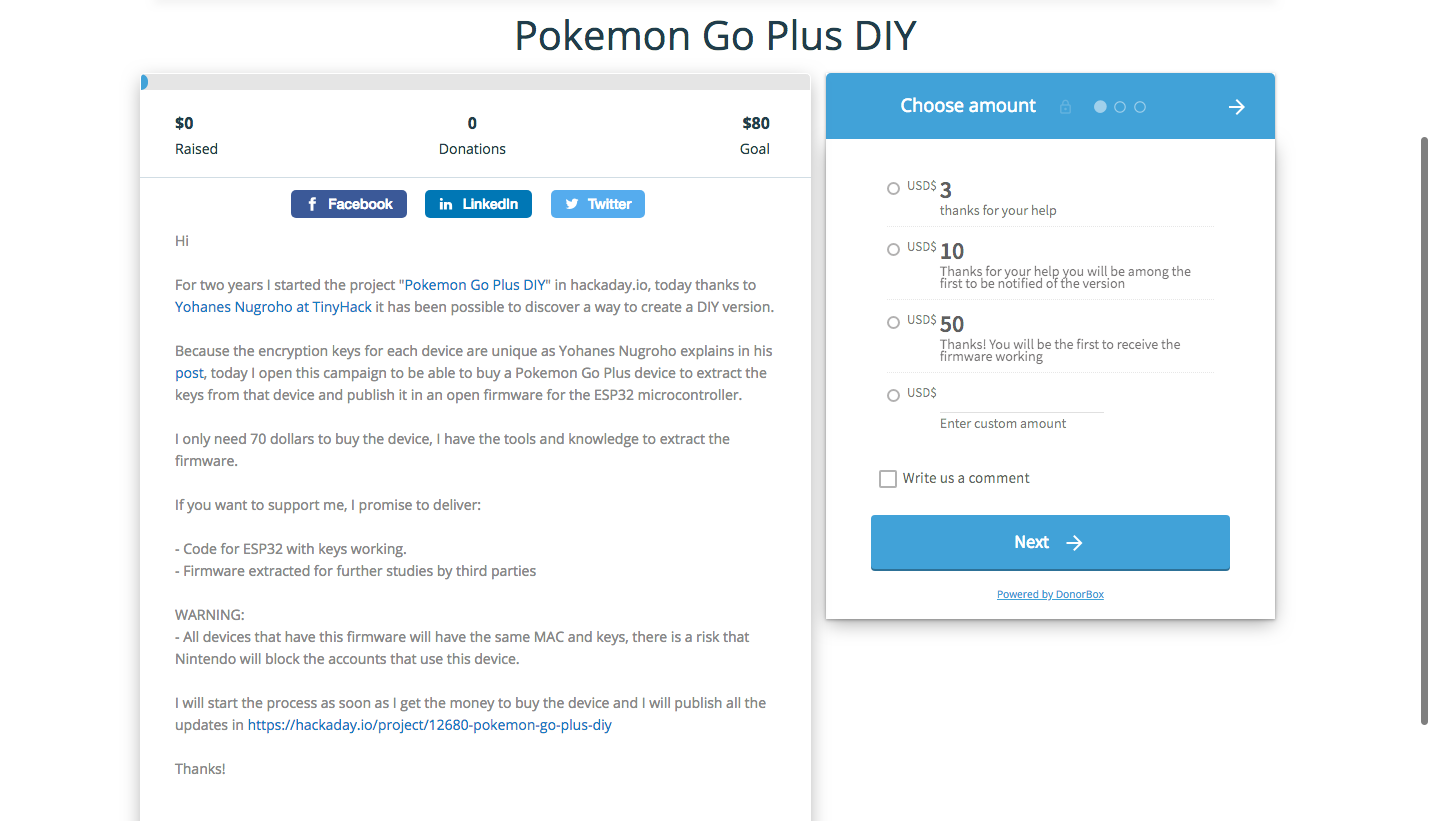
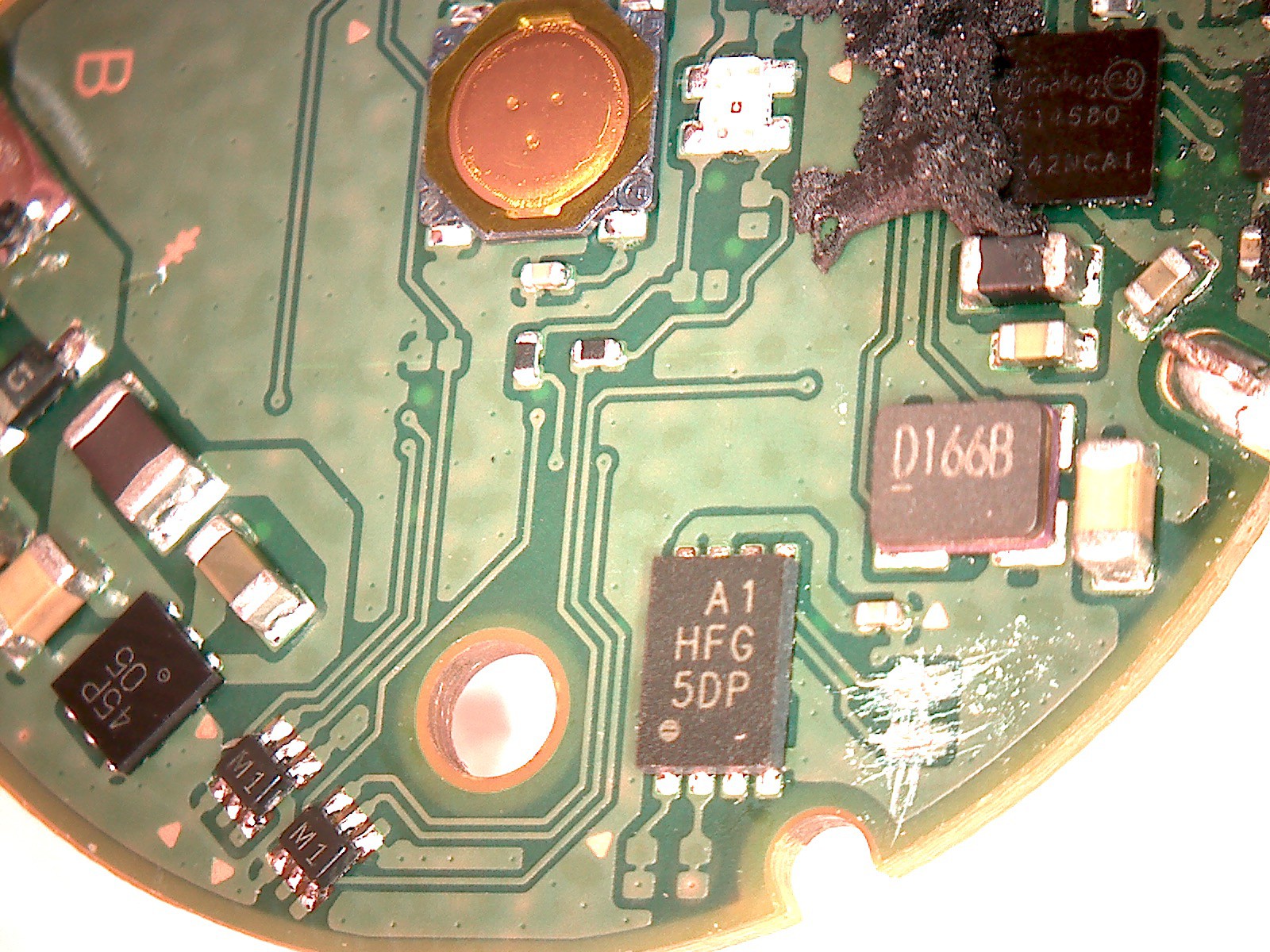
This project is intended to collectively create a DIY version of the famous device Nintendo Pokemon Go Plus, which can be created with different platforms
Platforms supported:
- ESP32
Possible
- Arduino + BLE
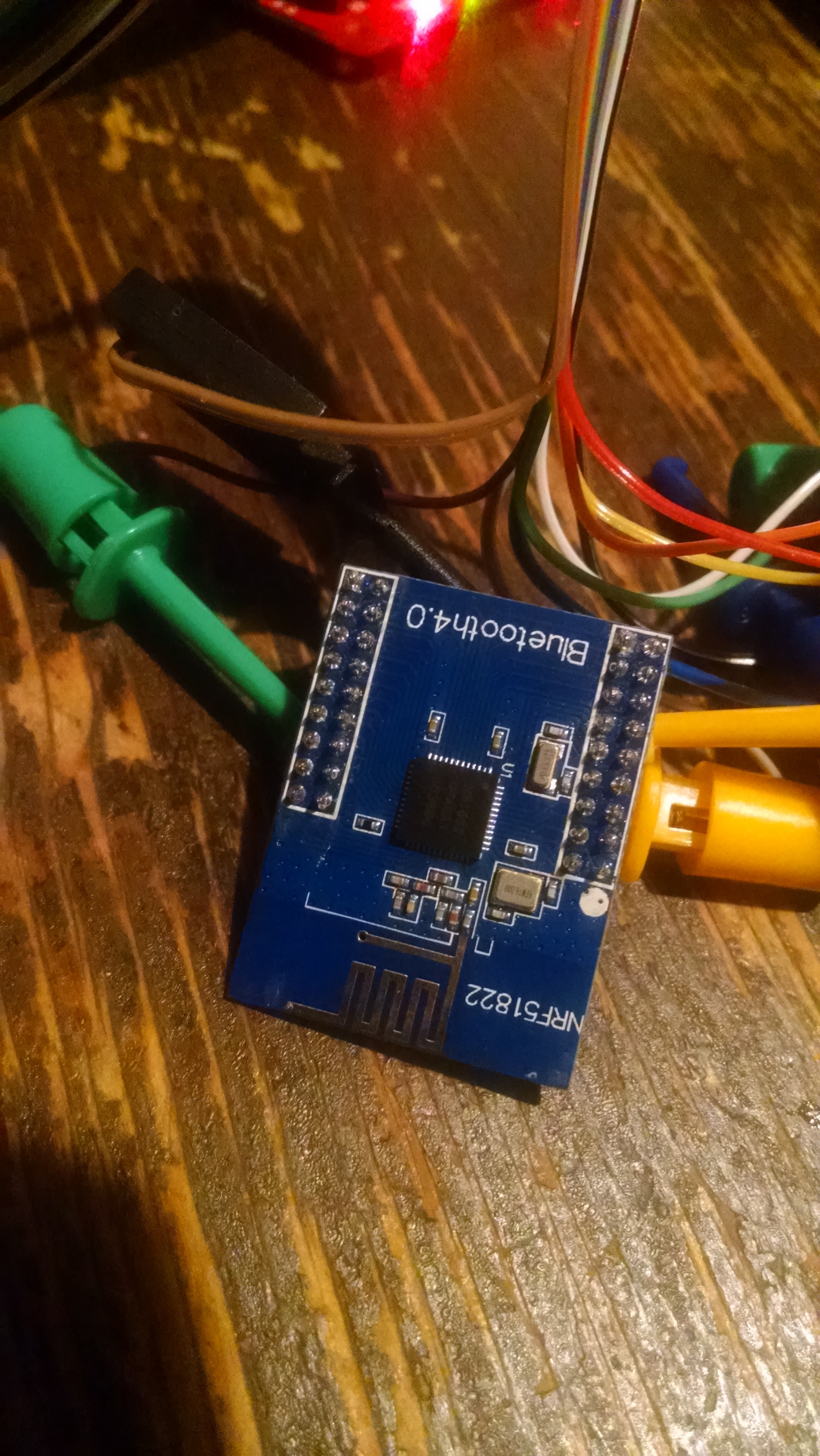
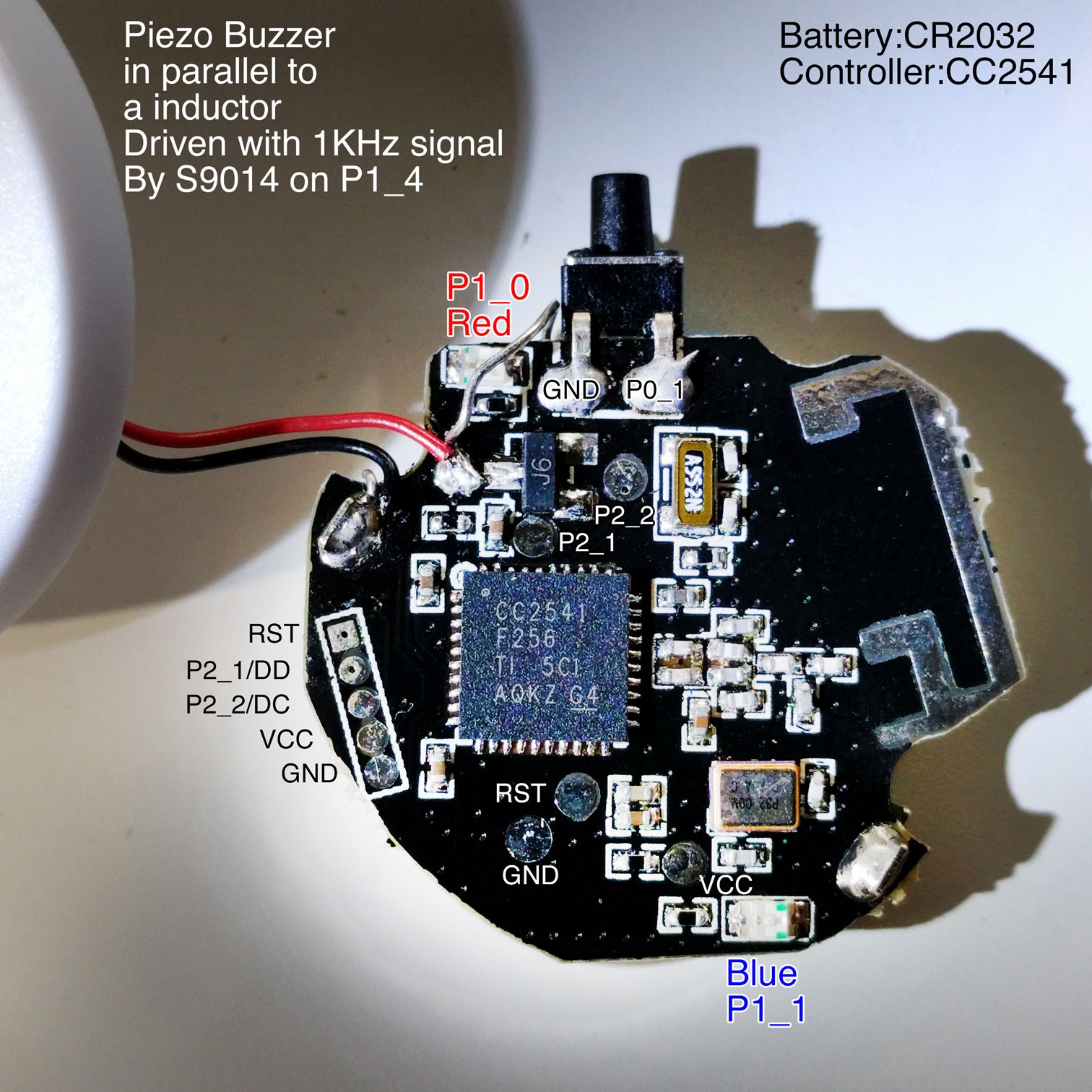
- nRF51822
- Raspberry Pi
Welcome your help and comments
 Sabas
Sabas
















Thanks for the exciting update! My Boy APK, a famous GBA Emulator has arrived, and we're thrilled!