As I said in the previous log, I decided to take a break from schematics drawing and to look at the software; I chose to start with the ROM from the Rotor 2 board, since I was reasonably sure that it contained card reader interfacing code and since the board is less integrated and easier to probe if need be. I'm not sure if I can post these here; after all, it's still copyrighted code (but then again, with almost no payphones remaining at all, who would care? )
The first problem I encountered is that the Hitachi HD6305Y2 is not a popular MCU, so there's very little information about it. I managed to find the original Hitachi handbook (http://bitsavers.trailing-edge.com/components/hitachi/_dataBooks/1988_U08_HD6305_Series_Handbook.pdf), but no disassembler or compiler.
This didn't leave much options: if I wanted a disassembler, I had to write one myself. Luckily, the popular reverse engineering tool Ghidra does offer the possibility to add a new architecture. The process is not all that well documented, but luckily I found a Reddit post which explained it pretty well (see https://www.reddit.com/r/ghidra/comments/ba09tk/documentation_on_adding_new_processor/ ). I copied some stuff from the files for the already supported processors and, with the help of the provided SLEIGH documentation (https://ghidra.re/courses/languages/html/sleigh.html) I was able to write my own processor module (you can find it here: https://mega.nz/file/CDQD3SwT#_zkjB--d8NPhUFaqIKVJzupw02vo9lRbekrEkIG6EP4 but there's no guarantee it's error-free).
So, I imported the ROM files into Ghidra, aaand:
Yeah, it's full of errors. I tested the disassembler on a fake ROM i made that contains all the instructions the processor supports in sequence and it recognizes and decodes them correctly, so I strongly suspect this is just due to me not starting the disassembly at the right place in memory (I just dumped the whole ROM from start to end). I need to check the address decode logic on the CPU board to really understand what addresses contain code and what don't.
Just for fun, I imported the Z80 ROM:
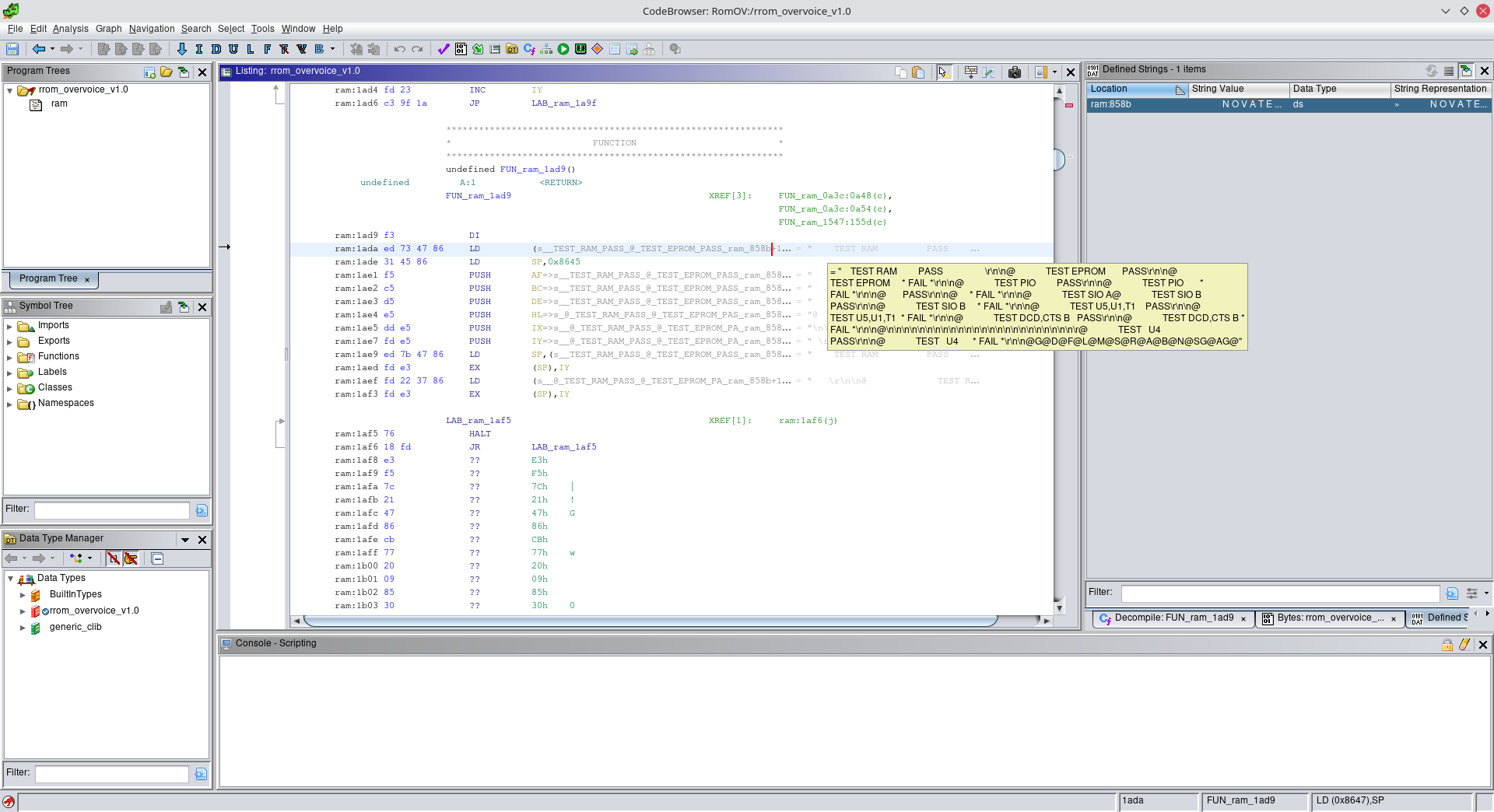
This already looks better, AND it looks like they're using one of the MCU serial ports as a debug port, as seen in the highlighted strings.
The next step will probably be tracing the CPU board to get the memory map of the processor, so that I can atleast confirm I'm trying to disassemble code and not random data.
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.