NSA Away Hackaday Prize Criteria
Our five minute semifinal video
How “Open” is the design?
NSA Away is designed to be both open source software and open source hardware. This is not just because it is a good thing to do. Since trust of the device is a fundamental requirement, the open nature of the design and implementation are critical to its functionality. This device could not succeed if it was either closed hardware or software. Because openness is a fundamental requirement, this makes it an excellent showcase for the open source hardware and software movement and highlights the need for programs like the Hackaday prize to provide incentives for devices like the NSA Away to be developed.
“Wow” factor: is the entry innovative, is the build impressive?
The concept of unbreakable one-time-pad encryption was first proposed in 1882, but it has been unwieldy and impractical for regular people to use it until now. This ambitious project required extensive hardware and software development. We have interfaced multiple devices in a user-friendly and convenient way.
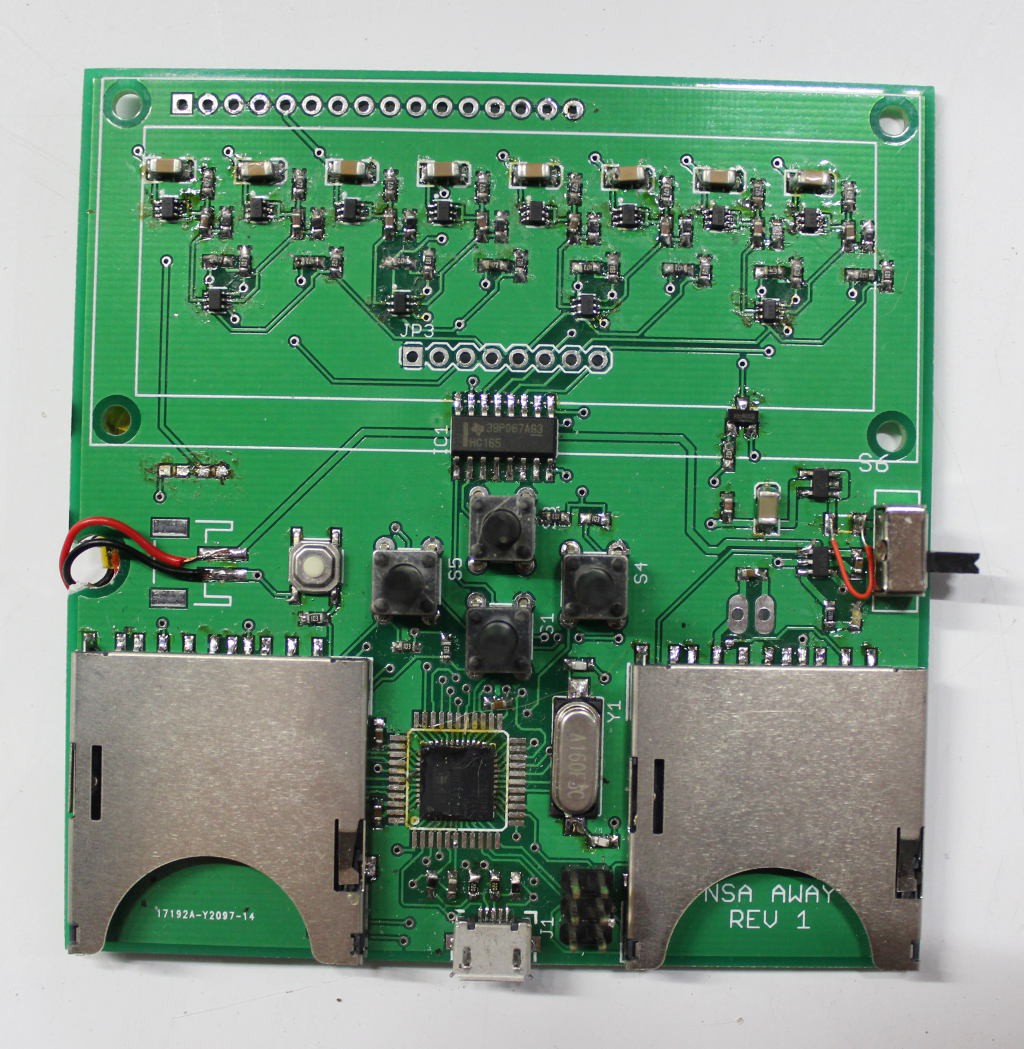
Specifically, we designed and implemented a true hardware random number generator that saves the same random key to two SD cards and designed and 3D printed the case to protect this new device. We wrote user-friendly software for the android phone to read the SD card and encrypt the message the user types in. We went through several design iterations before settling on a reliable yet secure way to send the information from the encryption device to the laptop. We wrote and integrated software to interface with Google’s open source Tesseract optical character recognition engine to provide on-device OCR so that the receiving person can decode the message easily.
Is the entry a connected device and is that “connectedness” meaningful to the function?
The function of the NSA Away is to allow friends and colleagues to connect safely and privately. Improving social connectedness via technical connectedness is the absolute purpose of the device. By being connected yet separated in very specific technical ways, the NSA Away solution allows two individuals to maintain the privacy of their communications even if they do not trust their own PCs or the network connections between them.
Is the project reproducible and could the work be extended for other uses?
We have designed and implemented the solution in an open way, so anyone could use our design and implementation to reproduce their own NSA Away devices. The concepts and work behind the NSA Away project could be extended in several different innovative ways. Our solution as implemented provides human verifiability to all steps of the process and keeps the encryption keys and message composing/viewing device isolated from any Internet-connected infrastructure. If those are not hard requirements, a range of other extended applications are possible, including:
- Use of asymmetric key algorithms (GPG, etc) so that key pre-sharing is not required.
- Running the encryption/decryption applications on a non-dedicated smart phone or tablet device, directly integrated with the device's chat and email functions or other custom applications. For instance, using the NSA Away project as a base it is easy to imagine an open source snapchat-type application with pre-shared keys and true forward secrecy.
- Using the keystroke sending functionality of the encryption device as a password manager.
- Using the key generation device as a verifiable USB-connected hardware random generator.
- Integrating a cellular or other wireless connection for message sending and receiving, providing an extremely secure pager-class device.
Of course most of those applications compromise privacy or verifiability in one way or another for increased convenience, but all of them would increase privacy, make strong crypto more mainstream and decrease the effectiveness of bulk surveillance.
Does the entry exhibit engineering innovation?...
Read more » Scott Hasse
Scott Hasse



















 Johannes
Johannes
 Andrey Ovcharov
Andrey Ovcharov
 bsutton
bsutton
 Sam P
Sam P
this is a great idea but you need true random number generation.... digital circuits will always have some predictability!