We have a holiday house with a complete off-the-grid solar charging system, which consists of 6 solar panels and a 24V / 525Ah battery bank. The Outback MX solar charger we use has a special port that you can connect an Outback MATE to, which itself has an RS232 port for logging data.
However this logging data is a pretty basic ASCII packet, and I was frustrated that I couldn't access the more advanced information shown on the LCD! So I started this project in an attempt to access the raw data myself.
The result is pyMATE - an open-source python library that can speak the native protocol that Outback devices use, and it opens up many more possibilities than the RS232 port alone could provide.
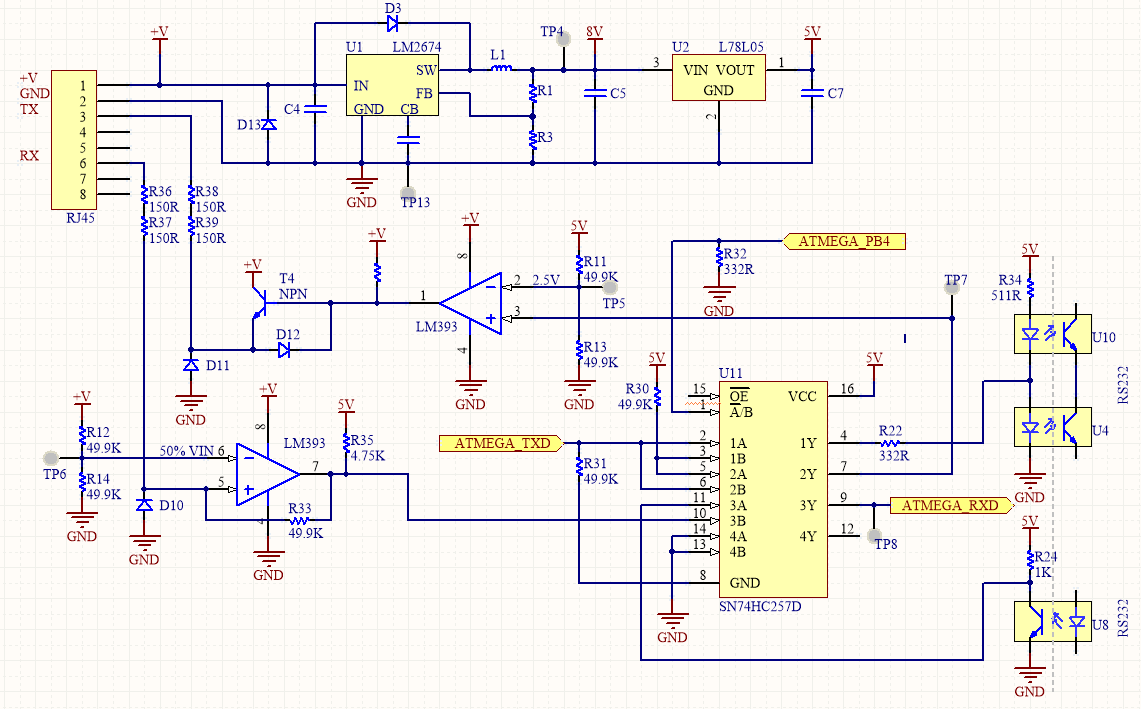
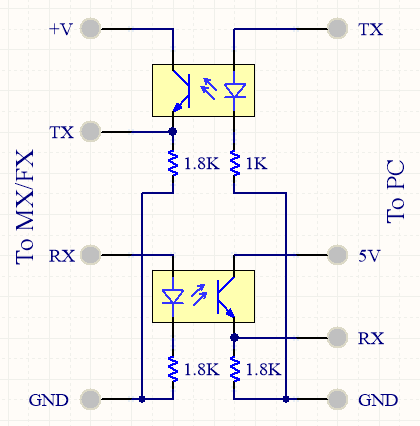
All it needs is a UART port and some opto-isolator hardware to convert it to the correct voltages.
Currently I am able to:
- Get a status packets for the MX solar charger, FX inverter, and FLEXnet DC monitor
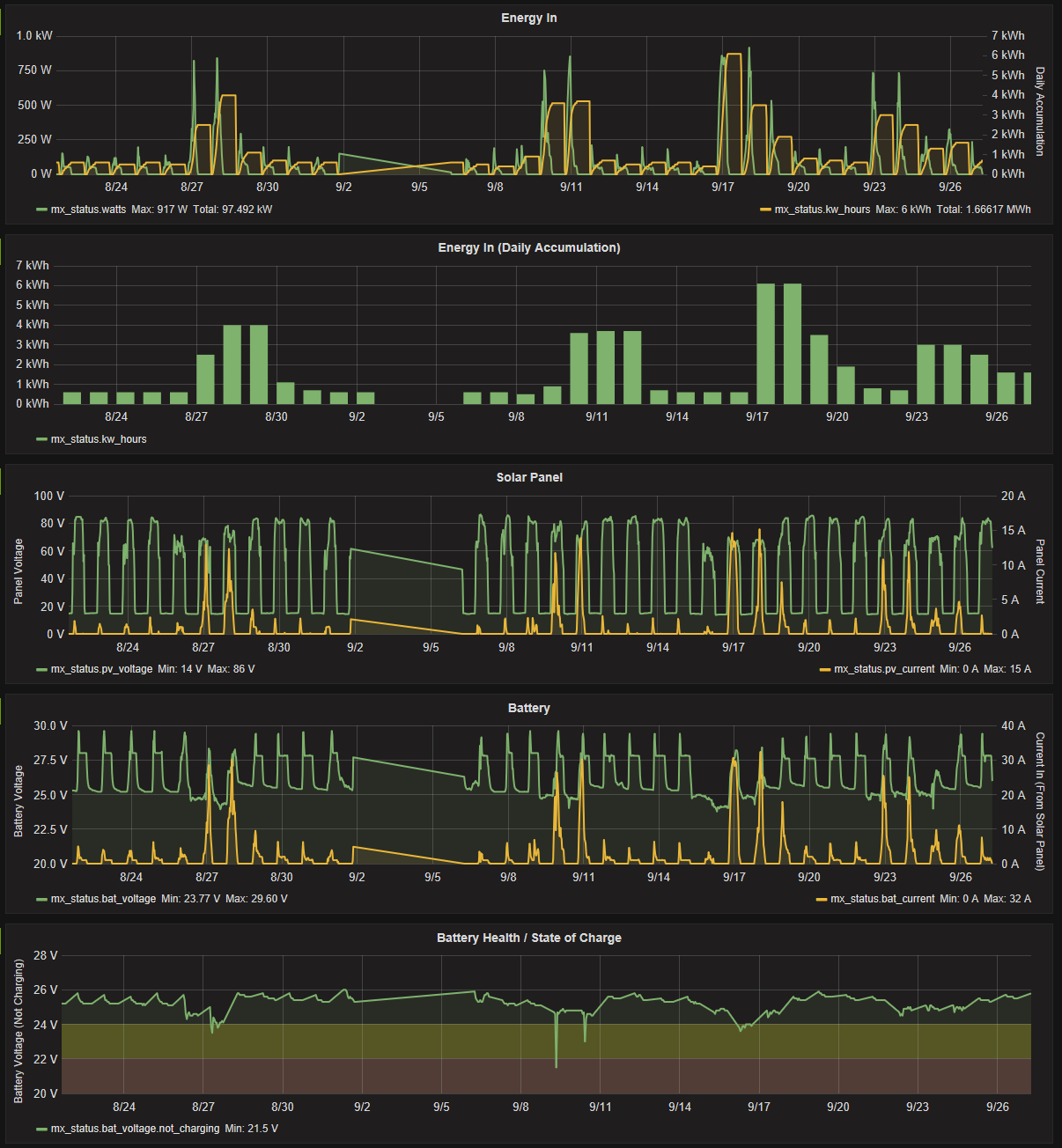
- Get log entries stored on the MX (Up to 255 days worth)
- Read & write MX/FX/DC registers, parameters, and controls (allows you to change system behaviour!)
Full protocol implementation details is available in the python library.
Leave a comment if you found this library useful!
 Jared Sanson
Jared Sanson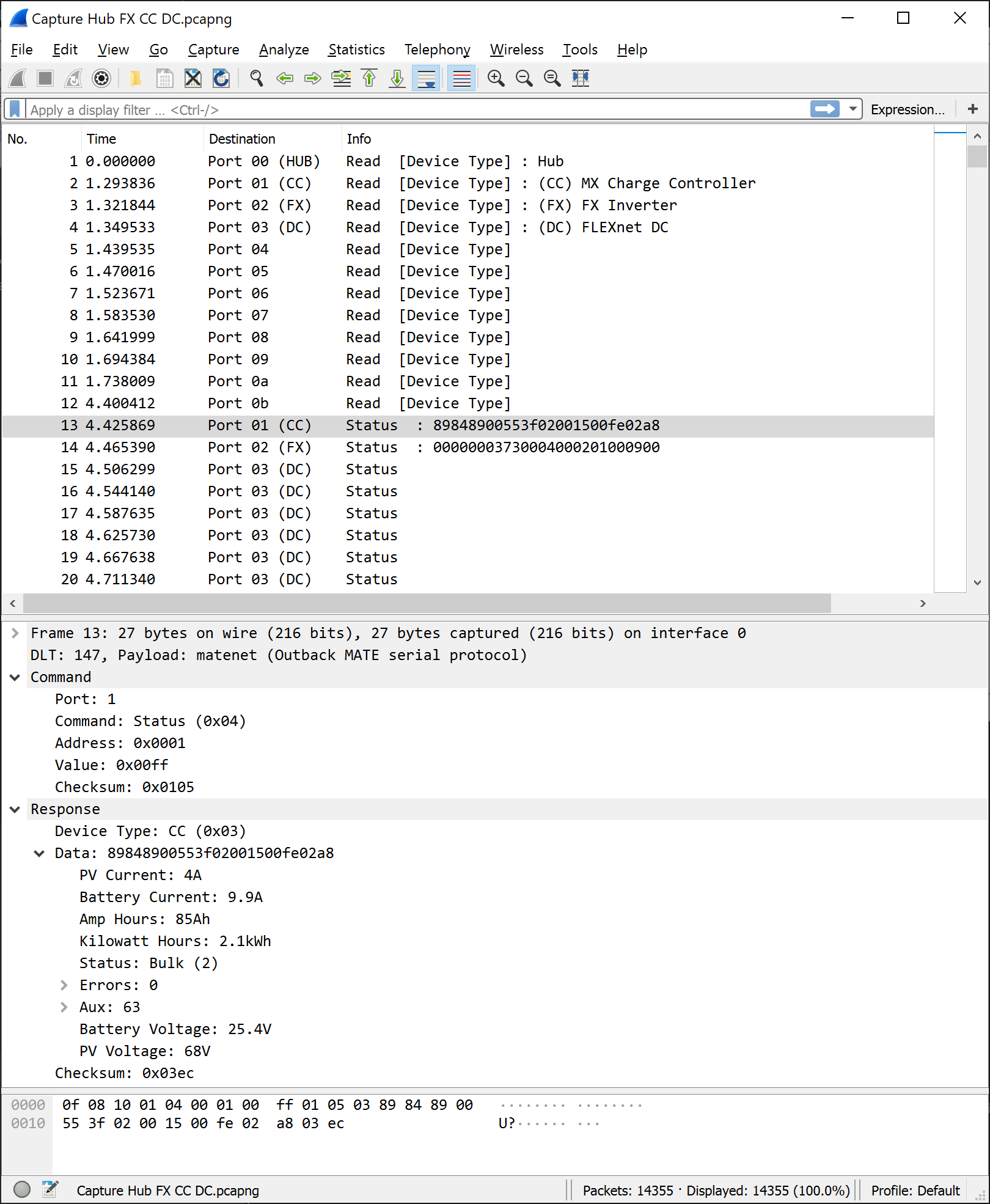 This has been immensely helpful for figuring out the remaining details, as I can capture & monitor traffic in real-time and compare it with the MATE readouts. It helped me discover that the MATE actually synchronizes the devices every minute or so by reading/writing specific registers - and this is how the FLEXnet DC can know the date, time, and battery temperature without actually having an RTC or temperature sensor.
This has been immensely helpful for figuring out the remaining details, as I can capture & monitor traffic in real-time and compare it with the MATE readouts. It helped me discover that the MATE actually synchronizes the devices every minute or so by reading/writing specific registers - and this is how the FLEXnet DC can know the date, time, and battery temperature without actually having an RTC or temperature sensor.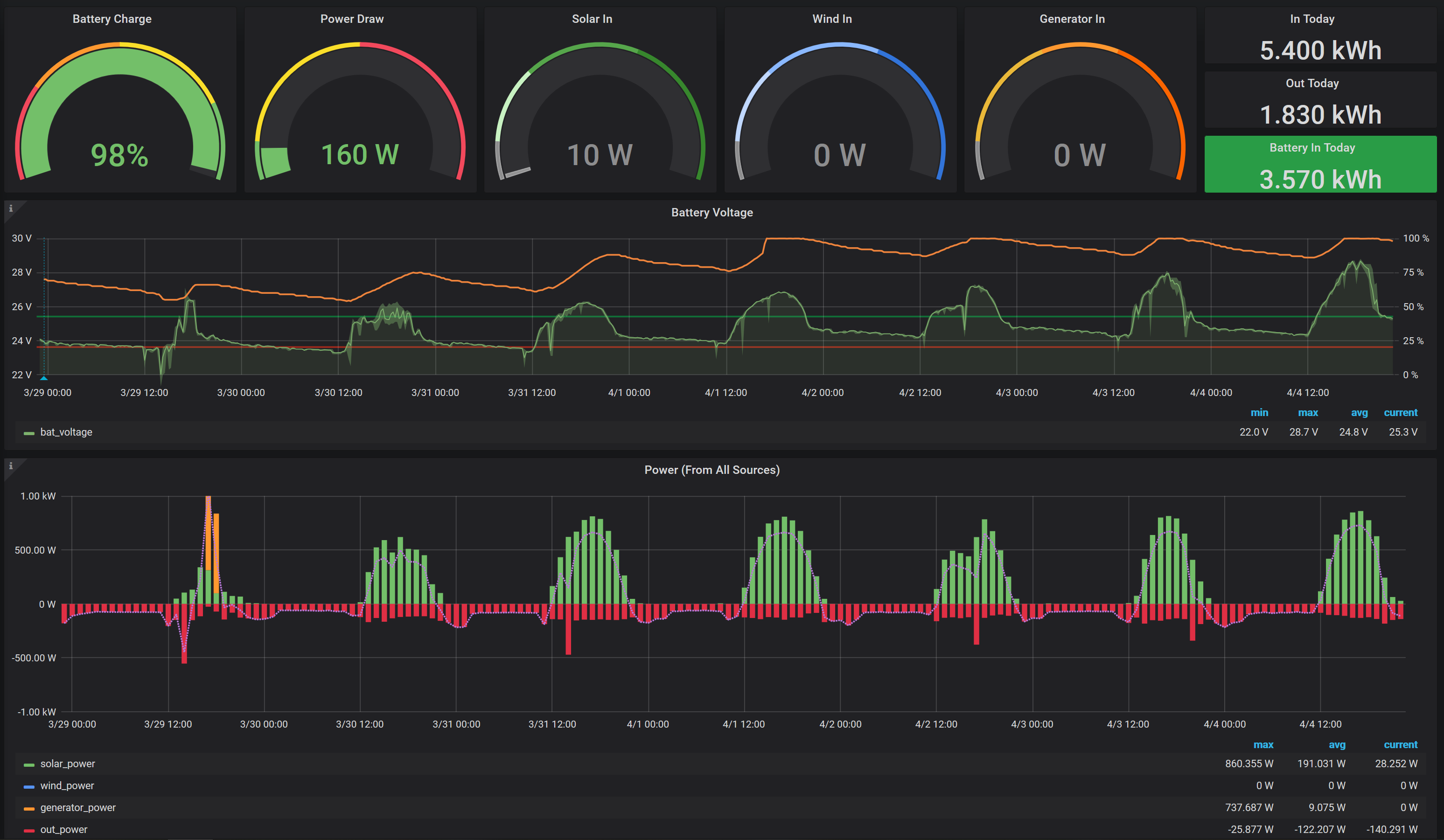 Repos:
Repos: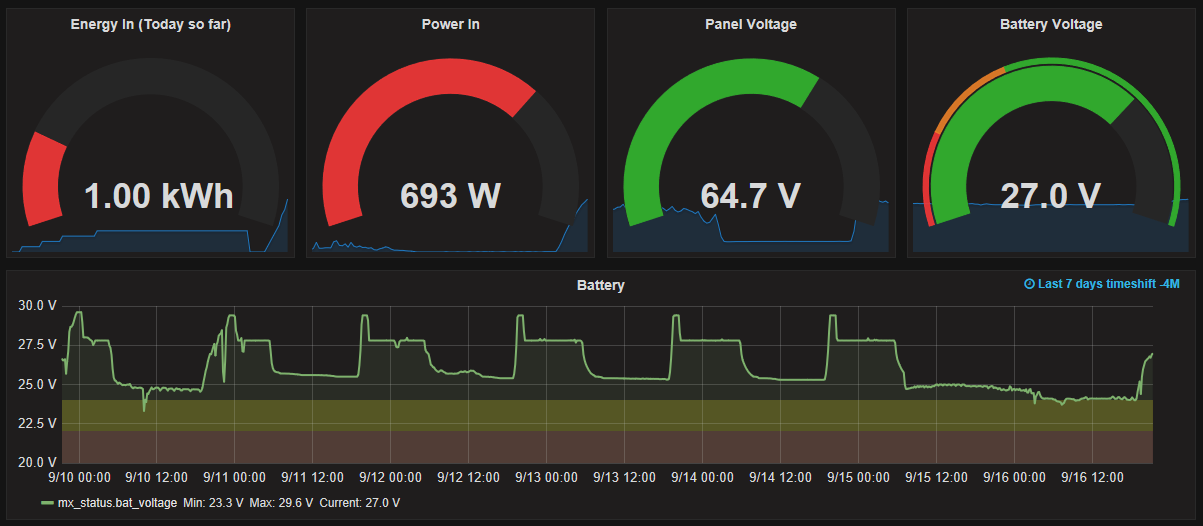









 Dominic DeMarco
Dominic DeMarco
 David
David
Thanks for posting all this wonderful work.
I have a 48V system and noticed the Vbat on the RJ45 connection of the FlexMax is about 22V. Does this make any sense?