This device was semifinalist of The Hackaday Prize contest ! - Link -
Basically, this device acts as a wifi / ethernet router and access point. It could connect to the internet using some random wifi, a wired network, or a tethered android phone (wifi or usb). On the secured side, it acts as a wireless access point with internet forwarding so it works with every kind of device : PC, laptop, smartphone, using Windows, GNU/Linux, Android or even Mac-OSX.
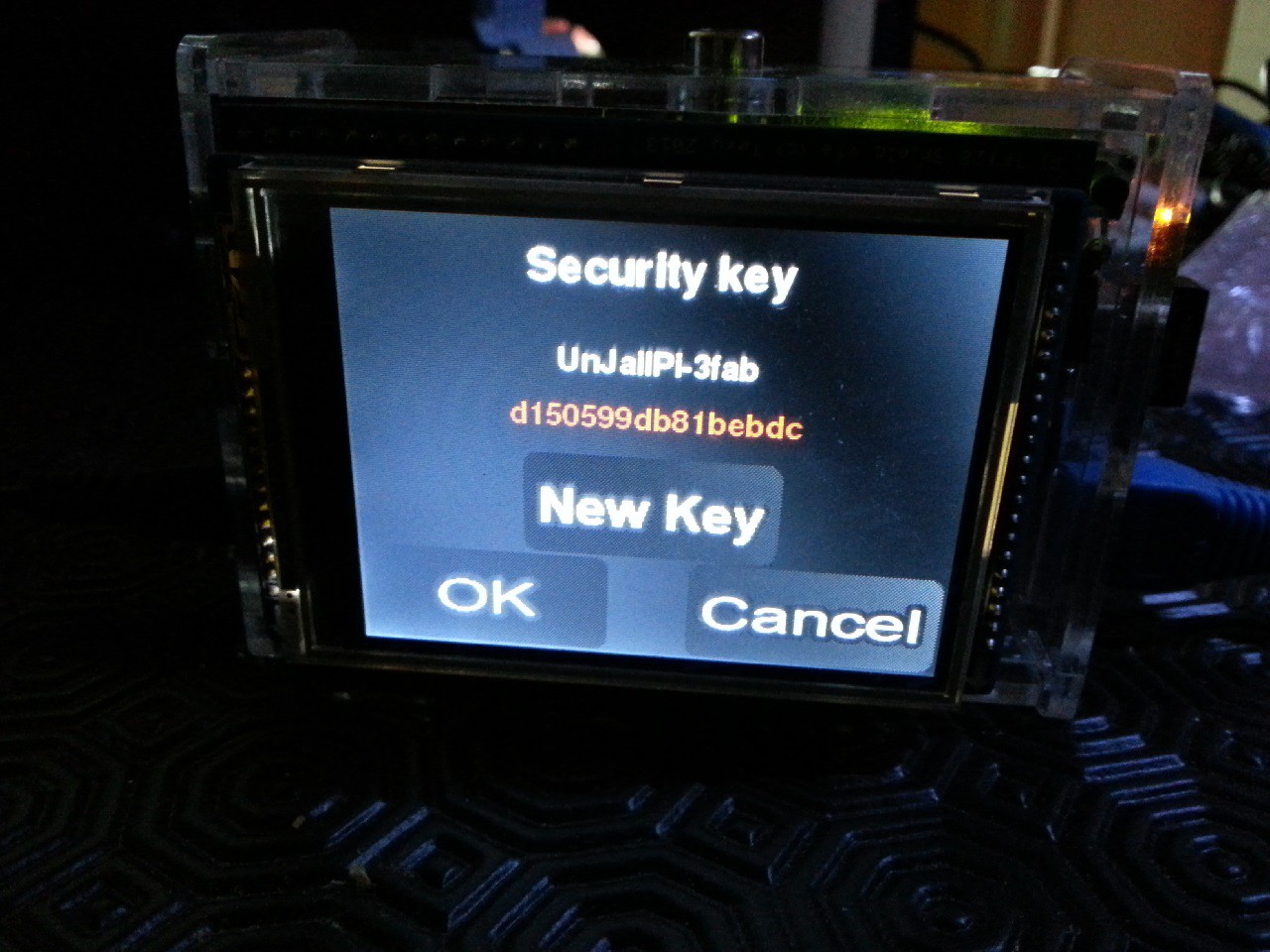
The wireless access-point is also hardened with a random key feature. The access-point security key could be modified on-demand and at boot-time with a random one.
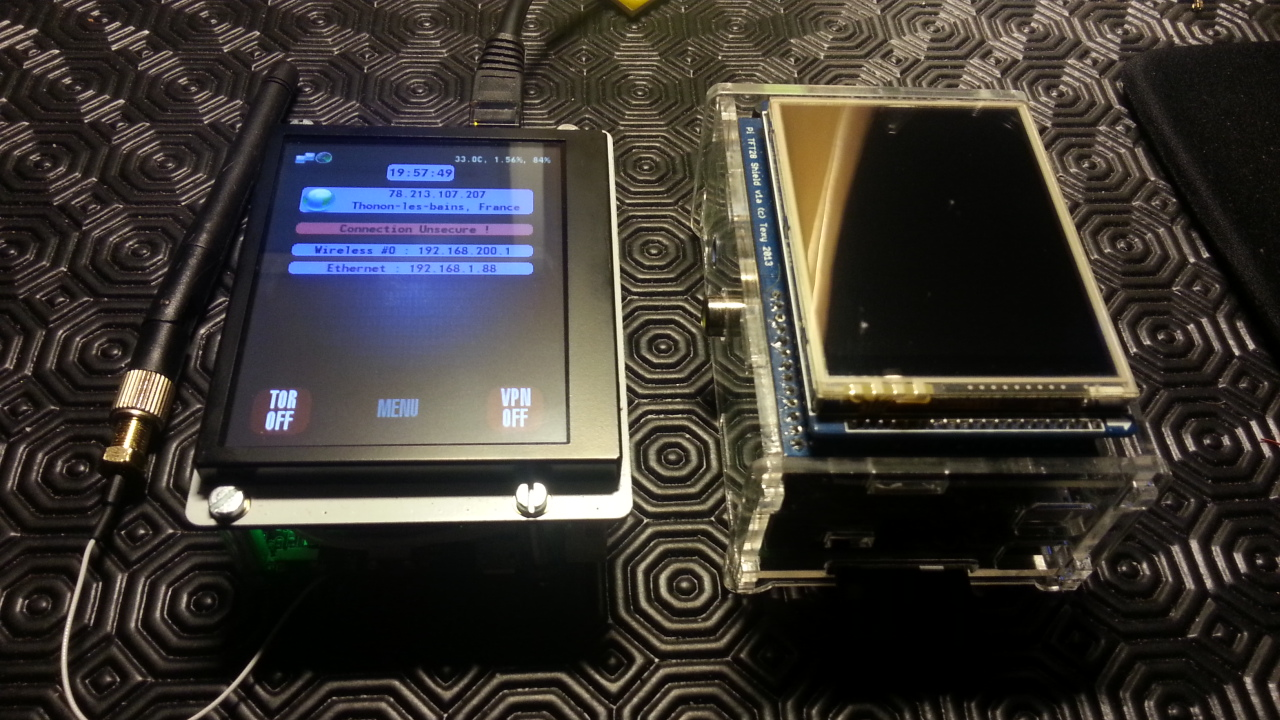
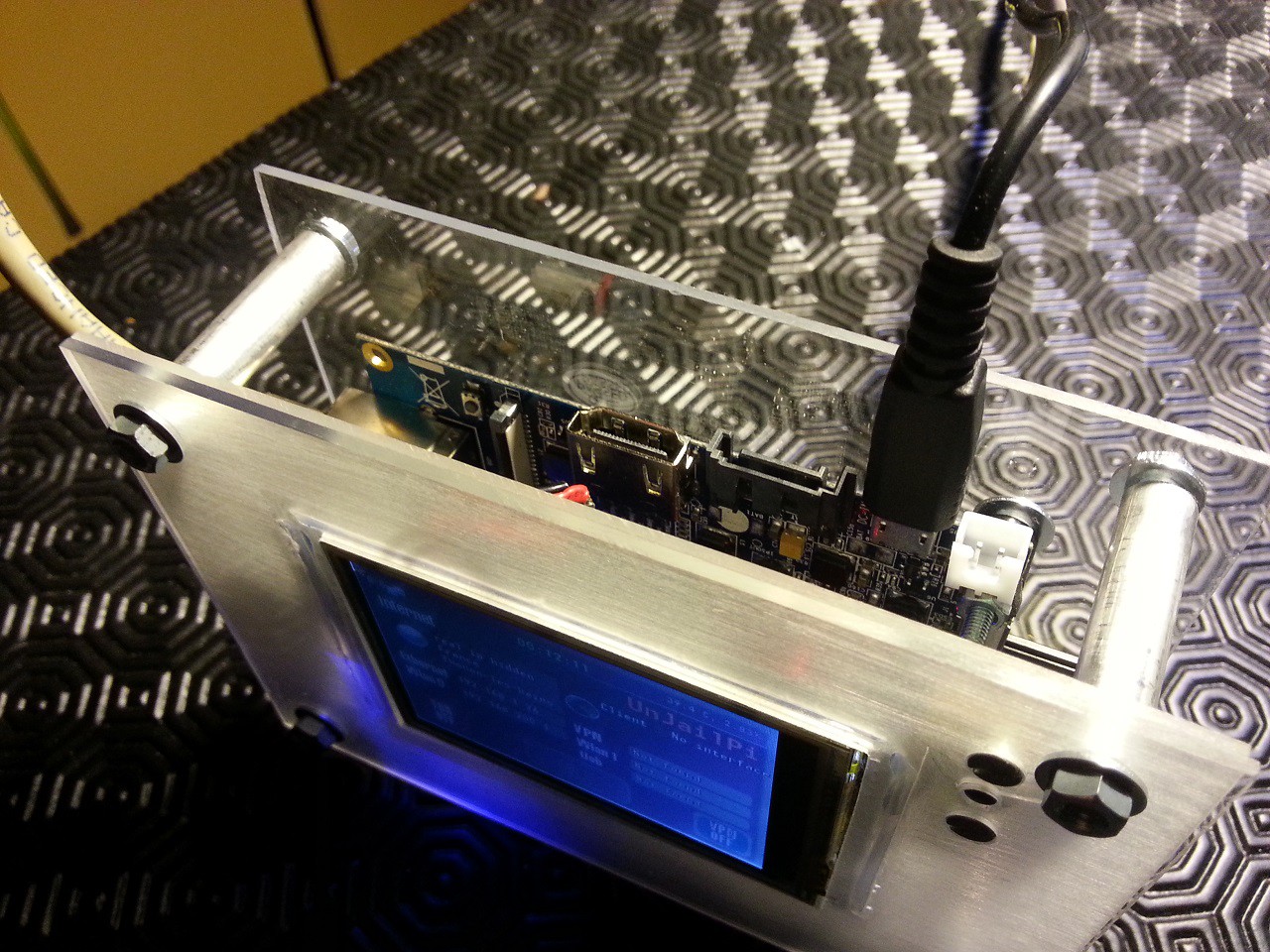
From the touch screen interface, TOR or an OpenVPN tunnel could be enabled. This custom interface could be used for complete operation, full setup and device monitoring.
It only needs a wifi adapter and no setup on the endpoint device (computer, smartphone…) to work. The user interface is also very easy to use with on/off buttons, so it is very easy to operate by non tech people.
In sensitive situations, the complete software and operating system could be installed in a few minutes from a preconfigured and encrypted image. The SD-card could also be removed from the device or even destroyed in a few seconds, causing no harm to the device, but makes it completely empty and useless. This way, sensitive data such as SSH private keys are secure.
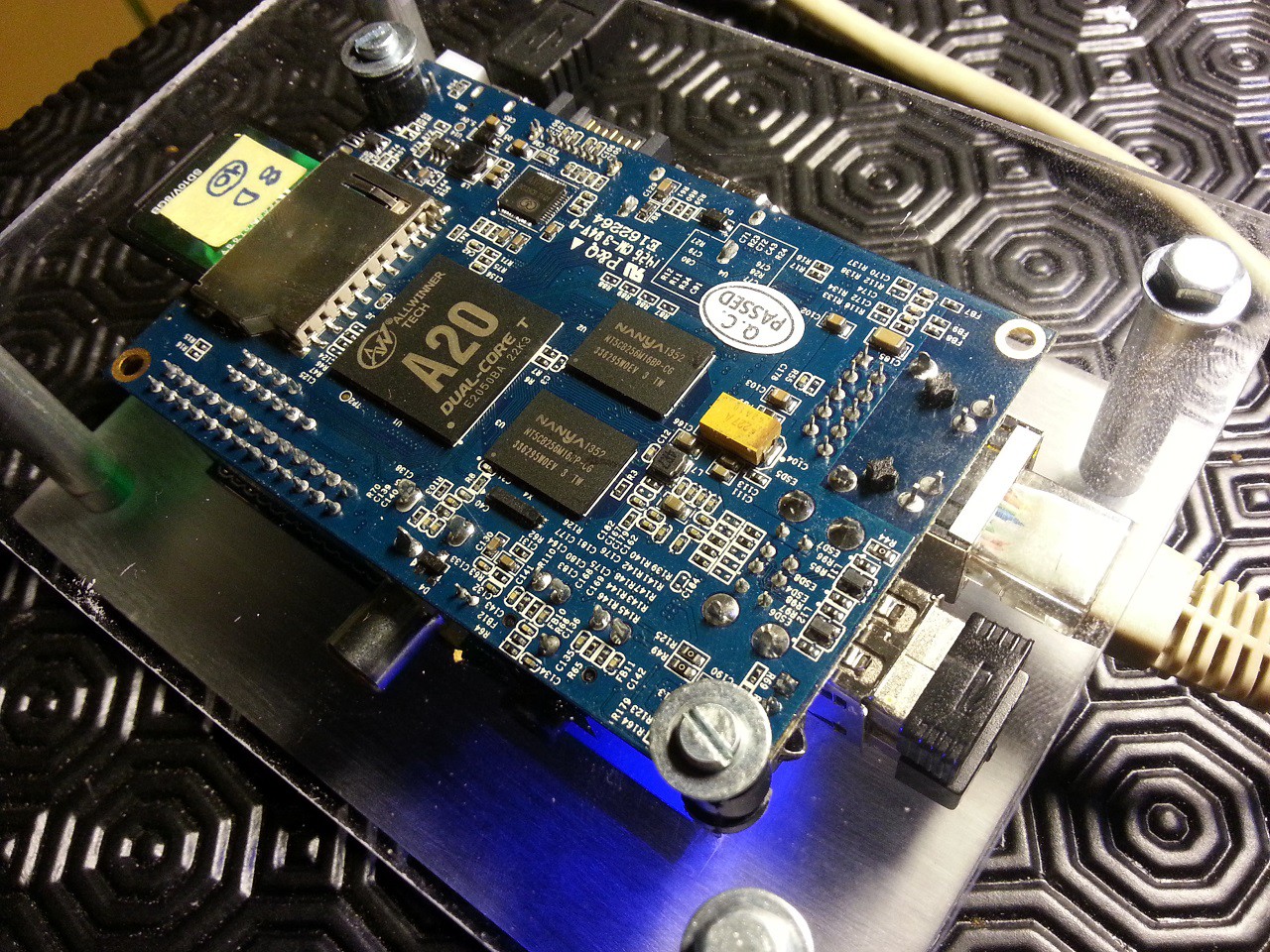
The device hardware is open source, and uses only free software. This way, it could be improved by the community when it needs to, and it also helps defend digital freedom and Human Rights.
It also makes a perfect device to fight planned obscolescence : the software is built to be cross-compatible with different boards, offering different features, to adapt to various situations and evolve over time.

The device could be built at home using some easily sourceable parts and laser cut enclosure in a ready-to-build kit (see below), but could also be easily customized and manufactured for specific needs.

Key features
- Secure wireless access point, with random security key generation features :
- Quick connect to Android using QR code
- AP security forced on WPA2-PSK
- On-demand OpenVPN transparent tunnelling to a remote trusted network/server (here, it is a second Raspberry Pi) :
- Point to point tunneling with internet forwarding
- Very stable and fast over wireless, cellular and other non reliable networks
- Keeps connected over a roaming connection
- On-demand Tor transparent proxy :
- Anonymous browsing,
- Access forbidden websites / services based on location
- Force or Block relay nodes based on their location, from the main interface
- Hardware firewall with dynamically and automatically addressed rules
- Capable of traversing NATs and firewalls
- Ad-blocker / DNS filter feature with quick custom rules
- Touch display control interface
- Very low power consumption : ~5 Watts, runs on a phone charger
- Onboard 2600 mAh battery : ~4h running time
- External 10000 mAh battery : adds ~8h and charges onboard battery
- Very easy to operate, install and deploy
Why is it an important device ?
- It prevents people from learning your physical location or browsing habits,
- It helps defend individuals against traffic analysis,
- It helps businesses to keep their strategies confidential,
- It helps activists to anonymously report abuses or corruption,
- It helps journalists to protect their research and sources online,
- It helps people to use online services blocked by their local Internet providers
Target audience
- People who want to fight a form of network surveillance that threatens personal freedom and privacy,
- Every kind of job/activity that require confidentiality / privacy / security,
- Every kind of job/activity that require some secure remote access,
- Journalists / Activists
How you can help
This device is still in a prototype stage. It is actually looking for many things :
- some technical and security expertise
- a lot of feedback (reason I don't have any comments is still a mystery)
- some funding would really help, I'm looking for a solution to...
 Arcadia Labs
Arcadia Labs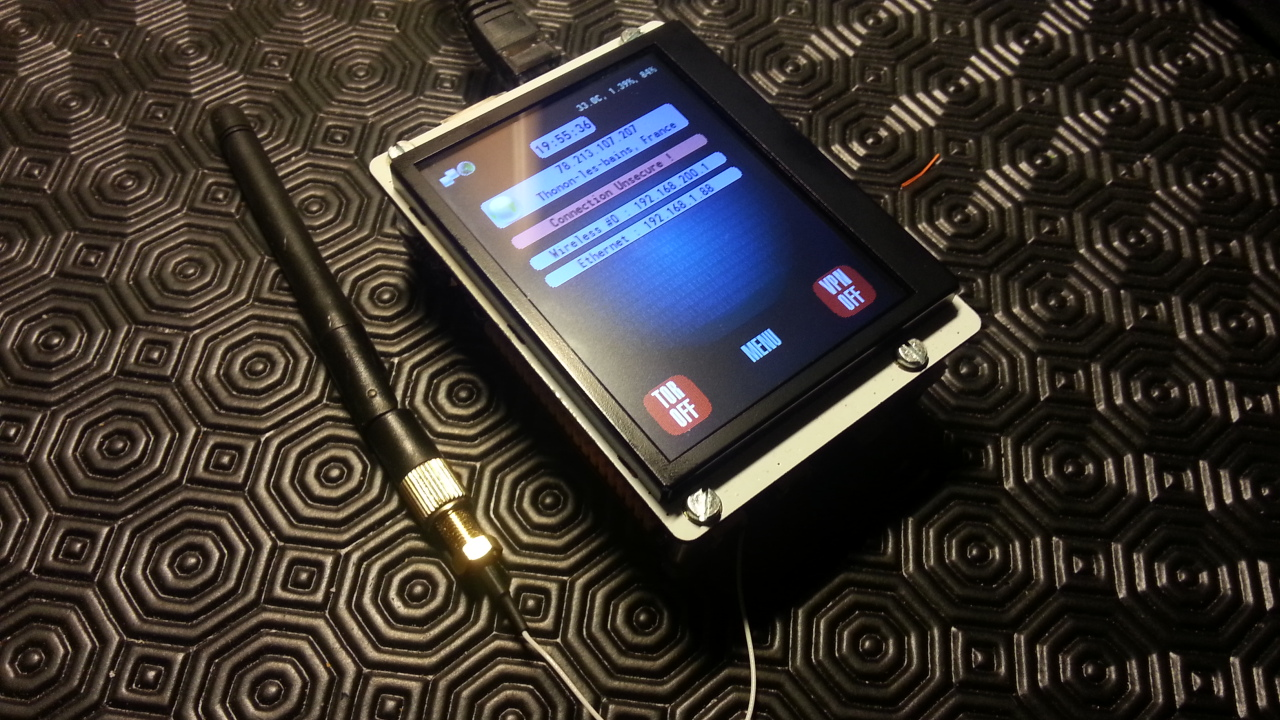











 AKA
AKA
 Muriel Green
Muriel Green
 Sergio Demian Lerner
Sergio Demian Lerner
 robheffo
robheffo
Is it possible to use a PIC instead of the Pi?