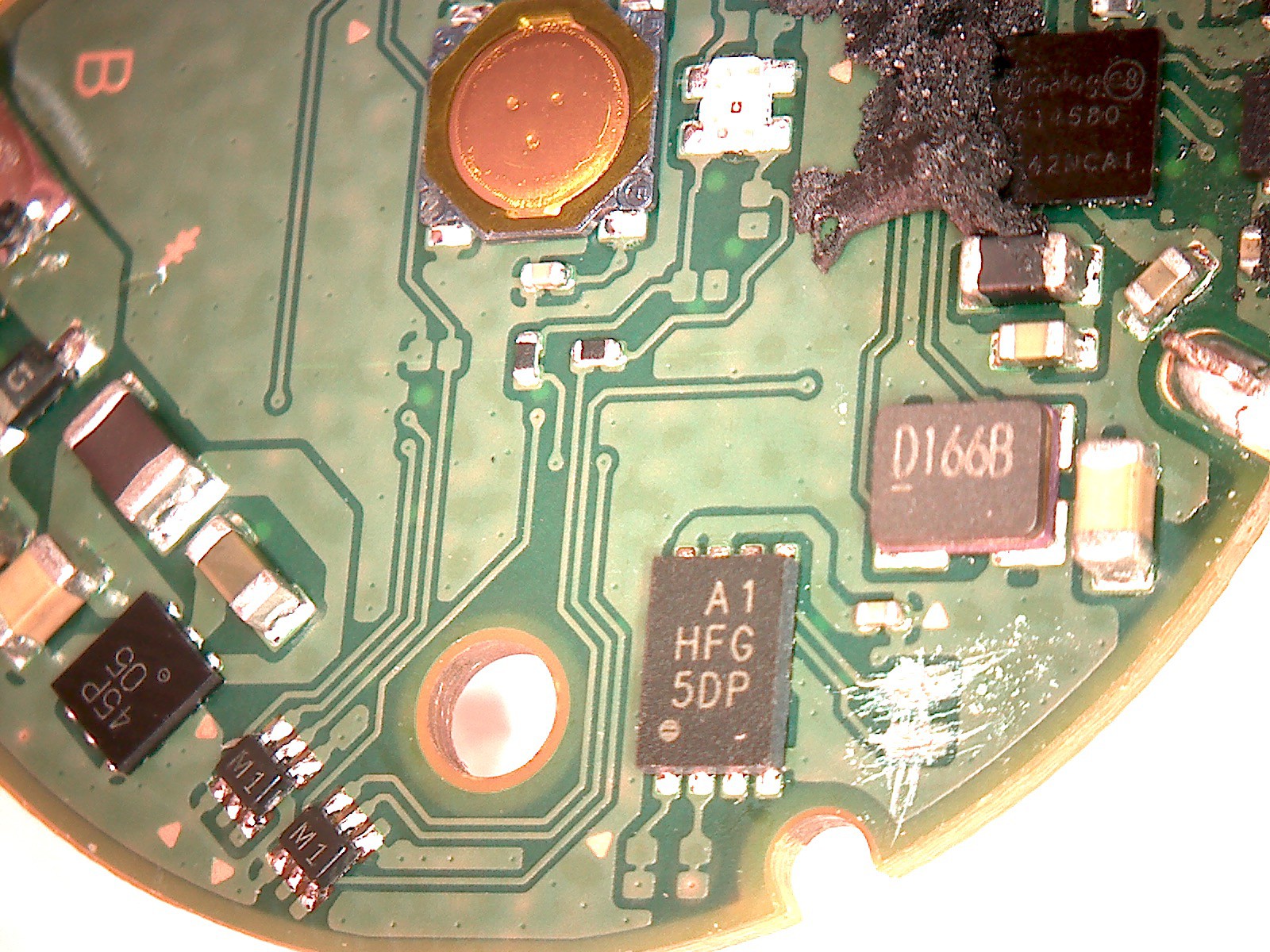
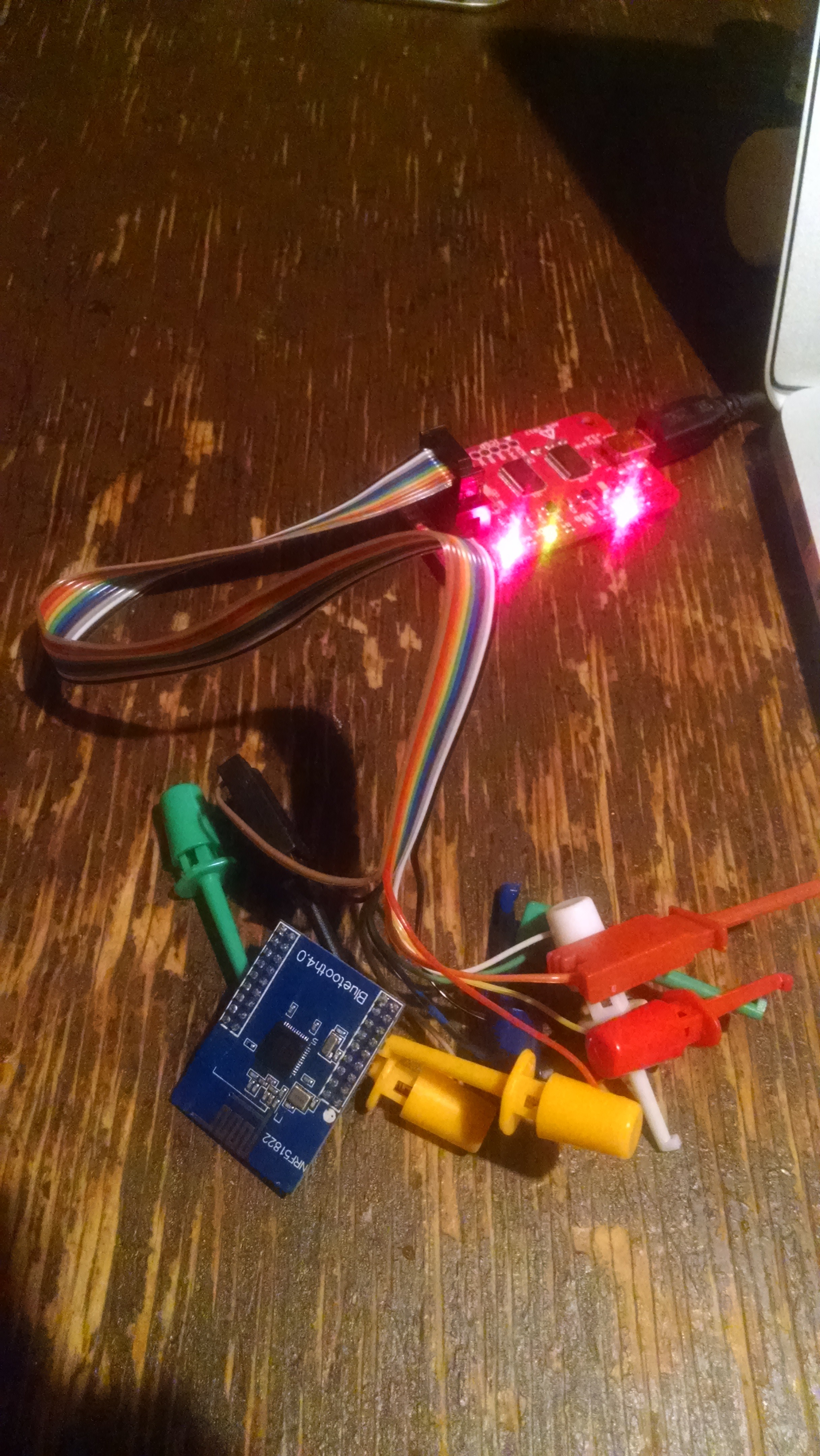
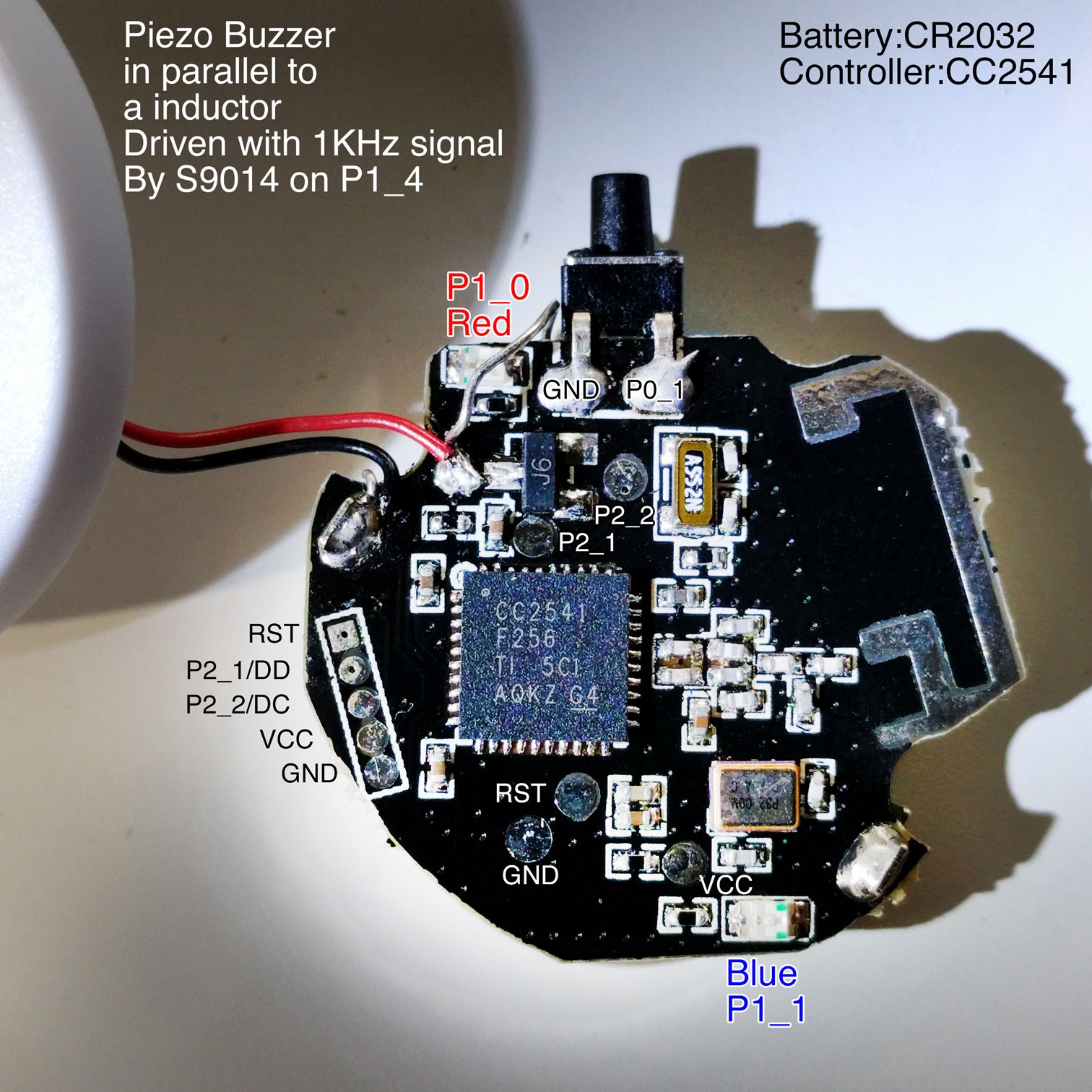
This project is intended to collectively create a DIY version of the famous device Nintendo Pokemon Go Plus, which can be created with different platforms
Platforms supported:
- ESP32
Possible
- Arduino + BLE
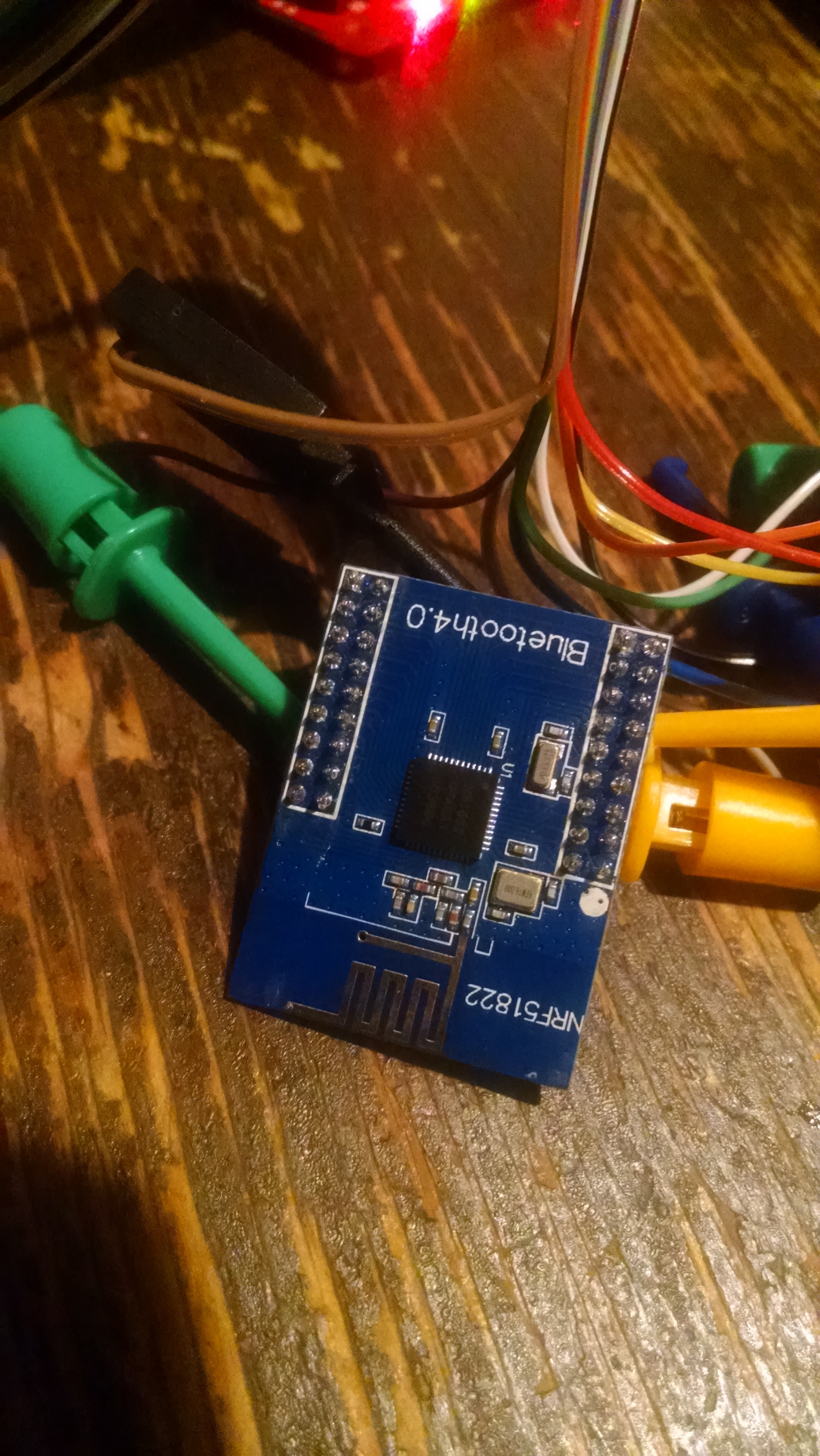
- nRF51822
- Raspberry Pi
Welcome your help and comments
 Sabas
Sabas


















 Sumit
Sumit
 Brad Spry
Brad Spry

 Tim Wilkinson
Tim Wilkinson
hmm, i've been looking into the communication protocols:
"CERTIFICATE_SERVICE:
SFIDA_COMMANDS
bbe87709-5b89-4433-ab7f-8b8eef0d8e39
CENTRAL_TO_SFIDA
bbe87709-5b89-4433-ab7f-8b8eef0d8e38
SFIDA_TO_CENTRAL
bbe87709-5b89-4433-ab7f-8b8eef0d8e3a"
Perhaps the devices all have a unique (authorized) ID to be paired with a device/account?
If so it might be alot harder to get a 'custom' bracelet working with the pokemon go app, as in pairing problems etc. ?