Earlier this year the new standard of secure passwordless authentication was submitted to W3C. Major browser are already in the process of implementing this standard so we can expect that this kind of authentication will be available to the end users very soon. Meanwhile I was playing with the ESP32 development board which features Bluetooth Low Energy connectivity. I think it will be extremely interesting to build personal authenticator device.
URU Key
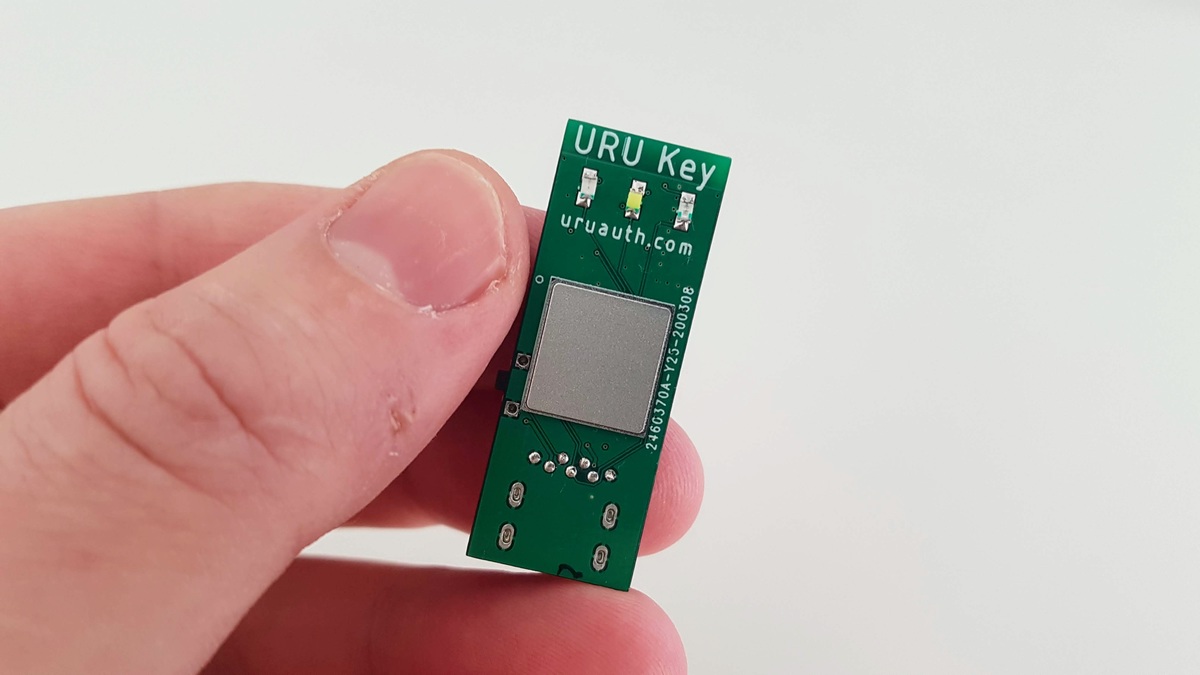
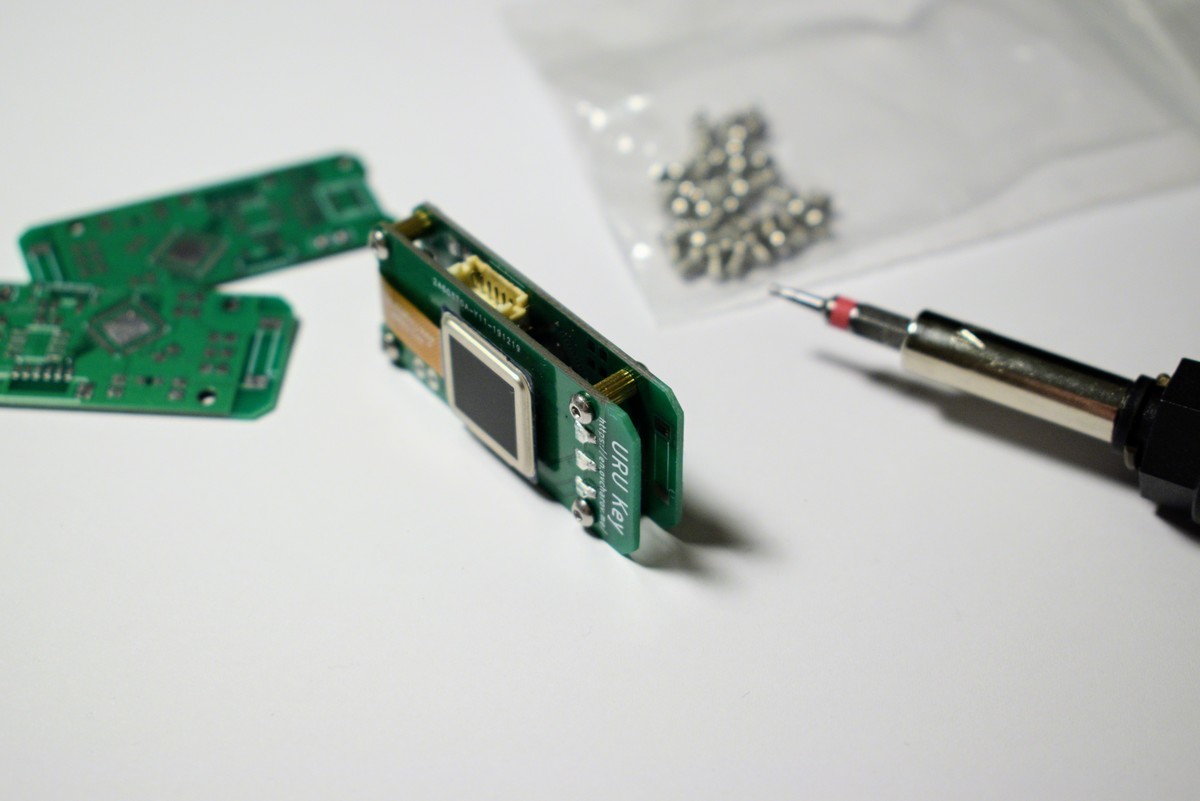
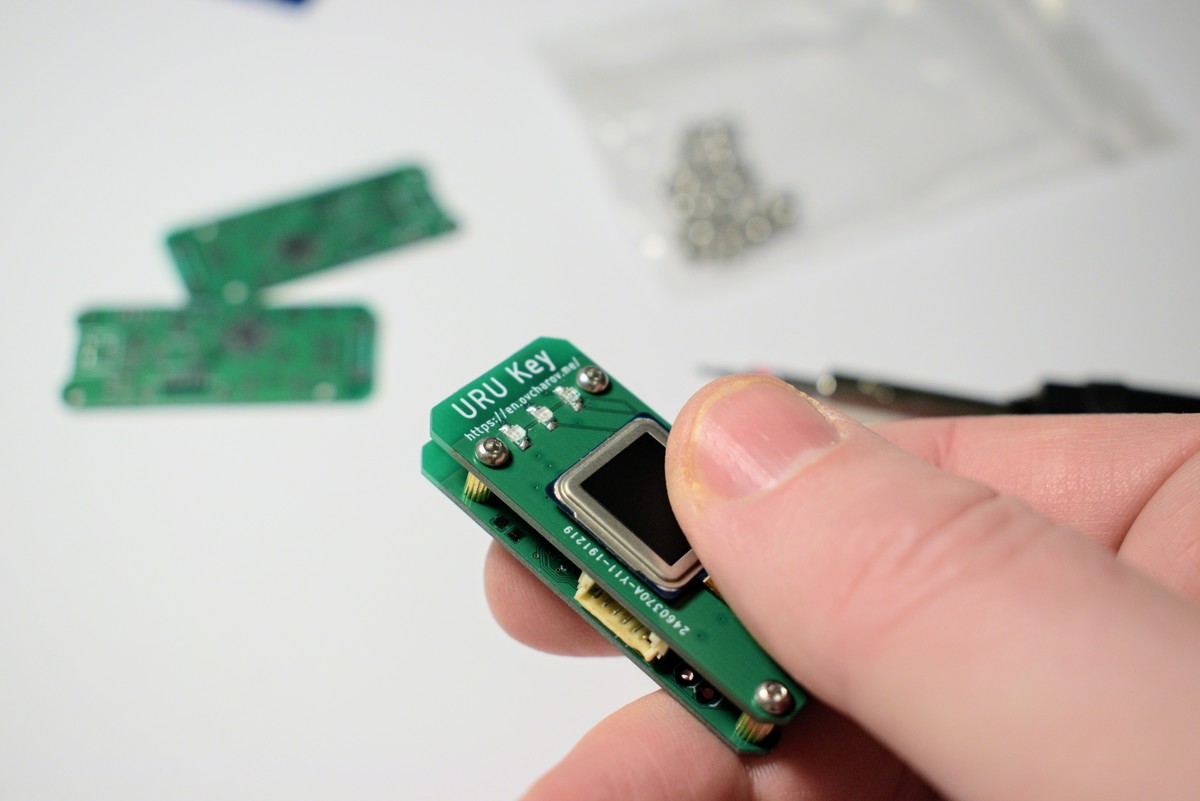
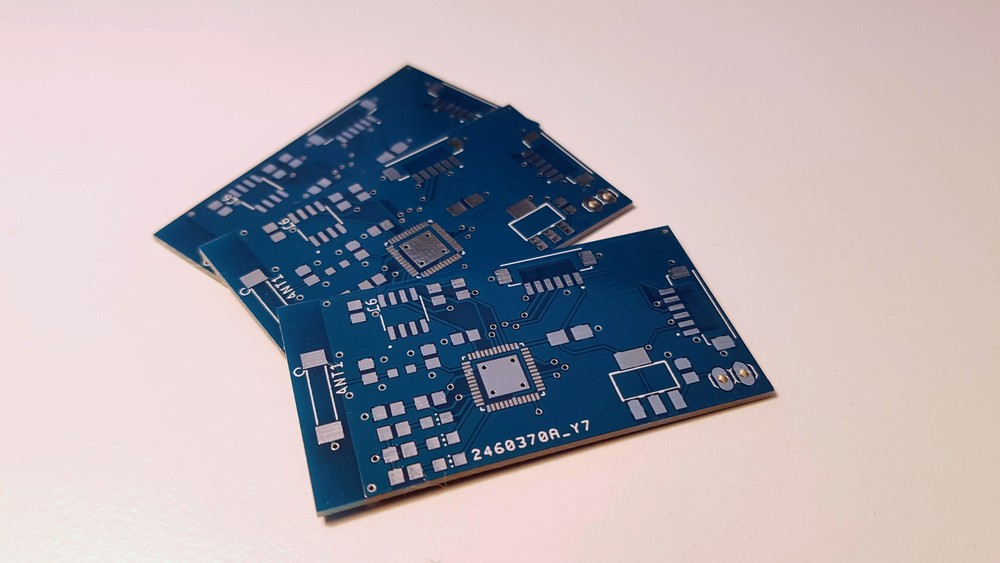
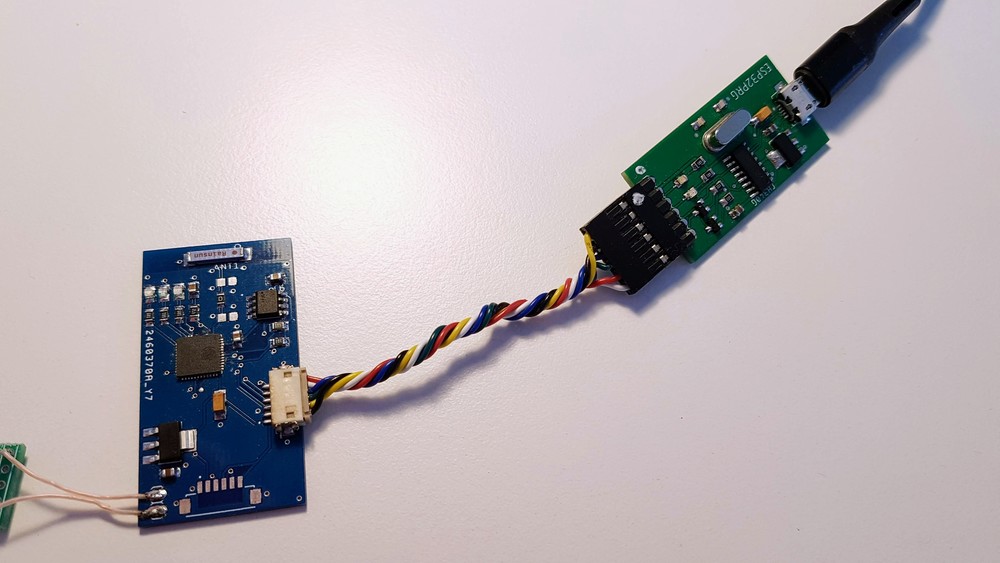
URU Key - a biometric FIDO2 Authenticator
built with ESP32 / ATECC508A / FPC1020
 Andrey Ovcharov
Andrey Ovcharov





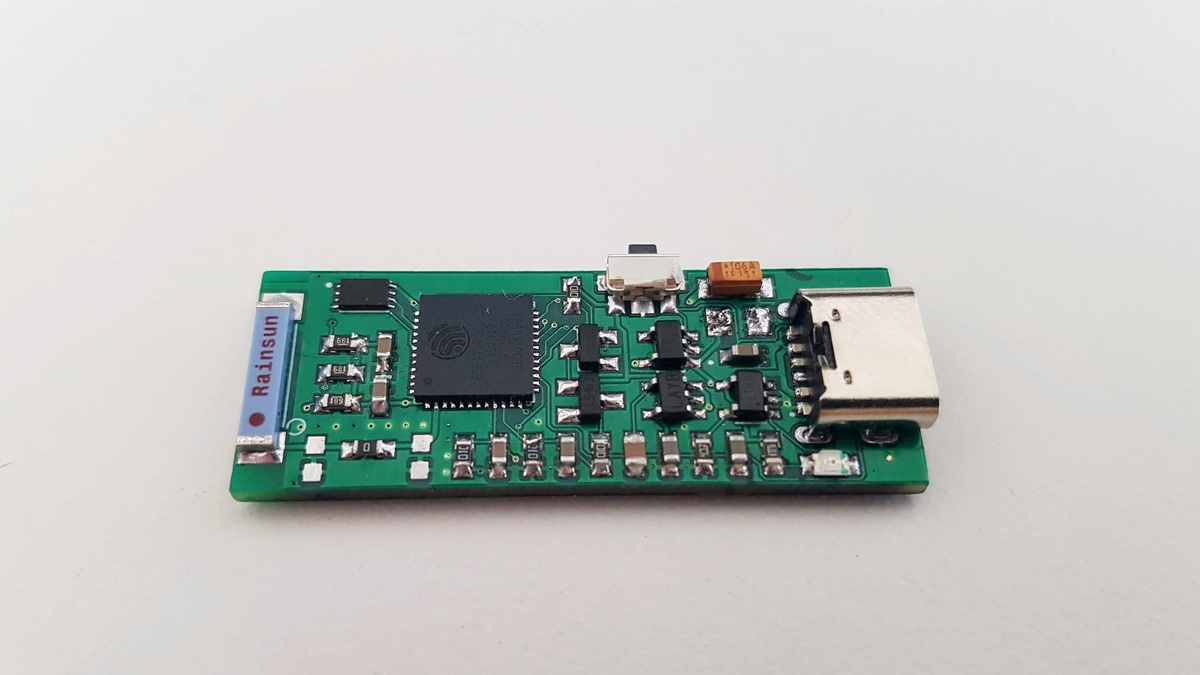

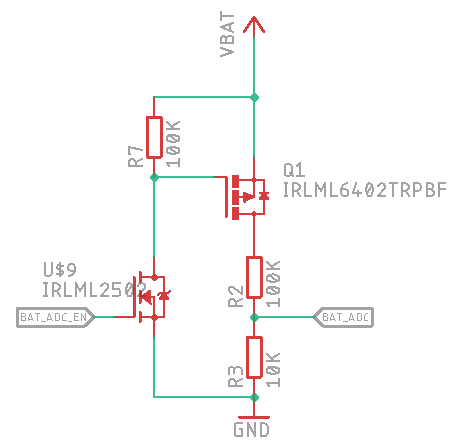
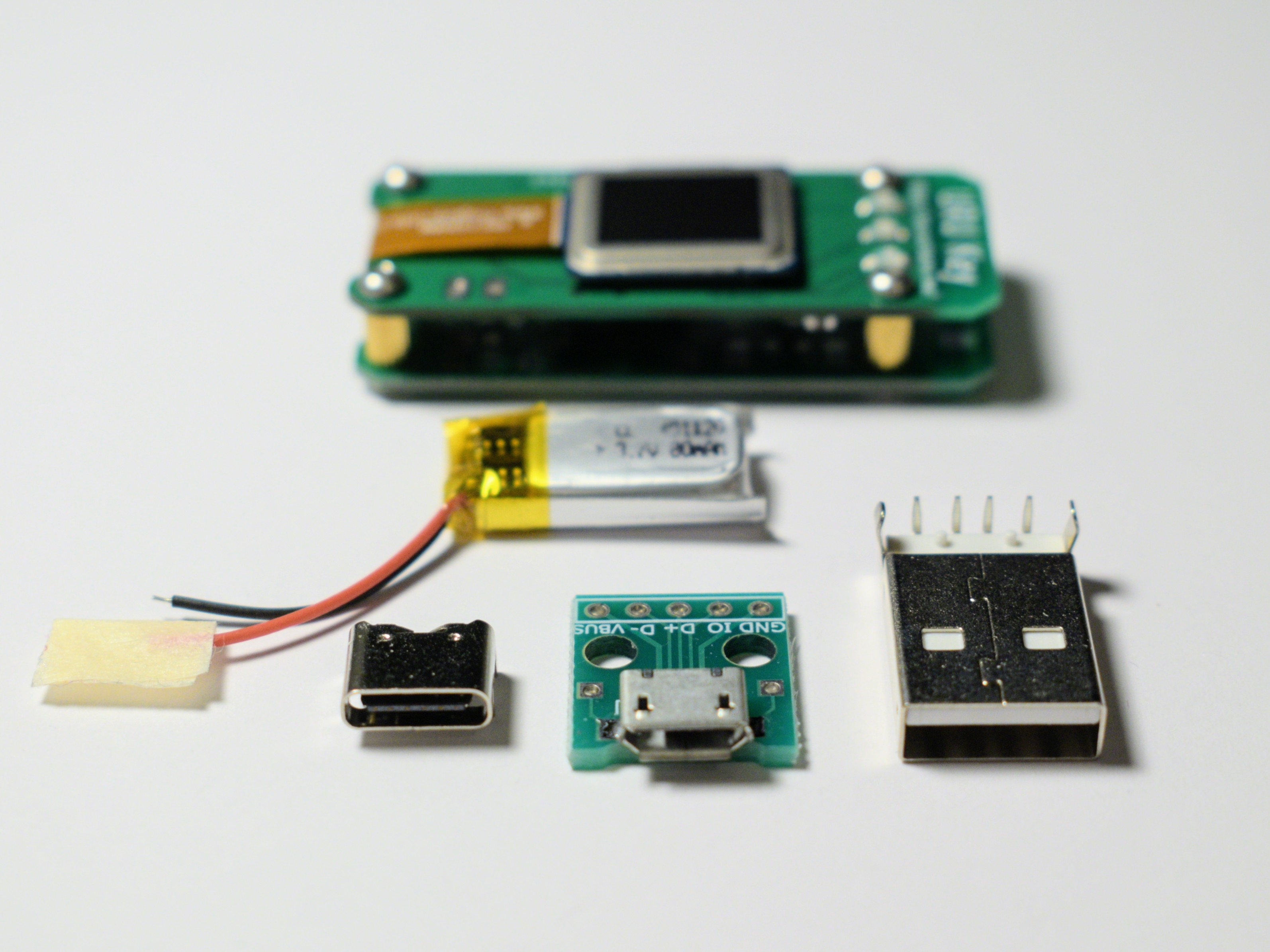

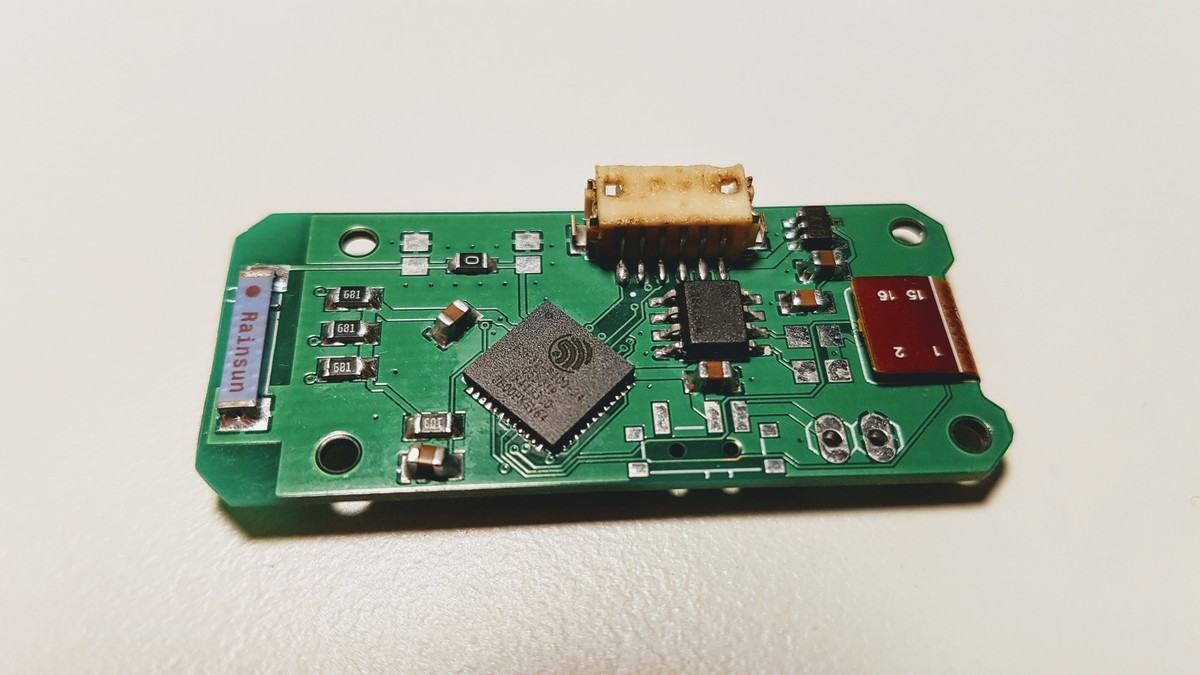
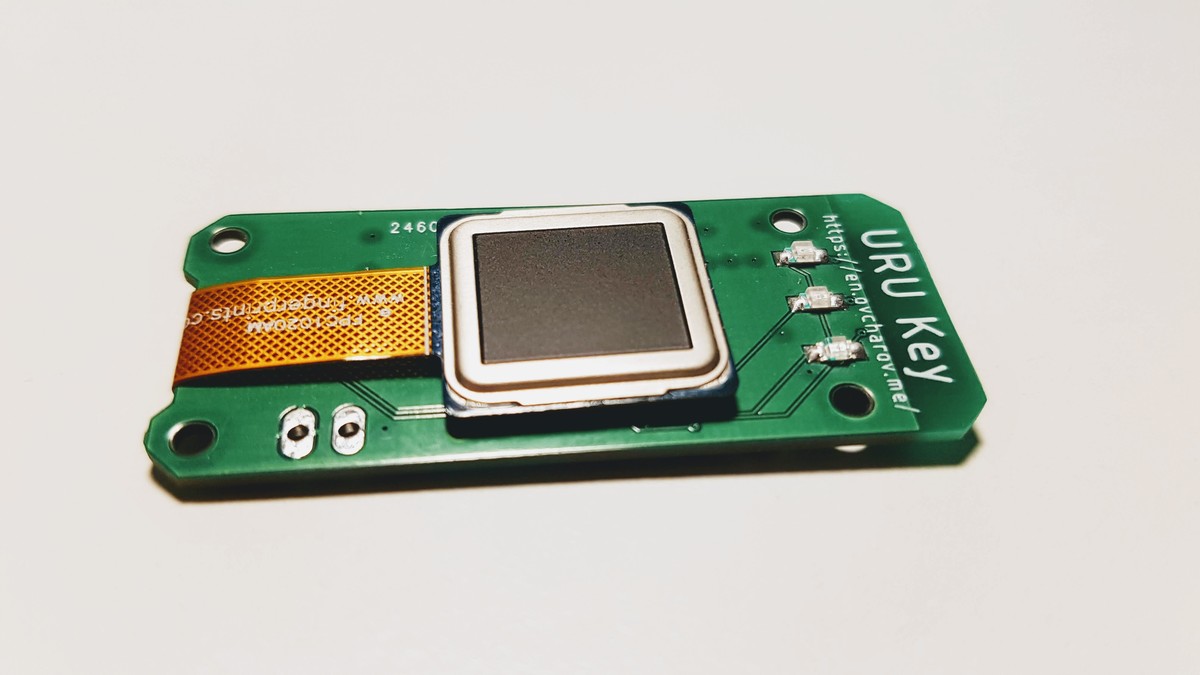
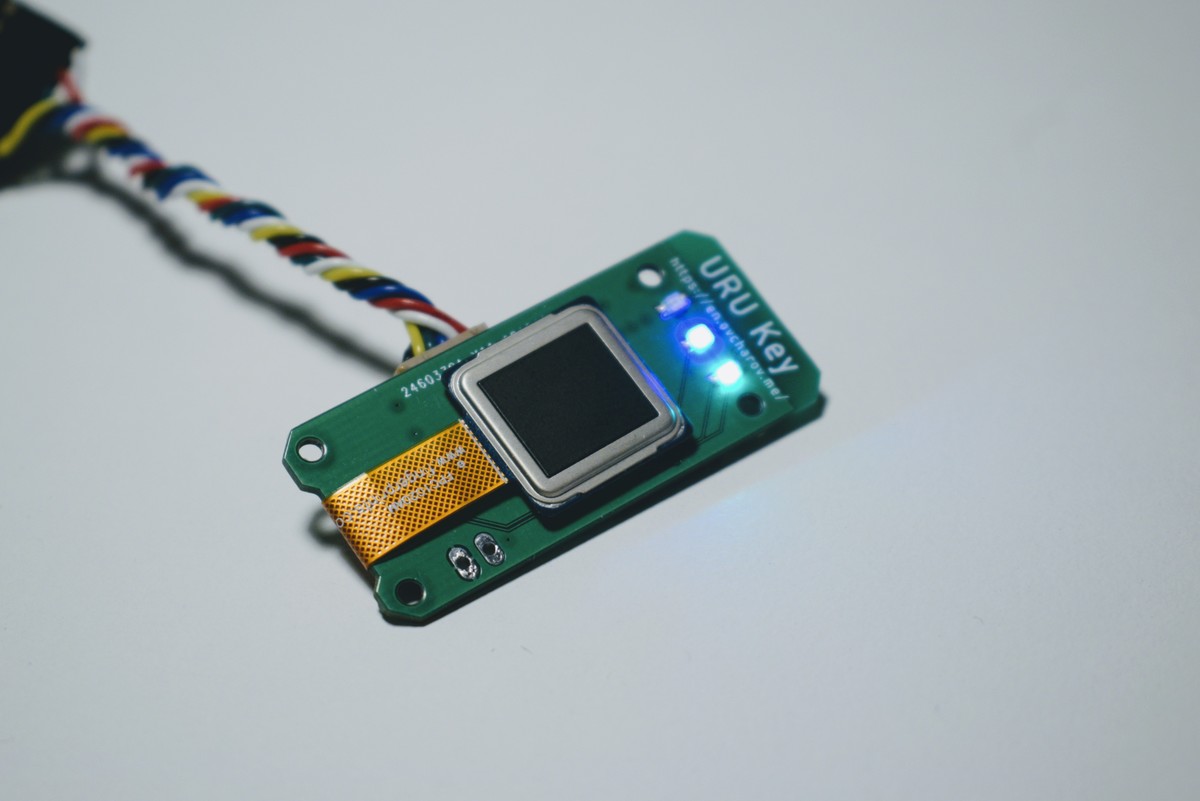

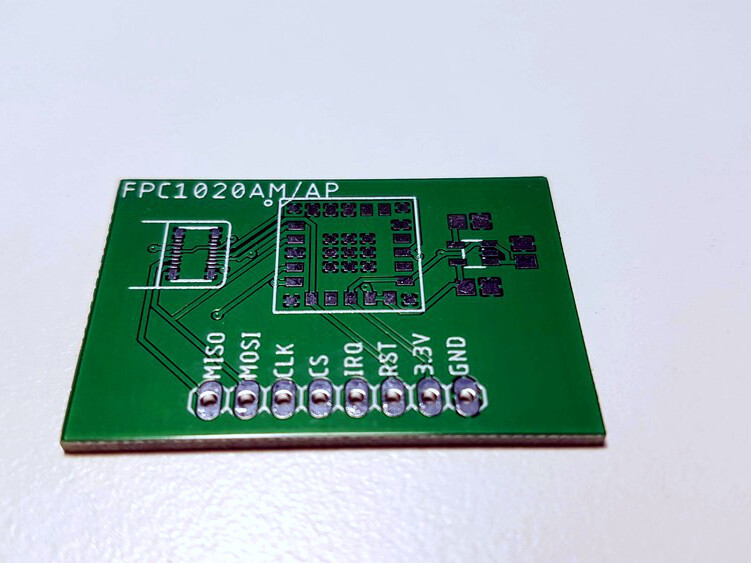
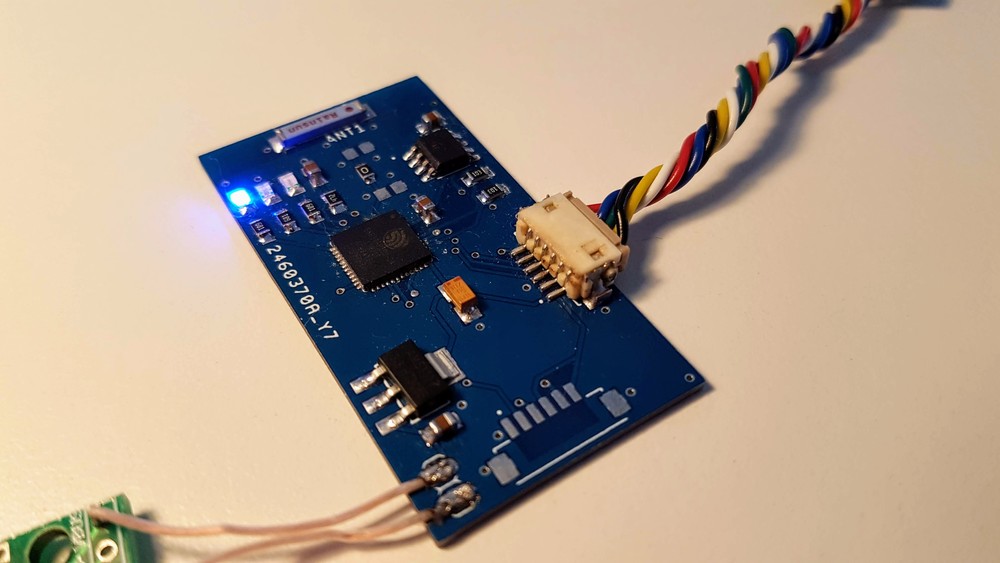
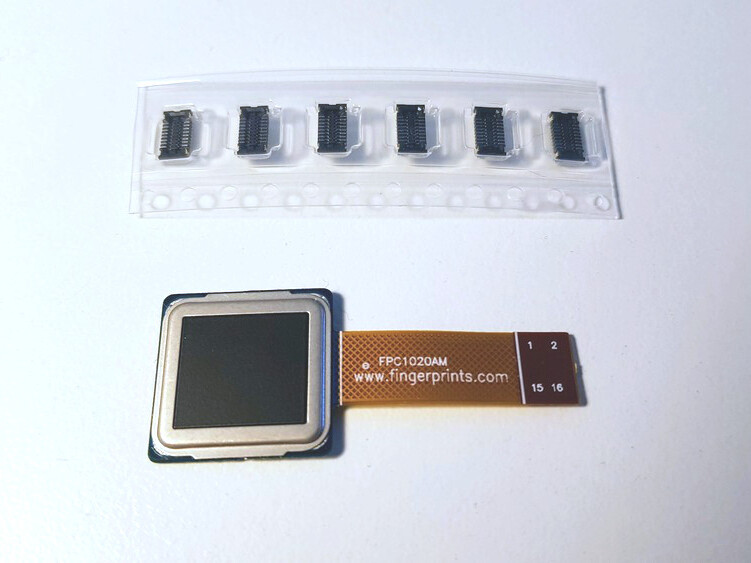 FPC1020AP is the same scanner in LGA package and I’ve spent some time figuring out how to properly connect it.
FPC1020AP is the same scanner in LGA package and I’ve spent some time figuring out how to properly connect it.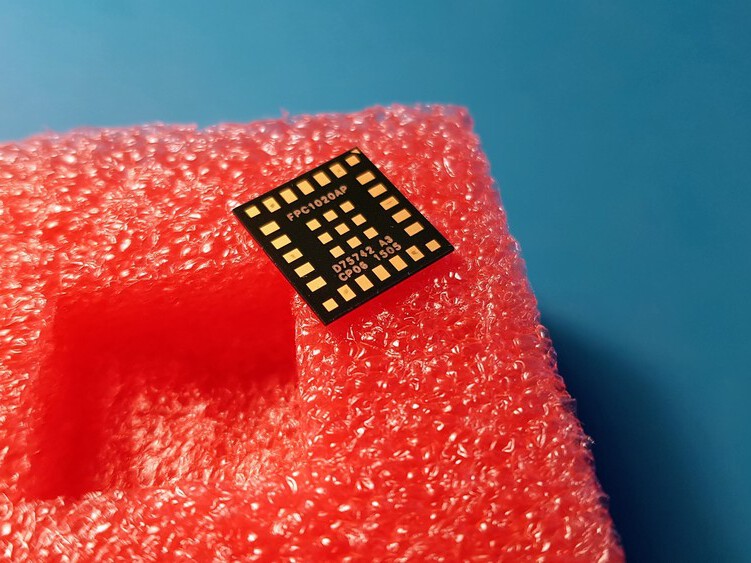
 The board is connected to the ESP32 development board with four wire SPI interface.
The board is connected to the ESP32 development board with four wire SPI interface.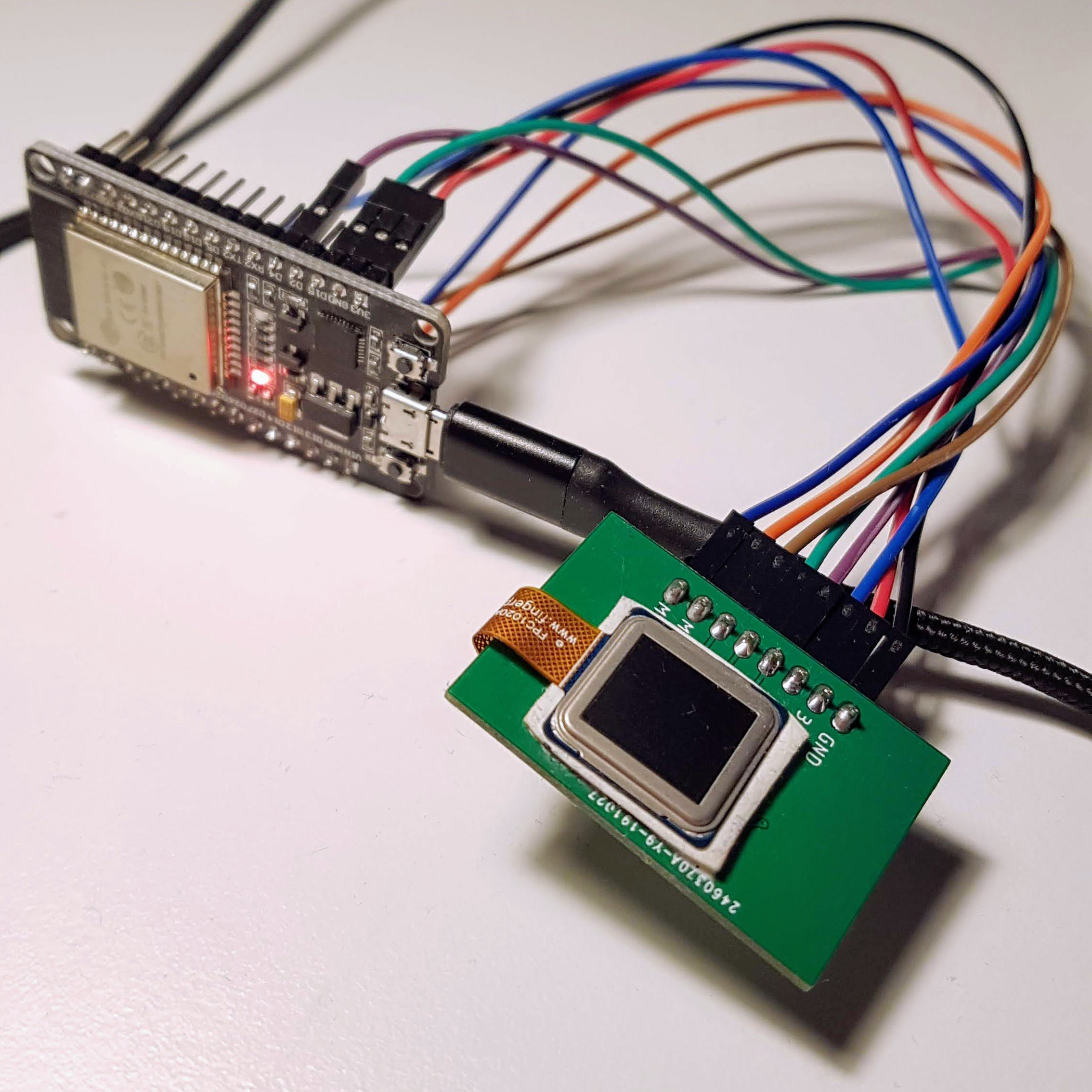






 mulcmu
mulcmu
 Matias N.
Matias N.

 Ben Lim
Ben Lim
You said you won't opensource it due to biometrics.
But perhaps you can make a "URU Key Lite" without fingerprinting, but with a simple click-button (and maybe tiny screen in the freed from fingerprinting space), and perhaps a pair of USB + USB-C connectors for desktop uses ?