DISCLAIMER: This article does not intend to facilitate phishing attacks or any other kind of illegal activities. The misuse of information contained in this article CAN bring criminal charges against you. The author will not be held responsible if criminal charges are brought against any persons utilizing any information related to this article, to break the law. DO NOT try to reproduce the scenario demonstrated in this article, with networks and devices you do not own, unless otherwise expressly permitted. The author has exclusively run this experiment on private premises and equipment.
This paradigm, inspired by academic interest on IT security, merely points out the risks to the confidentiality of data, submitted via WiFi access points that require their users to log in via a captive portal. It should act as a cause of concern both for the users, but mostly for the companies that have deployed such services and it's primarily their duty to protect their customers' privacy and security. If such an attack is commenced successfully, then the perpetrator can impersonate the legitimate user and perform malicious activities under the unsuspected victim's identity. Furthermore by disclosing the username and the password of this service, to a malicious individual, the credentials for others (e.g. online payment system, email etc) can be derived, especially if - as it is sadly a common practice - the same or similar are used.
The tutorial you will find below, is only about setting up a Physical Web Space, using an Open WRT device and specifically the Onion Omega. This attack, is a potential use case of the Physical Web Space, which could be as easily conducted, utilizing different technology. Additionally, the script that actually logs down the victim's credentials is not published, however it is practically very easy to compile.
To conclude, the combination of low cost, pocket sized equipment and software that does not require high technical knowledge to set up, can annotate this scenario as a valid threat that should be countered by appropriate security measures and increased user awareness. It is imperative that such risks are exposed publicly and coped with. Lack of security is not as dangerous as a false sense of security.
Despite not posting much in this blog lately, I have been particularly busy on various projects, mainly the SmartCar educational platform, more about which I promise to report on soon. One of them, was My Physical Web Space, that was published and featured on Instructables. The Physical Web Space, is a website that literally follows you around wherever you go, is hosted on a micro server that can fit in your pocket and the visitors can get access to it by using its WiFi hotspot. Moreover, the WiFi hotspot is enhanced by a captive portal, which redirects all requests to a specific (local) address.
A typical scenario of the Physical Web Space, begins the user detecting an open WiFi network on their smartphone, connecting to it (because we all love free Internet, don't we?), receiving a notification that sign in is required and then to be redirected to a local website hosted on the micro server. Additionally, all other (non https) requests are redirected to the local server.
The Physical Web Space original prototype, includes a Raspberry Pi Zero running lighttpd and just 3 AAA batteries as its power source which. Without any particular power consumption optimizations on the Zero, this setup provides enough juice for a couple of hours. Here, we will use it to demonstrate how easy it is to perform phishing attacks against users trying to connect to WiFi hotspots, that require some form of membership, paid or otherwise and a log in via a web page, in order to gain access to the Internet.
The rationale is fairly straight forward: The micro server will create a hotspot around it, with the same SSID as the network we want to target. At this point, it does not matter if the legitimate network actually exists in the area, but...
Read more » platis.solutions
platis.solutions
 Amine Mehdi Mansouri
Amine Mehdi Mansouri
 Guy Dupont
Guy Dupont
 Thomas
Thomas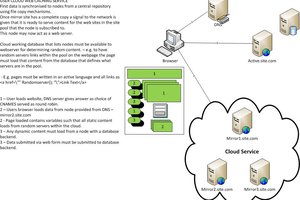
 Danny
Danny