 OK folks, let's get it going! Welcome to the Hack Chat, I'm Dan, and Dusan and I will be moderating today as we welcome Chris Poore for a chat about RF Hacking!
OK folks, let's get it going! Welcome to the Hack Chat, I'm Dan, and Dusan and I will be moderating today as we welcome Chris Poore for a chat about RF Hacking!
Hi Chris, thanks so much for your time today. Can you tell us a little about your interest in RF and reverse engineering?
 Hi everyone!
Hi everyone!
![]() @anarchoN3rd : today the speaker is @Chris Poore
@anarchoN3rd : today the speaker is @Chris Poore
 Sure, I work at a cybersecurity company called Assured Information Security (AIS). So it mostly originates from what we do.
Sure, I work at a cybersecurity company called Assured Information Security (AIS). So it mostly originates from what we do.
 @anarchoN3rd -- Chris Poore is the invited guest, but it's really just a chat among friends. This week it's about RF Hacking
@anarchoN3rd -- Chris Poore is the invited guest, but it's really just a chat among friends. This week it's about RF Hacking
 We provide government and commercial customers with industry leading cyber and information security capabilities specializing in research, development, consulting, testing, forensics, remediation and training.
We provide government and commercial customers with industry leading cyber and information security capabilities specializing in research, development, consulting, testing, forensics, remediation and training.
 I specifically work on a team that identifies weaknesses, verifies systems, and provides solutions to customers.
I specifically work on a team that identifies weaknesses, verifies systems, and provides solutions to customers.
 We’re often provided with systems or tasked to look at targets and we have to characterize their operation and assess their security.
We’re often provided with systems or tasked to look at targets and we have to characterize their operation and assess their security.
 What tools do you use?
What tools do you use?
 What are common vulerabilities you find?
What are common vulerabilities you find?
![]() @Dan Maloney is there a video I am supposed to be seeing or just a chat?
@Dan Maloney is there a video I am supposed to be seeing or just a chat?
 I'm quite curious on where do you start. Besides the usual FCC info :)
I'm quite curious on where do you start. Besides the usual FCC info :)
 Well, it's a pretty diverse team and I specialize in topics related to RF technology
Well, it's a pretty diverse team and I specialize in topics related to RF technology
 @anarchoN3rd - just text. We roll old school here ;-)
@anarchoN3rd - just text. We roll old school here ;-)
 So pretty much anything with a computer that has a wireless aspect, I've looked at
So pretty much anything with a computer that has a wireless aspect, I've looked at
 That covers a lot of tools as you can imagine
That covers a lot of tools as you can imagine
![]() Does your job also include probing inadvertent emissions security, like project Tempest?
Does your job also include probing inadvertent emissions security, like project Tempest?
 We've had people work on projects like that and are familiar with the technology
We've had people work on projects like that and are familiar with the technology
![]() @Dan Maloney that's pretty cool, actually. Just misunderstood the assignment ;)
@Dan Maloney that's pretty cool, actually. Just misunderstood the assignment ;)
![]() I have question about RF. I moved into a place that has an alarm system. I didn’t want it. But would like to play with the sensor they left. Door/movement/water. Is there a way to use these devices.
I have question about RF. I moved into a place that has an alarm system. I didn’t want it. But would like to play with the sensor they left. Door/movement/water. Is there a way to use these devices.
![]() Does it have to be only about computers emitting data, or can we include other EMI as well, from said tempest to eg. machinery health detection by detection sparking? Detection of cameras and other devices by their EM signatures?
Does it have to be only about computers emitting data, or can we include other EMI as well, from said tempest to eg. machinery health detection by detection sparking? Detection of cameras and other devices by their EM signatures?
![]() I too am curious about devices such as those that are part of SimpliSafe.
I too am curious about devices such as those that are part of SimpliSafe.
 With certain devices you can repurpose them, but it will usually take a good understanding of the underlying technology
With certain devices you can repurpose them, but it will usually take a good understanding of the underlying technology
![]() @Thomas Shaddack If a tree falls in a wood and there IS someone to hear it ...
@Thomas Shaddack If a tree falls in a wood and there IS someone to hear it ...
![]() Do you use GNURadio in your work?
Do you use GNURadio in your work?
 There are all these different applications of RF and security so I'm here mostly to promote a project I've been working on that kind of brings it all together in one place
There are all these different applications of RF and security so I'm here mostly to promote a project I've been working on that kind of brings it all together in one place
 Do you ever work with 24GHz stuff and do you have any low cost hacks for signal reception?
Do you ever work with 24GHz stuff and do you have any low cost hacks for signal reception?
![]() @chris where would be a good place to find information. I’m pretty sure they are using 915 freq. but with having limited tool to analyze the RF what other option does someone have to play around with the devices?
@chris where would be a good place to find information. I’m pretty sure they are using 915 freq. but with having limited tool to analyze the RF what other option does someone have to play around with the devices?
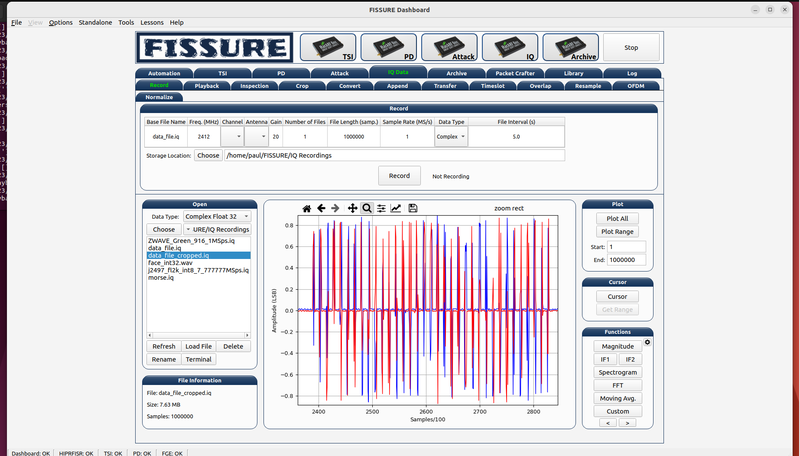
 I'm quite involved with GNU Radio, just got back from GRCon. The project I'm promoting is an RF framework called FISSURE: https://github.com/ainfosec/FISSURE
I'm quite involved with GNU Radio, just got back from GRCon. The project I'm promoting is an RF framework called FISSURE: https://github.com/ainfosec/FISSURE
 Fissure? I have installed it, Need a bit of a tutorial on it to be honest. Unsure of the correct order or working
Fissure? I have installed it, Need a bit of a tutorial on it to be honest. Unsure of the correct order or working
 @Chris Poore What made you decide to build FISSURE? It seems like a pretty refined framework for modular plugins.
@Chris Poore What made you decide to build FISSURE? It seems like a pretty refined framework for modular plugins.
 I haven't been too involved with the 24 GHz stuff, mostly due to hardware restrictions.
I haven't been too involved with the 24 GHz stuff, mostly due to hardware restrictions.
 @Brendancontest Pop the gizmo open, look for the chip set, order the dev kit from the manuf.
@Brendancontest Pop the gizmo open, look for the chip set, order the dev kit from the manuf.
![]() Thank you @chris. I’ll read through that and start there to see how the team worked with with the RF.
Thank you @chris. I’ll read through that and start there to see how the team worked with with the RF.
![]() Is Ubuntu obligatory? How much trouble should I expect on Arch/Artix?
Is Ubuntu obligatory? How much trouble should I expect on Arch/Artix?
 @salec should work OK on arch
@salec should work OK on arch
![]() @duckpaddle I’ll try that never though of ordering a dev kit.
@duckpaddle I’ll try that never though of ordering a dev kit.
 Let me just dump some information on FISSURE to get people in the loop
Let me just dump some information on FISSURE to get people in the loop
 FISSURE is an open-source RF and reverse engineering framework that contains hooks for detection, classification, protocol discovery, attack execution, vulnerability analysis, automation, and AI/ML.
FISSURE is an open-source RF and reverse engineering framework that contains hooks for detection, classification, protocol discovery, attack execution, vulnerability analysis, automation, and AI/ML.
 Its original purpose was to speed up the characterization of signals and the identification of vulnerabilities in RF protocols, waveforms, and devices.
Its original purpose was to speed up the characterization of signals and the identification of vulnerabilities in RF protocols, waveforms, and devices.
![]() Is this mostly an integration of other tools or new work that overlaps?
Is this mostly an integration of other tools or new work that overlaps?
 But it has evolved to consolidate all-things RF: software modules, radios, protocols, signal data, scripts, flow graphs, reference material, and third-party tools
But it has evolved to consolidate all-things RF: software modules, radios, protocols, signal data, scripts, flow graphs, reference material, and third-party tools

https://hackaday.com/2022/08/27/introducing-fissure-a-toolbox-for-the-rf-hacker/
Introducing FISSURE: A Toolbox For The RF Hacker
No matter what the job at hand is, if you're going to tackle it, you're going to need the right kit of tools. And if your job includes making sense out of any of the signals in the virtual soup of RF energy we all live in, then you're going to need something like the FISSURE RF framework.
 It's a place to test out new things but also quickly access things you have relied upon in the past
It's a place to test out new things but also quickly access things you have relied upon in the past
 How are you performing signal classification out of interest, i assume that means determining if a signal is say FSK,PSK,...? Is that via ML or..?
How are you performing signal classification out of interest, i assume that means determining if a signal is say FSK,PSK,...? Is that via ML or..?
![]() Is this legal for us (foreign) civilians? Looks like something which could be under export restrictions.
Is this legal for us (foreign) civilians? Looks like something which could be under export restrictions.
 Would Fissure work with RFID protocols?
Would Fissure work with RFID protocols?
 What hardware do you need to run FISSURE?
What hardware do you need to run FISSURE?
 A lot of what is included in the software for FISSURE now, is mostly examples of how to certain things. It's still pretty early going in the project but I wanted to make it available so people can take a look at and see what it is about
A lot of what is included in the software for FISSURE now, is mostly examples of how to certain things. It's still pretty early going in the project but I wanted to make it available so people can take a look at and see what it is about
 So research areas like signal classification are not fully fleshed out as a finished product, but as I (and others) work on it, there is a place to put our code
So research areas like signal classification are not fully fleshed out as a finished product, but as I (and others) work on it, there is a place to put our code
 that's the framework aspect of it
that's the framework aspect of it
 So is this a framework in the sense of Metasploit where it provides pre-packaged tools, or a framework like Nix where it provides the tools to build the tools?
So is this a framework in the sense of Metasploit where it provides pre-packaged tools, or a framework like Nix where it provides the tools to build the tools?
 many of these technical areas have been performed ten times over by people across the world but this software provides a place to swap out techniques and use what works best for people
many of these technical areas have been performed ten times over by people across the world but this software provides a place to swap out techniques and use what works best for people
![]() A top down design, and "down" may vary
A top down design, and "down" may vary
 The framework is meant to flexible and inclusive to most people, so it uses (or could use) most commercial SDRs
The framework is meant to flexible and inclusive to most people, so it uses (or could use) most commercial SDRs
 Technically electromagnetic but not classified as RF have you looked into hacking of potential LASER comms from orbit by satellites or is the directionality the limiting factor here?
Technically electromagnetic but not classified as RF have you looked into hacking of potential LASER comms from orbit by satellites or is the directionality the limiting factor here?
 or other types of hardware besides SDRs, like 802.11 adapters or zigbee sniffers
or other types of hardware besides SDRs, like 802.11 adapters or zigbee sniffers
 Cool got a preferred zigbee sniffer?
Cool got a preferred zigbee sniffer?
 I see some esp32 modules in there, that used for BLE sniffing?
I see some esp32 modules in there, that used for BLE sniffing?
![]() @kjansky1 I'd guess once you get it sampled into the machine it's the same. Quite some similarity these days between encoding for rf and for wire/fiber and I can imagine it will be the same for free-space laser.
@kjansky1 I'd guess once you get it sampled into the machine it's the same. Quite some similarity these days between encoding for rf and for wire/fiber and I can imagine it will be the same for free-space laser.
 bt/ble
bt/ble
 There's a lesson on RFID included with FISSURE if you want to read up on it. It can be used for RFID, there only a few RFID tools included right now though
There's a lesson on RFID included with FISSURE if you want to read up on it. It can be used for RFID, there only a few RFID tools included right now though
![]() Is it I/Q only or can it take even a raw sampled waveform eg. from an oscilloscope?
Is it I/Q only or can it take even a raw sampled waveform eg. from an oscilloscope?
![]() Are some protocols already included? I am personally interested in DECT.
Are some protocols already included? I am personally interested in DECT.
 FISSURE has a couple pieces, it's mostly a GUI with menu items and tabs. The menu items are filled with third-party tools, standalone flow graphs, help items, reference material.
FISSURE has a couple pieces, it's mostly a GUI with menu items and tabs. The menu items are filled with third-party tools, standalone flow graphs, help items, reference material.
 So there are third-party tools for Wi-Fi, bluetooth, and other protocls
So there are third-party tools for Wi-Fi, bluetooth, and other protocls
 But the tabs below are more tailored towards making sense of signals and characterizing them
But the tabs below are more tailored towards making sense of signals and characterizing them
 recording signals, building up a library of information, running attack scripts/flow graphs
recording signals, building up a library of information, running attack scripts/flow graphs
 There's limited DECT included. We initially tested the project with a baby monitor and I know it also installs gr-dect2
There's limited DECT included. We initially tested the project with a baby monitor and I know it also installs gr-dect2
 How about counter-measures like for GPS spoofing.
How about counter-measures like for GPS spoofing.
 FISSURE is pretty modular, most of the signal data is meant to be handled as I/Q data but you could build it out to accept it in other forms
FISSURE is pretty modular, most of the signal data is meant to be handled as I/Q data but you could build it out to accept it in other forms
 If you can think of a way to pass data to a Python component, it can probably be achieved and you can do whatever you want with it from there
If you can think of a way to pass data to a Python component, it can probably be achieved and you can do whatever you want with it from there
 The framework is meant to be transparent so you can edit it on your own
The framework is meant to be transparent so you can edit it on your own
 I am looking into porting Fissure to Nixpkgs. Any tips?
I am looking into porting Fissure to Nixpkgs. Any tips?
![]() Are there lessons on writing modules?
Are there lessons on writing modules?
 There a variety of GPS tools. I've been using a USB GPS receiver to test them
There a variety of GPS tools. I've been using a USB GPS receiver to test them
 I know that's more of a Nix problem, I more meant, is there any stand-out uniquness in the vodebas.
I know that's more of a Nix problem, I more meant, is there any stand-out uniquness in the vodebas.
 There isn't much there for actively generating GPS signals or spoofing, but FISSURE acts as a place to put such tools as they are developed
There isn't much there for actively generating GPS signals or spoofing, but FISSURE acts as a place to put such tools as they are developed
 There are a couple help menu items for adding GUI elements to the dashboard but further documentation on creating standalone components will be released in the future
There are a couple help menu items for adding GUI elements to the dashboard but further documentation on creating standalone components will be released in the future
 and there are other topics like adding attacks, uploading flow graphs/scripts
and there are other topics like adding attacks, uploading flow graphs/scripts
 How about applications for use with coherent multi SDR receivers such as the Kraken..
How about applications for use with coherent multi SDR receivers such as the Kraken..
 I'm a little hesitant in packaging up FISSURE mostly due to all the third-party tools. More needs to be done to isolate the main features in the tabs from all the extraneous software meant for quick access
I'm a little hesitant in packaging up FISSURE mostly due to all the third-party tools. More needs to be done to isolate the main features in the tabs from all the extraneous software meant for quick access
 Right now, FISSURE is designed for kind of a single-computer laboratory setup.
Right now, FISSURE is designed for kind of a single-computer laboratory setup.
 The components communicate to each other over a network and at one time it was distributed across multiple computers in different locations
The components communicate to each other over a network and at one time it was distributed across multiple computers in different locations
![]() Should work in a vm? So long as the sdr can get a passthrough?
Should work in a vm? So long as the sdr can get a passthrough?
 but as far as the radios and RF hardware, it's really just a single assignment to one particular function
but as far as the radios and RF hardware, it's really just a single assignment to one particular function
 in the long-term it will probably change to more a multiple sensor deployment scheme so you could have multiple radios doing multiple things, sending data back over a network
in the long-term it will probably change to more a multiple sensor deployment scheme so you could have multiple radios doing multiple things, sending data back over a network
 so for multi-SDR receivers it might be better to treat it as a new software component and pass the inputs/outputs back to FISSURE
so for multi-SDR receivers it might be better to treat it as a new software component and pass the inputs/outputs back to FISSURE
![]() Looking through the screenshots, what would it take to get a dark theme? 😉
Looking through the screenshots, what would it take to get a dark theme? 😉
 make a python wrapper around whatever is controlling your application
make a python wrapper around whatever is controlling your application
 It's all PyQt
It's all PyQt
![]() Seems like a very cool project and well fleshed out already :)
Seems like a very cool project and well fleshed out already :)
 I can look into different themes
I can look into different themes
![]() I heard about encoding the pulse-per-second sync from GPS into the signal as some weak sequence, and then autocorrelating it out for precision timestamp for syncing data from multiple stations.
I heard about encoding the pulse-per-second sync from GPS into the signal as some weak sequence, and then autocorrelating it out for precision timestamp for syncing data from multiple stations.

 i have it running in VB. seems to work fine.
i have it running in VB. seems to work fine.
 Running in VMs will be tricky with certain types of hardware
Running in VMs will be tricky with certain types of hardware
 Docker can also be a possibility in the future
Docker can also be a possibility in the future
 with the hack rf seems ok. did some captures of a 2.4ghz photographic transmitter.
with the hack rf seems ok. did some captures of a 2.4ghz photographic transmitter.
 At this stage, I'm working on getting more information out to the public and I'm looking for people to provide suggestions
At this stage, I'm working on getting more information out to the public and I'm looking for people to provide suggestions
 There is a discussions tab in the GitHub
There is a discussions tab in the GitHub
 Would be interesting to see what could be done with Starlink signals
Would be interesting to see what could be done with Starlink signals
 There is a Discord server if you want to chat about anything https://discord.gg/JZDs5sgxcG
There is a Discord server if you want to chat about anything https://discord.gg/JZDs5sgxcG
![]() Is the GUI key, or can everything also be accessed via a CLI?
Is the GUI key, or can everything also be accessed via a CLI?
![]() @kjansky1 could be fun to have a grid of ground stations and use the starlink birds (and/or the gnss ones) as sources of known signals for atmospheric/ionospheric tomography. weather radar on steroids.
@kjansky1 could be fun to have a grid of ground stations and use the starlink birds (and/or the gnss ones) as sources of known signals for atmospheric/ionospheric tomography. weather radar on steroids.
 Dan Maloney
Dan Maloney
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.