The first rule is: don't use any app that comes with your IP cam. Always make sure that you know where your images are going.
But even if you control how you transmit the picture to your observation device of choice. (mine is a self-hosted Dyn-dns and direct access via user and password through the app "IP cam Viewer") There is always the possibility that deep down in your camera's firmware, a pathway to china is coded. Because I don't trust my abilities to check for such hidden "features", my cams get turned off "hard" when somebody is at home. The power for each of the cameras is turned off via my Smarthome either through remote-controlled plugs (433Mhz - which again creates its own risks) or direct via a digital output and a relay.
To overcome all these security flaws, I created a method to check if the cams are "ON" when they should be and, much more important "NOT-ON" when nobody should watch. This checking mechanism is done in my Node-red and my Soft-PLC.
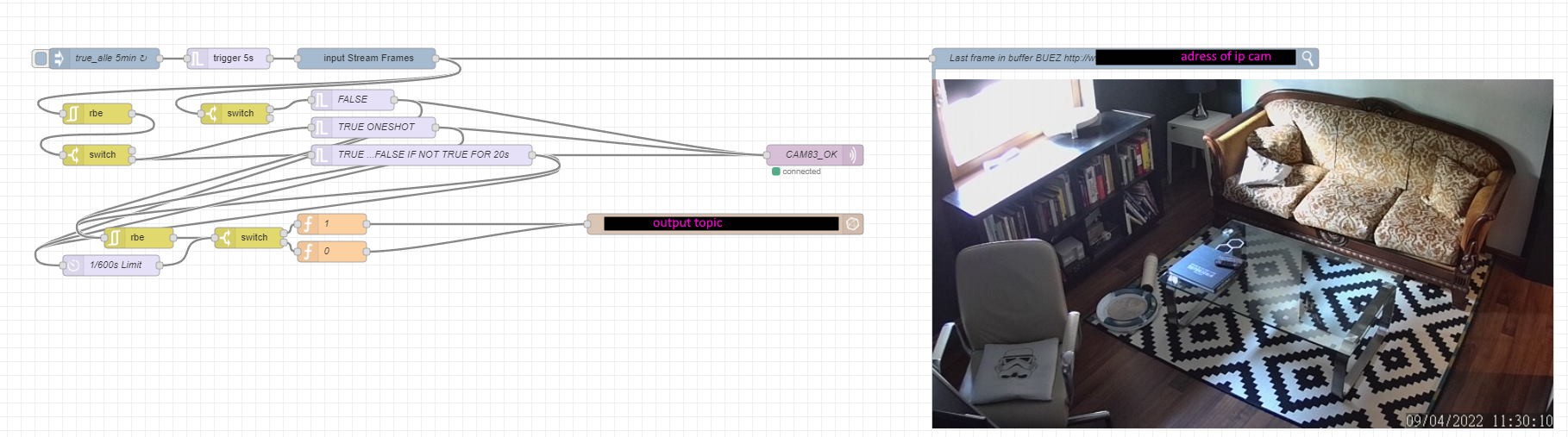
The Nodered constantly (in certain intervals) checks if it is able to get a picture from the cam. If not, it sends an "OFF" state to my Soft-PLS and vice versa. The PLC always compares the desired state to the current state from the Node-red.
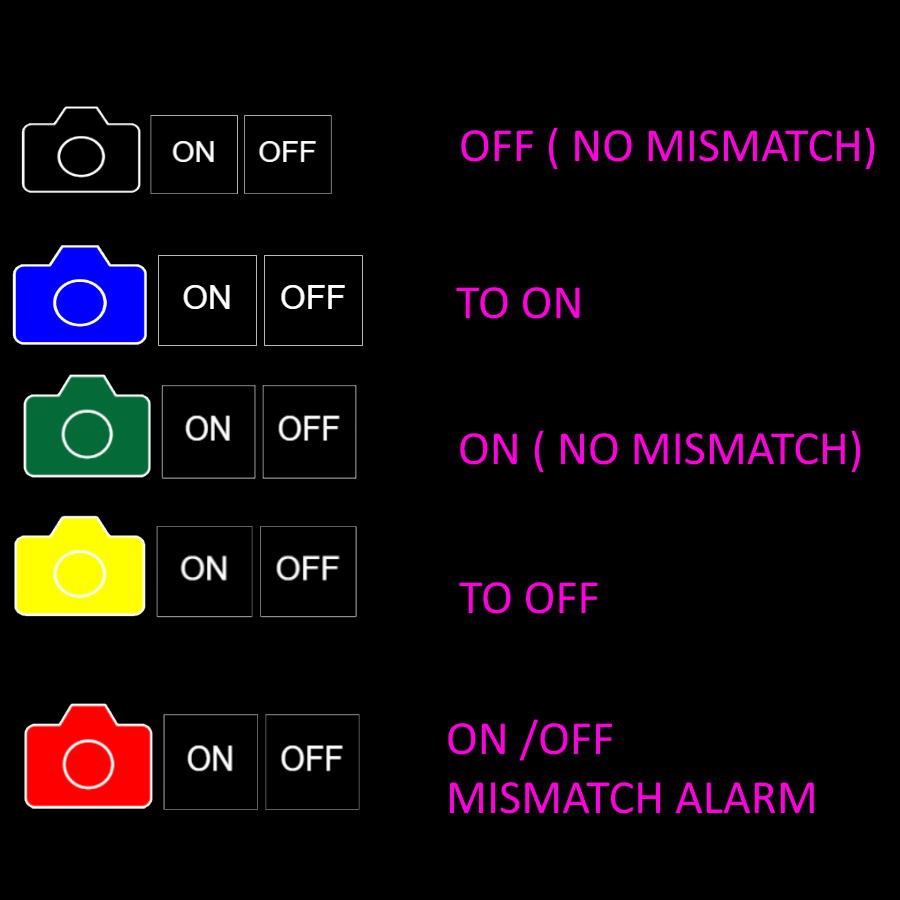
If there is a mismatch, an alarm is sent to my phone (via Phusover), and the symbol on the UI gets red.
This method is not flawless, and I am sure I missed some possible entry points for motivated hackers.
 stefan.schnitzer
stefan.schnitzer
 NaranInc
NaranInc
 Ansaf Ahmad
Ansaf Ahmad
 Dewet
Dewet
 Robot
Robot