller, or the user's own knowledge.
This model allows a user to secure a system without relying on personal knowledge or a single device's security. By doing this, I hope to build a system that remains secure even if you are kidnapped or threatened (which should reduce or remove that from happening). I'll go into more detail on each element of the model and how they provide a completely secure model in future posts.
In addition, I have a working implementation of this model. Unfortunately, it is not yet robust or generalized enough for a complete release, however, as I rebuild the system into a generalizable and implementation independent system, I will release it publicly on Github and here.
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.