Firmware
Original firmware
The original firmware runs on S132 SoftDevice ver 2.0.1.
The device contains an OTA bootloader that can be used with the generic Nordic upload tool, so new firmware can be uploaded safely.
Custom firmware
The chip is locked, so if you want to use your own firmware you have to use the built-in OTA bootloader or erase the whole chip to remove the lock.
Hardware
Hardware Components
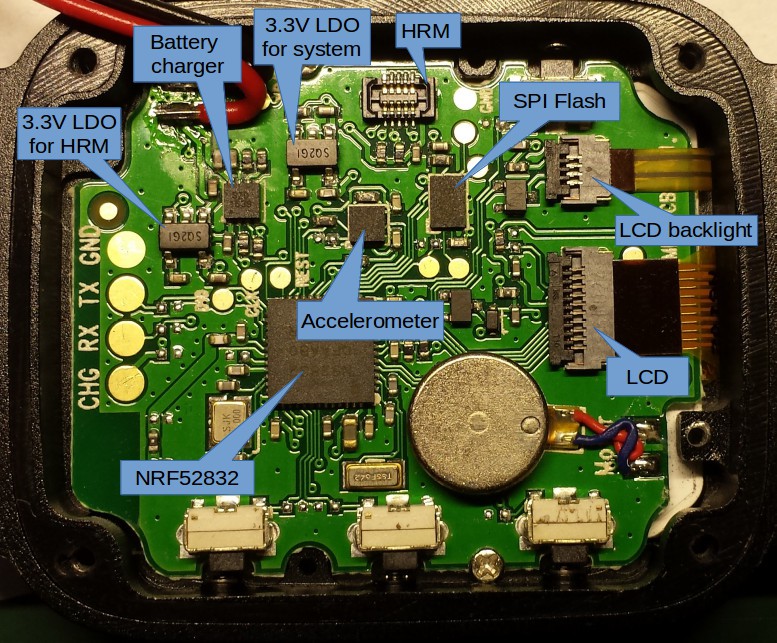
| NRF52832-QFAAB0 | Main SoC |
| LP2985 (?) | 3.3V LDO for everything |
| LP2985 (?) | 3.3V LDO for heart rate sensor module |
| RT9526 (?) | Battery charger |
| KX022-1020 | 3-Axis accelerometer |
| PAH8002 | Heart rate sensor |
| GD25Q16C | 16Mbit SPI flash |
| LPM013M126A | 176×176 Japan Display Color memory LCD |
Main MCU
Nordic Semiconductor NRF52832.
32-bit ARM Cortex-M4F CPU with 512kB flash and 64kB RAM and of course Bluetooth.
MCU pinout:
|
Pin |
Description |
|---|---|
|
P0.02 |
LCD SCLK |
|
P0.03 |
LCD SI |
|
P0.05 |
LCD SCS |
|
P0.06 |
LCD EXTCOMIN |
|
P0.07 |
LCD DISP |
|
|
|
|
P0.04 |
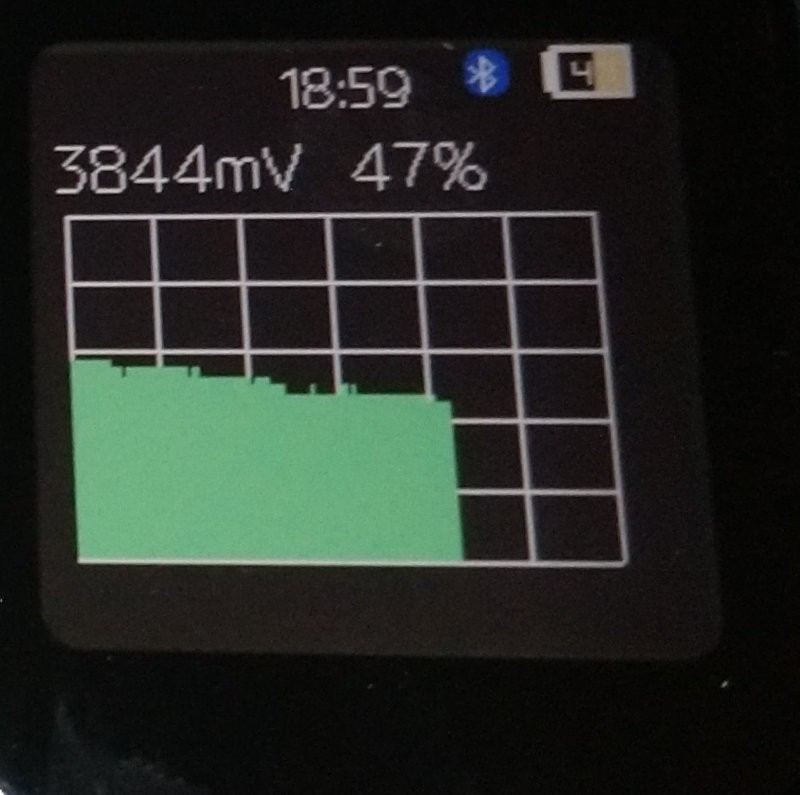
Battery voltage measurement (x0.25 divider) |
|
|
|
|
P0.08 |
BACKLIGHT ON |
|
|
|
|
P0.09 |
BUTTON BACK |
|
P0.27 |
BUTTON UP |
|
P0.28 |
BUTTON OK |
|
P0.29 |
BUTTON DOWN |
|
|
|
|
P0.11 |
FLASH MISO |
|
P0.12 |
FLASH CS |
|
P0.13 |
FLASH MOSI |
|
P0.14 |
FLASH CLK |
|
|
|
|
P0.25 |
UART RX |
|
P0.26 |
UART TX |
|
|
|
|
P0.30 |
VIBRATOR ON |
|
|
|
|
P0.15 |
ACCEL INT ? |
|
P0.16 |
ACCEL POWER |
|
P0.17 |
ACCEL SDA |
|
P0.18 |
ACCEL SCL |
|
|
|
|
P0.19 |
HRM SDA |
|
P0.20 |
HRM SCL |
|
P0.22 |
HRM INT ? |
|
P0.10 |
HRM RESET ? |
|
P0.31 |
HRM POWER ON |
| P0.23 | CHARGER STATUS ? |
| P0.24 | CHARGER POWER GOOD ? |
3.3V LDO for system
Unknown chip, but similar to LP2985. Powers the whole thing
3.3V LDO for heart rate sensor module
Same as above. Powers the PAH8002 heart rate sensor module.
Enable pin controlled by the MCU.
Battery charger
Unknown chip, seems like a generic linear li-ion battery charger IC.
Possibly a Richtek RT9526, the pinout seems to match.
Accelerometer
Kionix KX022-1020 3-axis accelerometer.
Communication over I2C. Powered from an MCU pin!
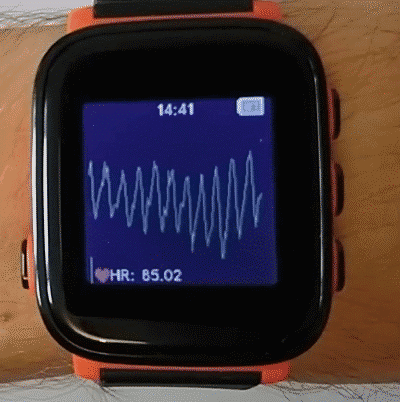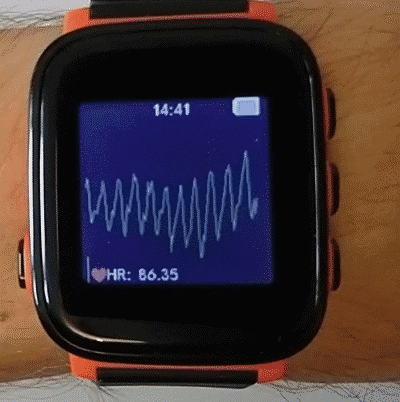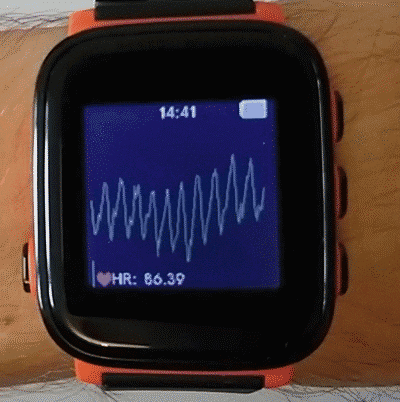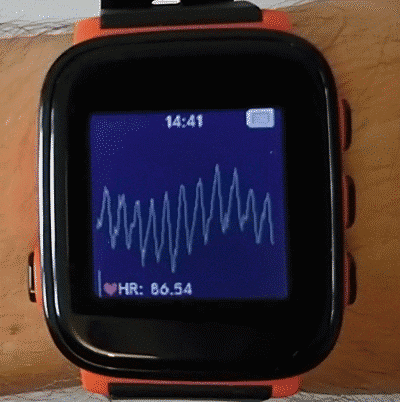
Heart rate sensor
PAH8002 heart rate sensor with green and infrared LEDs. Mounted on the back plate of the watch, connects to the mainboard with a ribbon cable.
Communicates over I2C.
I have managed to dig up the complete datasheet and application note.
External Flash
GigaDevices GD25Q16C 16Mbit (2MB) SPI Flash.
LCD
LPM013M126A 176×176 Japan Display Color memory LCD.
Driven with SPI. Has a LED backlight controlled...
Read more » emeryth
emeryth



















 Krzysiek
Krzysiek
 Kn/vD
Kn/vD

 Lukas Fässler
Lukas Fässler
Cant find this watch, is it still being produced?