
Redford did a whole lotta work reverse engineering the BIOS code and figured out that most of the interesting stuff (password check, challenge/response for lost password) is actually done by something off the main x86 processor. We figured out that it's probably the EC/KBC (Embedded/Keyboard Controller) which we found earlier on the laptop mainboard.
The controller is a generic microcontroller, with a bit of a twist - it's a pretty obscure one. It's labeled as a TMP87PH48, which is a programmable version of the TMP87CH48. Never heard of it? We neither.
As it turns out, it's based off the “TLCS-870" architecture, which is kind of like-ish to a weird Z80. We quickly skimmed through some specs we found for the CPU core itself, decided that it's probably powerful enough to run password verification code, and started figuring out what to do next.
Usually, the CH48 model is a mask-ROM model. Thankfully, our laptop shipped with the PH version, which is one-time programmable by the user. And, thanks to that, it actually contains a programming and verification interface. As it turns out, if you pull one of its' pins low, it can be treated as a generic PROM chip. This means we can read out the code from the chip just by asserting a 15-bit address on a port and reading out 8 bits of data on another port. Easy!
Since I didn't have an oldschool (EE)PROM programmer on hand, I quickly hacked together my own, the result of which can be seen in the picture at the beginning of this article - most of the jumper cables are address and data lines, some are just used to strap other pins to +5V and GND (a requirement from the chip datasheet). The home-etched board contains the EC from the laptop, soldered out with a Hot Air gun, then soldered into the board. The design of this (generic) board was done in KiCAD.
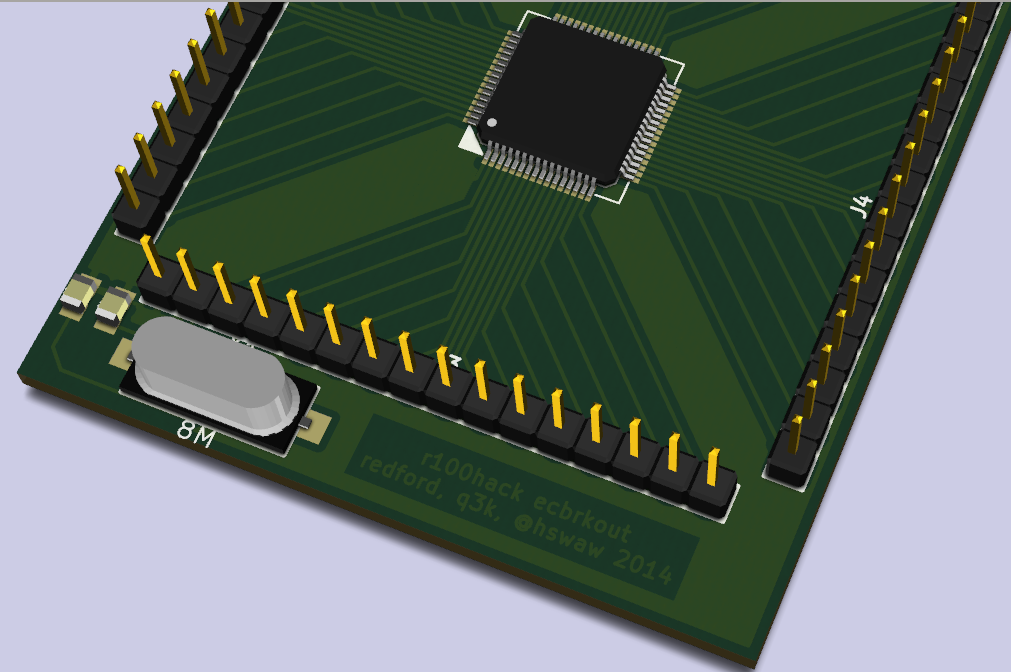
The programmer/reader interface is very basic - just a Spartan6 FPGA with a bit of Verilog to receive an address (one byte, then multiplied by 0xFF) over UART from a PC, then reply with 256 bytes of data read from the EC starting from the requested address. The code is available at https://code.hackerspace.pl/q3k/ec-prom-dump/. A quick and dirty Python script dumped all 32kbytes of memory a few times to check for read errors.
The code could've easily be written for a microcontroller with a lot of I/O pins (or with a I/O multiplexer) - I just had an FPGA on me, so that's what I chose. And, of course, a cheap EEPROM programmer would also do the job.
And then, after all of this, we saw dumps. Bitflipped, but statistical analysis will help us with this. As far as I know, Redford has already combined 16 read passes into one file which shows a high likelyhood of 100% accuracy.
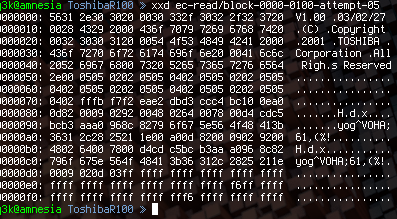
Now for more reverse engineering. We still don't know where the actual password is stored - this uC does not have any nonvolatile memory...
 q3k
q3k
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.
Hello, I read with interest the following in your blog post:
"As it turns out, if you pull one of its' pins low, it can be treated as a generic PROM chip. This means we can read out the code from the chip just by asserting a 15-bit address on a port and reading out 8 bits of data on another port.".
Which pins do you 'pull low' and then 'read' from. Do you have a tech lit reference I could learn more from? I've already been through the
Toshiba "8 Bit Microcontroller TLCS-870/C Series" guide (and similar) Nothing on this there. Thanks, Application: I'm into VFDs and I'd like to bypass the ROM mask on a TMP86CM74AFG. Any tips?
Are you sure? yes | no