Long ago when I started prototyping ideas, I was using a $89 FPGA Board (Avnet LX9 board). The ChipWhisperer system has always supported this board, but it's not as well documented as my newer, fancier hardware. I wanted to make a log post to demonstrate this system still working, as if you have a 'passing interest' in side channel analysis (SCA), this setup is a MUCH cheaper method of getting started. It's a lot slower than the full ChipWhisperer Capture Rev 2 hardware and due to the smaller FPGA doesn't support any features besides simple analog capture. It's all the same FPGA code (using my project management described in another log file), just with stuff missing to fit into the LX9 device.
This isn't the only cheap option, the Papillio Pro can also be used too which is even cheaper ($85), and there is a cheaper OpenADC you can build with more limited sample rate called the OpenADC Lite. Here's some of the cheap options:
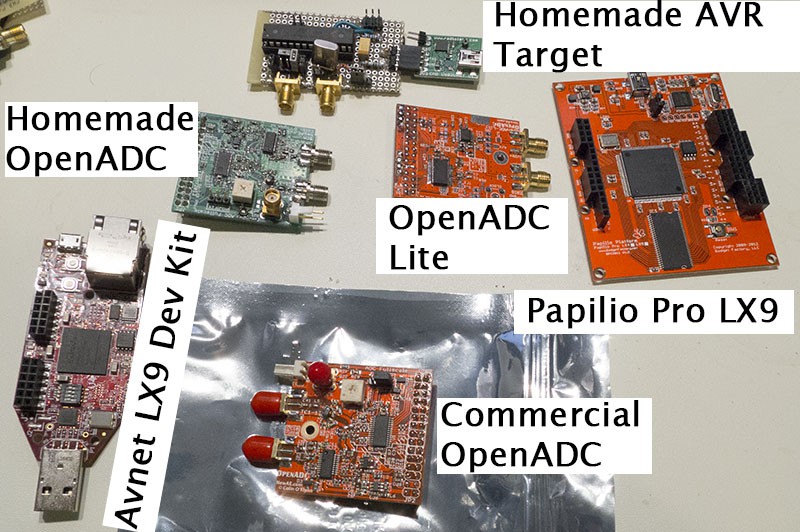
Setting up the LX9 board with the homemade OpenADC looks like this, where the total cost will be in the $150 vicinity ($89 for FPGA, about $50 to build the OpenADC, $10 for random stuff):

You can also build an AVR target on a breadboard, here shown with a 'commercial' OpenADC module:
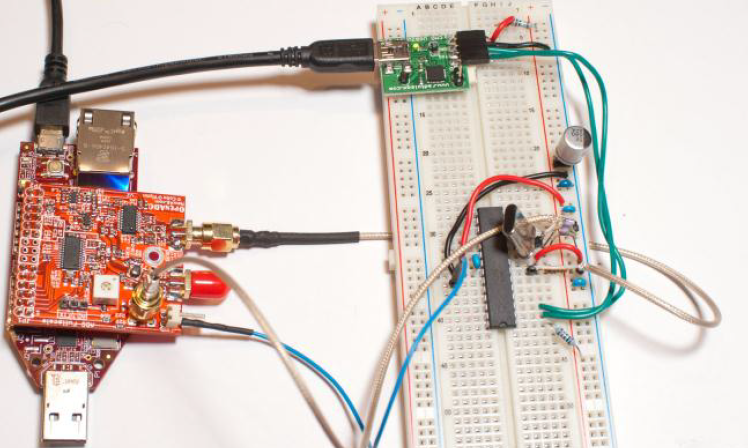
For your viewing pleasure here is a video version of the complete setup & attacking AES on the AVR. You can see it still only takes about 30 measurements of the power consumption to break AES, so it's the same resulting attack performance as my full-blown hardware. The main difference you see here is the slower capture, but it still takes under 2 minuites to perform all 50 power measurements, so it's far from unreasonable speed!
 Colin O'Flynn
Colin O'Flynn
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.