List of goals for this project:
- Automatically connect to whitelisted APs with "open" configuration.
- Use WiGLE
- Automatically accept terms of service for APs that require clicking "I Agree" in browser window.
- Establish VPN.
- Autoconnect VPN.
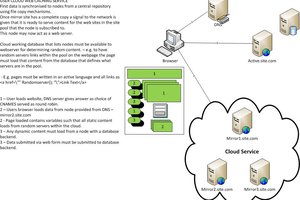
- Receive GPS and send location data to home server.
- Enclose in nondescript project box with provisions for multiple antennas, Ethernet port, USB host port, USB micro for charging.
- Pelican 1060
- Extended Feature Set:
- Wardrive?
- Piratebox?
- Bluetooth?
- Mesh?
- Camera?
- RTL TCP Server?
- ToR?
 load.nikon
load.nikon


 Craig Hissett
Craig Hissett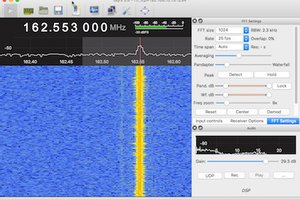
 worsthorse
worsthorse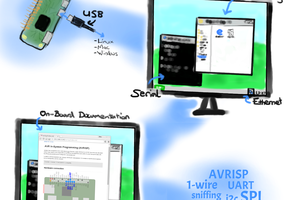
 Danny
Danny