
Thanks to precise placement decision, Beacon provides consumers specific info and also solutions on their smart device at the point of sale. We describe the beacon modern technology solutions and also iBeacon technology to you!
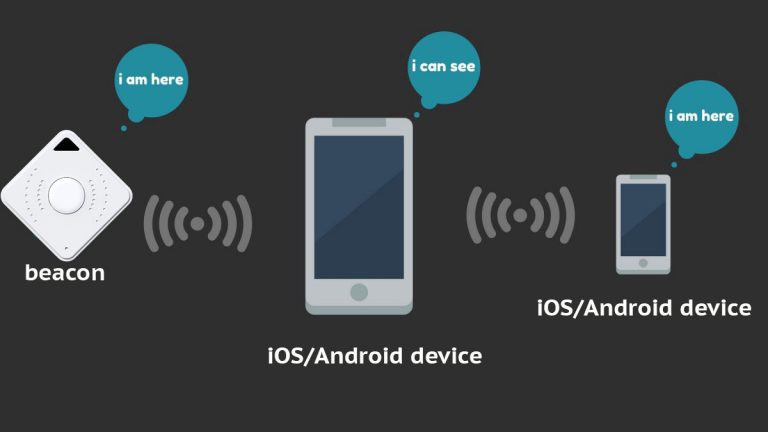
The new "beacon" in the marketing skies is brought on by little radio transmitters, the iBeacons. The word sign comes from the aeronautics and delivery industry and also means something like radio beacon or beacon. Apple presented iBeacon last year with the launch of its iOS 7 mobile os. It is to broaden the location services of their mobile os iOS. It starts where GPS and various other location systems no longer function, inside structures.
What are beacon modern technology options and just how do they function?
Beacons are a few centimeters little transmitters that not do anything but send a "beacon" of little information packages in close quarters. This basically has 3 items of details: a UUID (Widely One-of-a-kind Identifier), which serves to distinctly recognize the sender, and also 2 items of details regarding the position, major and also small.
In simple language: "I am X and also I am in the New York City Apple Shop (Major) in the iPads (Minor) division." Apple approximates the series of this sign to be some 10 meters. The maximum range specifies the border in between entering as well as leaving the active location. There are 4 areas within this area: Immediate = The receiver is likely to be a few centimeters far from the iBeacon. Near = The range is about 1-3 meters. Much = The signal of the iBeacon is gotten, yet it can not be identified whether it remains in the Near or Immediate zone. Unknown = The distance of the iBeacon can not be established whatsoever.
A procedure is made use of that is based upon Bluetooth Low Power (BLE), an innovation that consumes extremely little power. Which had to do with it. That does not sound particularly exciting, specifically not innovative. It obtains actually intriguing when iBeacons enter contact with a recipient-- e.g. B. to a Bluetooth 4.0-capable mobile phone on which a proper app is set up. If a customer is within the series of a beacon, the app on his smartphone can be used to provide him with location-based deals or info.
Legal elements of Beacon technology services
iBeacons just send out information about their identification as well as their setting in the room. They do not accumulate individual data and are therefore of no lawful significance. Data protection problems just end up being pertinent in connection with the information exchange between the server as well as the application of the provider.
Business are no question responsible for bringing their requirement for details about existing or possible clients right into line with the legal framework. The emphasis is on transparency and detailed information for customers. But there is also no doubt that the customer is accountable. Of course, they can make a decision whether to set up an app and accept accessibility different information. If you decide to do this, you must put in the time to read the customer agreements as well as permit terms in order to make an aware as well as understanding choice.
IBeacon modern technology has the prospective to develop itself as one of the basic modern technologies in the near future. Market researchers see the positioning of this technology at the POS as having terrific possible for market growth. And innovative minds are already establishing composite systems in which, for example, B. Area services such as GPS, WLAN as well as signs can be combined for ideal use. What influence this will have on potential users and on the marketplace is currently not direct. However it is definitely fascinating to see the more advancement.
What about iBeacons and also data defense? Review the interview with Frederick Richter, legal representative as well as board member of the Information Defense Foundation.
Frederick Richter is Head Of State of the Data Defense Structure in Leipzig. The Information Security Foundation was founded by the Federal Republic of Germany to enhance the populace's ability to safeguard its very own information with education and training. EXPERT SYSTEM asked him regarding the lawful aspects of the brand-new beacon innovation remedies.
Mr. Richter, do you see any kind of issues regarding the information defense of users with the existing condition of the brand-new beacon modern technology remedies?
As so frequently, issues with shielding customer information likewise emerge with the new iBeacon modern technology just when a number of types of information are linked. The presentbeacon devices just send details about their own place. These data are neither personal nor personal. When checking out the sending out beacon alone, there is, as a result, no worry. It can be more difficult if the applications are additionally watched on the mobile phone dealt with by the beacon. Since these can tell the operator of the sign a whole lot concerning the user. The customer needs to constantly be clear about this to make sure that he can decide whether he wants to proceed making use of the corresponding application on his phone. The suppliers need to as a result plainly connect what they wish to do with the individual information.
Technical contribution: Signs innovation services-- Danger to data protection?
The networking of daily items is the next big thing in the digital globe. Along with networked tvs and also fridges, smart power meters are currently likewise part of our daily life. With the billion-dollar acquisition by Nest, Google is positioning itself on the marketplace for networked gadgets. Samsung and LG likewise see terrific possible in the "Internet of Things" as well as are already establishing their own systems for the networked house. Market researchers forecast around 26 billion gadgets linked to the Internet by 2020. In addition to "intelligent" home products, the networking of items in brick-and-mortar retail is specifically fascinating for marketer. They pick up the long-awaited link between online as well as offline trade and also for that reason have high expect brand-new modern technologies. With the supposed Near Field Communication (NFC), sellers are already trying different options in this area. Nevertheless, the goal of consumer localization in department stores is not sufficiently attained by current modern technology (RFID, WLAN, infrared). With the supposed sign technology, the essential technological criterion is currently to be produced.
Beacons use a slimmed-down variation of the Bluetooth requirement, which makes use of less energy for information transmission as well as is consequently also ideal for daily objects. This future market has not stayed hidden from Apple: recently, iBeacon was launched as its very own solution. The inquiry for customers is which data these signs really process as well as whether the innovation develops brand-new surveillance software program. The following short article provides a technological overview and also take care of the lawful aspects of information protection.
Data protection risk?
In information security regulation, a distinction has to be made in between the beacon as the sender as well as the receiver program.
1. Beacon operator
Allow us first concentrate on the operator of the sign. The sign modern technology option itself only sends out the identification numbers currently mentioned, which can be processed by the getting gadgets in a closer distance. Because the signs are sent out by individual objects, there is normally no personal recommendation within the definition of Area 3 (1) of the Federal Information Security Act (BDSG). The sign itself can not recognize which tool receives identification numbers due to the fact that the information circulation is only prejudiced. A personal referral would only be possible if a things on which the sign is set up is appointed to a certain person. Similar to a smartphone ID, a personal recommendation could be offered below if more info (name, e-mail, Facebook profile, etc.) is linked to this day. In his post on iBeacons in the publication PING, von der Heide describes the example of the iBeacon secret fob, which makes it possible for the owner to establish the place of his keychain using the application. There would certainly be a significance to information defense law if added individual info were included in the crucial fob.
Verdict: Given that the beacons act as pure transmitters, there is no information protection-relevant handling of individual data. As a rule, the beacon itself additionally has no individual reference, given that it is not private information concerning a particular or recognizable individual. The only exemptions are a fixed link in between the item with the set up sign and one person.
2. Receiver program
As opposed to the sign, the receiver program (generally a smart device application) processes as well as assesses information. Because the app is frequently connected to a user account, personal data is stored and processed. For instance, the program obtains the info that the individual remained in the branch of an outlet store chain at a particular time. Since the precise position within the branch can also be determined by the beacon innovation, there are fascinating advertising chances. So a customer can have checked out a certain item. Through tracking with a beacon, the store owner obtains the details that the purchase has not been finished (beacon at the checkout was not set off). In order to still obtain his items marketed, the info in the application could be utilized for retargeting on the Internet. Preferably, the individual is then directed to the online store and moved to complete the acquisition. Sign modern technology therefore prolongs retargeting with an offline network.
Due to the direct personal recommendation (app-- customer account-- place-- sign), handling according to German law would certainly in principle just be feasible with the consent of the data subject. If the user knows the data processing processes when installing an application, a legal justification might offer (processing to meet the agreement). This would certainly need to be checked individually based on the concrete application.
In any case, the individual has to be sufficiently notified. According to the Telemedia Act (TMG), customers should be effectively informed before the processing procedures within a data security affirmation. The proprietors of the app would as a result have to make clear the functions for which they are utilizing the area information of the individuals. Advertising and marketing actions would likewise need to be named. A review by the Bavarian State Workplace for Information Protection Guidance in 2015 reveals that the responsibility to provide detailed details within an information defense declaration is neglected in many cases. Nevertheless, business owners need to not put any space below, yet ought to develop depend on with their users through the essential transparency. You can discover details on developing such a data protection declaration here.
What should do to make certain beacon information security?

It ends up being specifically important if the liberty of the customer to choose concerning the data concerning him is weakened. This would be possible if the Bluetooth low power technology made use of by the beacons is triggered on the user device and also an app is then set up, which covertly sends details to the beacon operator's server at the request of beacons through this channel. Such misuse of trust would certainly already be sanctioned under applicable information security regulation, given that the user has not provided notified approval. In such lawfully clear instances, the customer is also required to avoid it. He should only get applications from reliable sources, given that there he can rather anticipate that having fun with open cards.
Do you see prospective advancement chances for beacon modern technology solutions and also its application that could jeopardize information security?
Up until now, smartphone customers have a great deal in their hands. Because you do not have to mount applications that react to iBeacons and also possibly reveal undesirable personal information. However, this self-reliance could be jeopardized if the sign technology is additionally executed on the apple iphone or smartphone itself, i.e. if the individual himself releases the signals that may a. can lead to a very exact indoor location of his individual. Then he will certainly have to be much better educated about what the technology as well as uses intend to expose. Right here the suppliers will be needed to interact plainly in order to construct trust with consumers or potential customers.
Final thought: Beacon innovation gives apps new opportunities for data processing. Along with the inquiry of lawful admissibility (consent or legal basis), the info obligations in particular come to be intriguing for the operator. Here operators need to describe all pertinent handling processes with personal reference in order to create the necessary transparency for customers.
 torr45838
torr45838
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.