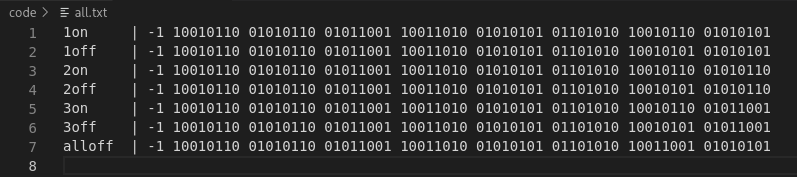
Step 1: All of the the payloads grouped in to a single file. Then I separated the initial pause and 64 bits that follow, grouped by 8 bits. Notice some similarities. The first 52 bits after the initialisation are the same on each command
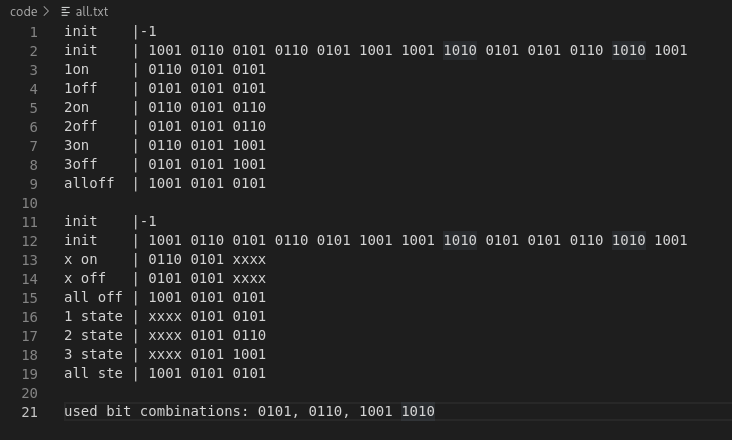
Step 2: Further dissection shows some more patterns starting to emerge
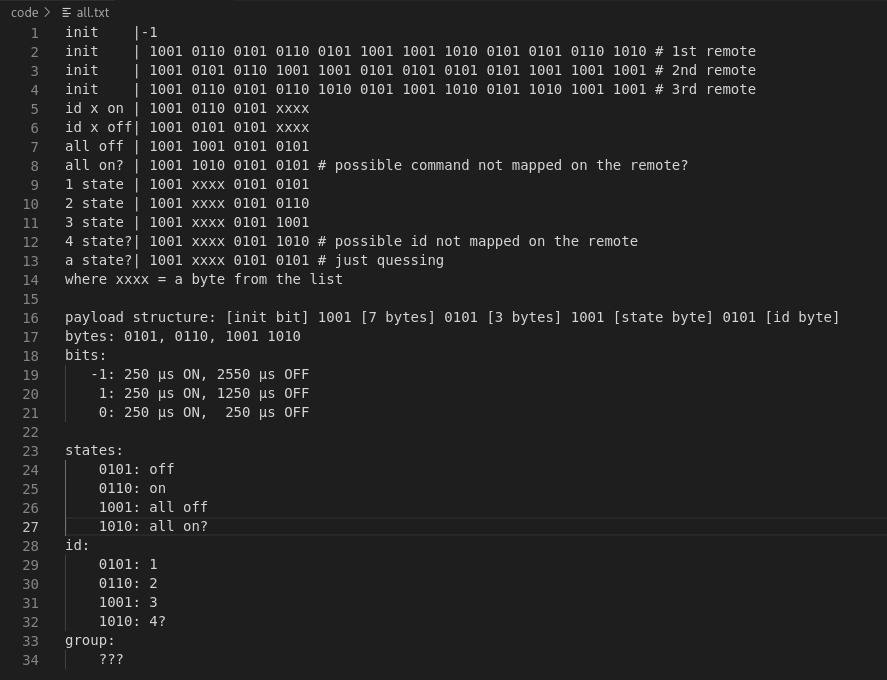
Step 3: Repeat the same process for two more remotes all of which are in different groups. The product packaging says theres 32 different memory slots so there's possibly 4 IDs and 8 groups?
 suikale
suikale
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.