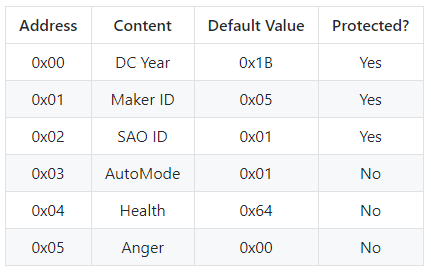
CTF Leaderboard
Click here for the leaderboard
If you don't appear, there's not a problem, you either....
1) Haven't been near a proxy node at the conference yet
2) Haven't figured out the first step to appearing on the leaderboard...
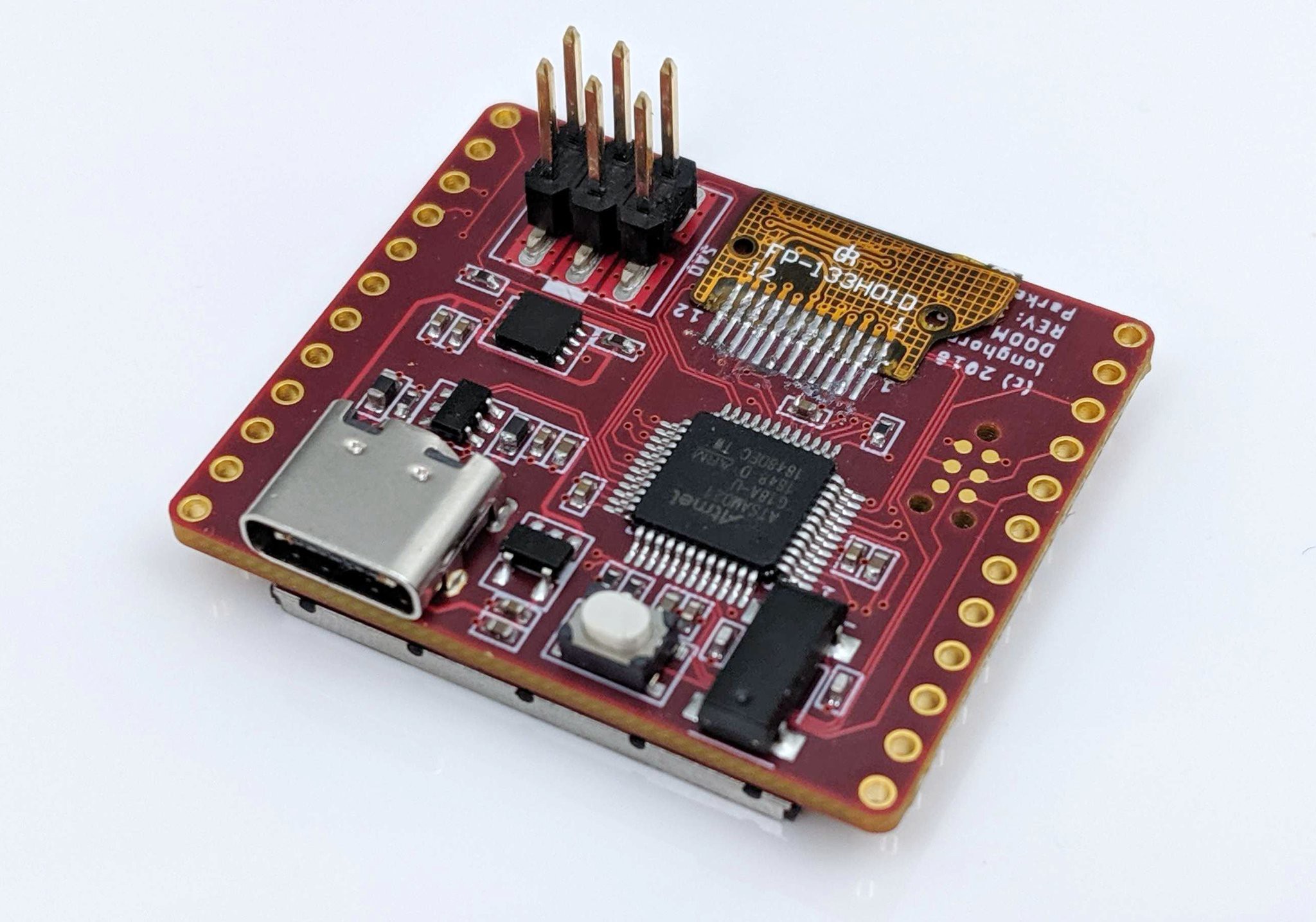
BADGE HARDWARE SPECS
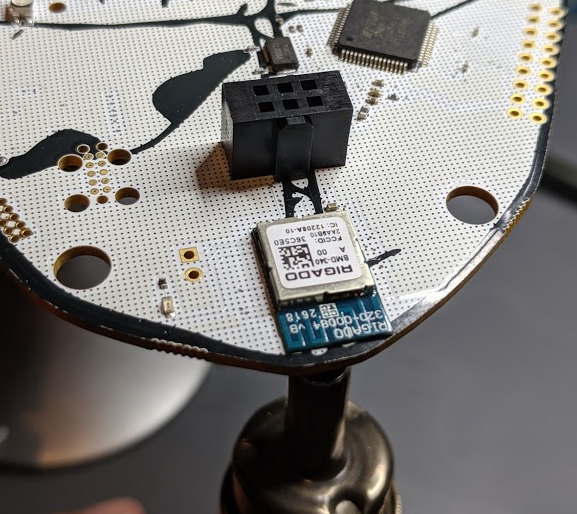
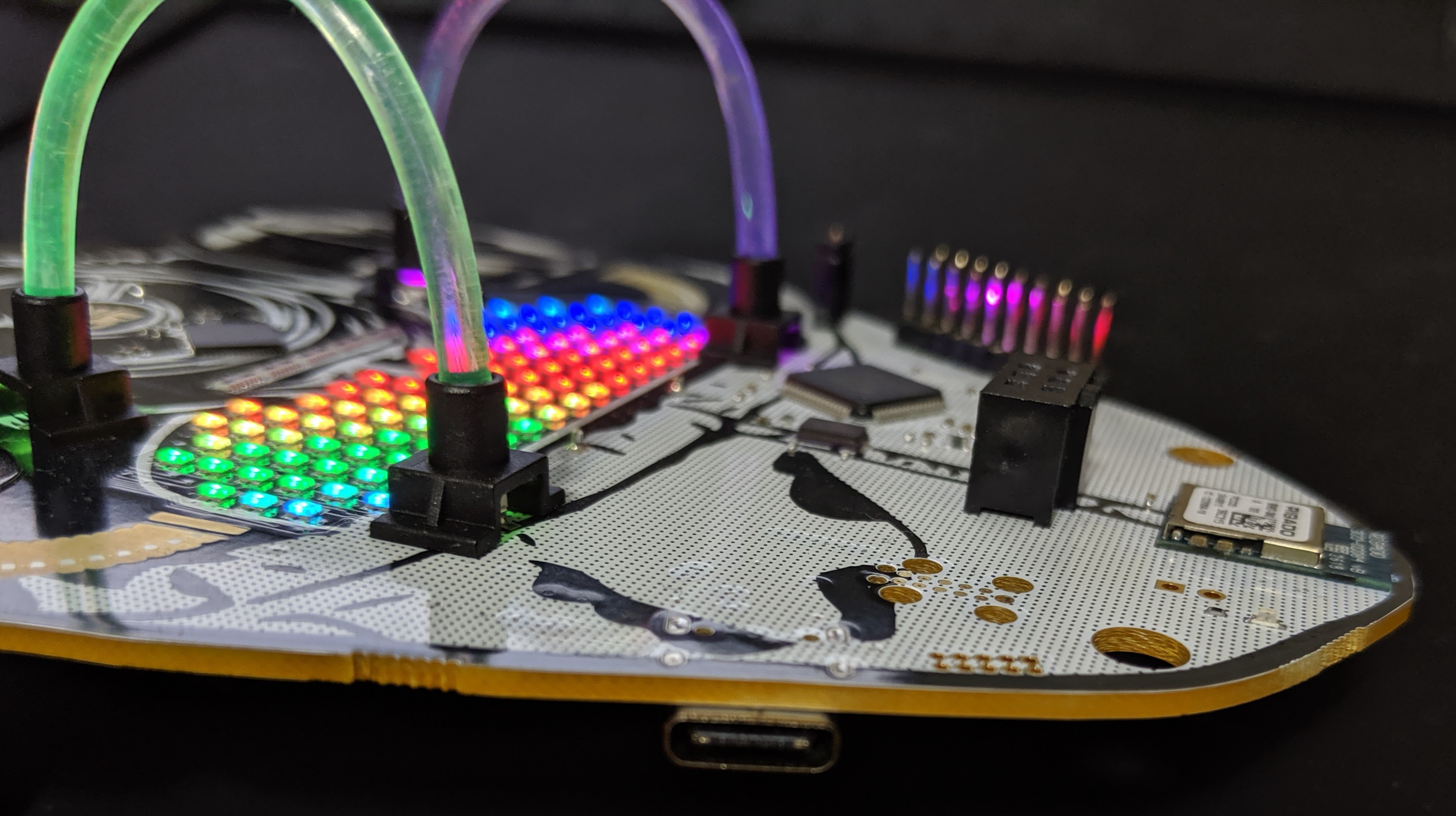
- System on Chip - Rigado BMD-340 (NRF52840 core)
- LED RGB - HQ19-2333RGBC
- LED Controller - IS31FL3741
- LDO - LM1117 ADJ
- Boost - AAT1217-3.3
- Captouch IC - IQS333
- Battery Holder - Keystone 2460
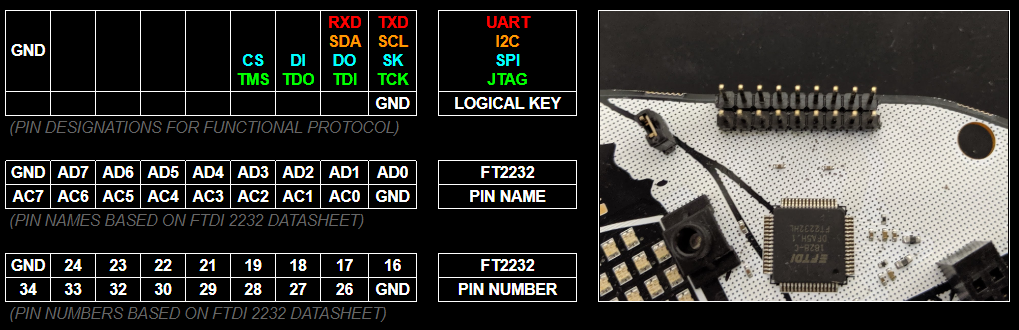
- USB to UART Bridge / Hardware Hacking Debugger - FT2232H
- Light Pipe
- SWD Programming Interface
- Tag Connect Programming Interface
- SAO 1.69bis Interface
- USB C Interface
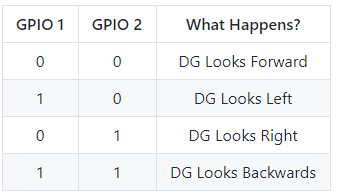
BADGE FUNCTIONS
- Bling
- Full LED Matrix, LED Back Lit Light Pipes, Glow In The Dark Cap Sense

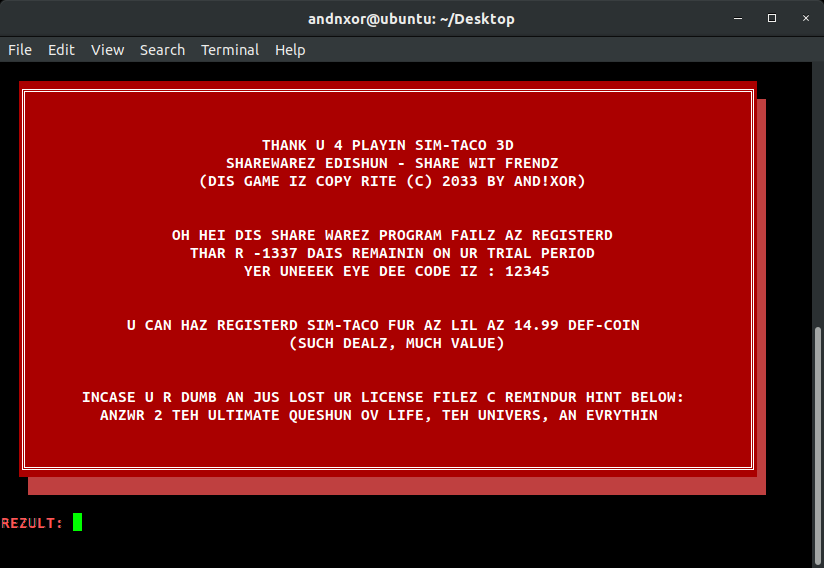
- BOTNET
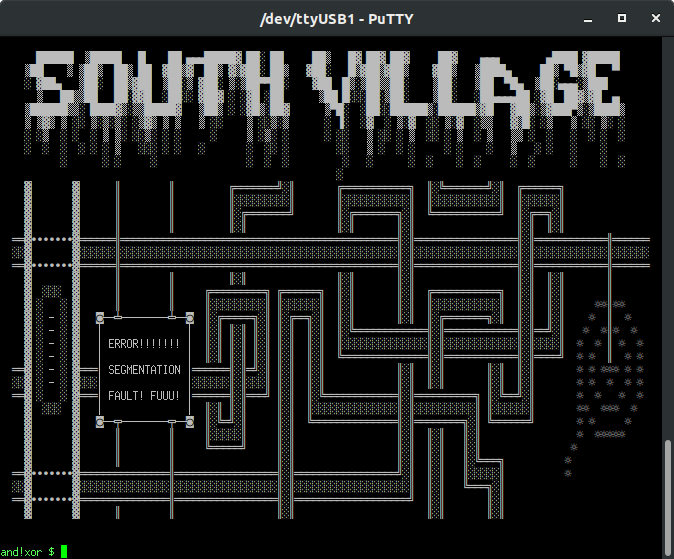
- The badges create an IoT bluetooth mesh network throughout the conference. Consider this badge your wireless modem to join the party... To start, connect to your computer via USB-C, open a serial terminal, and connect to (/dev/ttyUSB1) with serial settings 115200/8/N/1 within the conference area to join the mesh. Any command run on your own badge, can be remotely executed on other badges, without authentication or authorization. These are IoT devices with industry standard security...meaning none! With great power comes great responsibility, show us what you can do.
- Future Log Coming Soon...
- Badge Enabled Non Directive Enigma Routine (B.E.N.D.E.R)
- The Badge Enabled Non Directive Enigma Routine is back for more embedded text based adventure hacking challenges. To start, plug this badge in to your computer, open a serial terminal, connect just like above, and type “bender help”
- Future Log Coming Soon...
- Hardware Hacking Tool
- The badge includes an on board FTDI 2232 breakout. Which not only makes it the sexiest USB-C based tool out there, but adds the ability to hack embedded interfaces for UART (/dev/ttyUSB0), JTAG, SPI, I2C, and general bit-banging. Hack the planet and other badges with this badge.
- Future Log Coming Soon...
WHO:: We are 5 dudes from California (and a guest star from Texas) with backgrounds in HW and SW engineering. We enjoy building and hacking things for fun. AND!XOR pronounced..."AND-NOT-EX-OR"...
WHAT:: We built a hackable, open badge for use at DEFCON 27 in Las Vegas and any other conferences in the future. The badge also serves as a dev board for hardware developers of any experience level from novice to expert sorcerer.
WHY:: The purpose is to put some really awesome hardware around the necks of a bunch of hackers and see what they come up with. We hope to encourage others to make use of the badge and come back with their own flavor in years to come, AND to promote embedded development across the community. Most importantly, the badge serves as a way to teach principles about security and hacking.
HOW:: Pure internet science. We've developed algorithms which calculate the spin rate of cat quarks for generating our ssh keys at a rate of (P+9)/((# of blackberry users)^2), where P is the probability that a cat will leave a house when a door is opened for them. Through philanthropy and sponsorship we are able to raise enough funds to give these away for FREE during hacker summer camp. Thank our generous sponsors:
WHERE:: Paris / Bally's / Planet Hollywood, Las Vegas
WHEN:: Aug 7th - Aug 11th, 2019
EXTRAS:: We are spending our free time and money outside of our busy work schedules to develop this from 5 separate locations across the US. So we are definitely open and encourage feedback, suggestions, and features to be added onto the badge. If you complain that there are not enough blinky's happening then you are welcome to build your own....
Read more » Zapp
Zapp



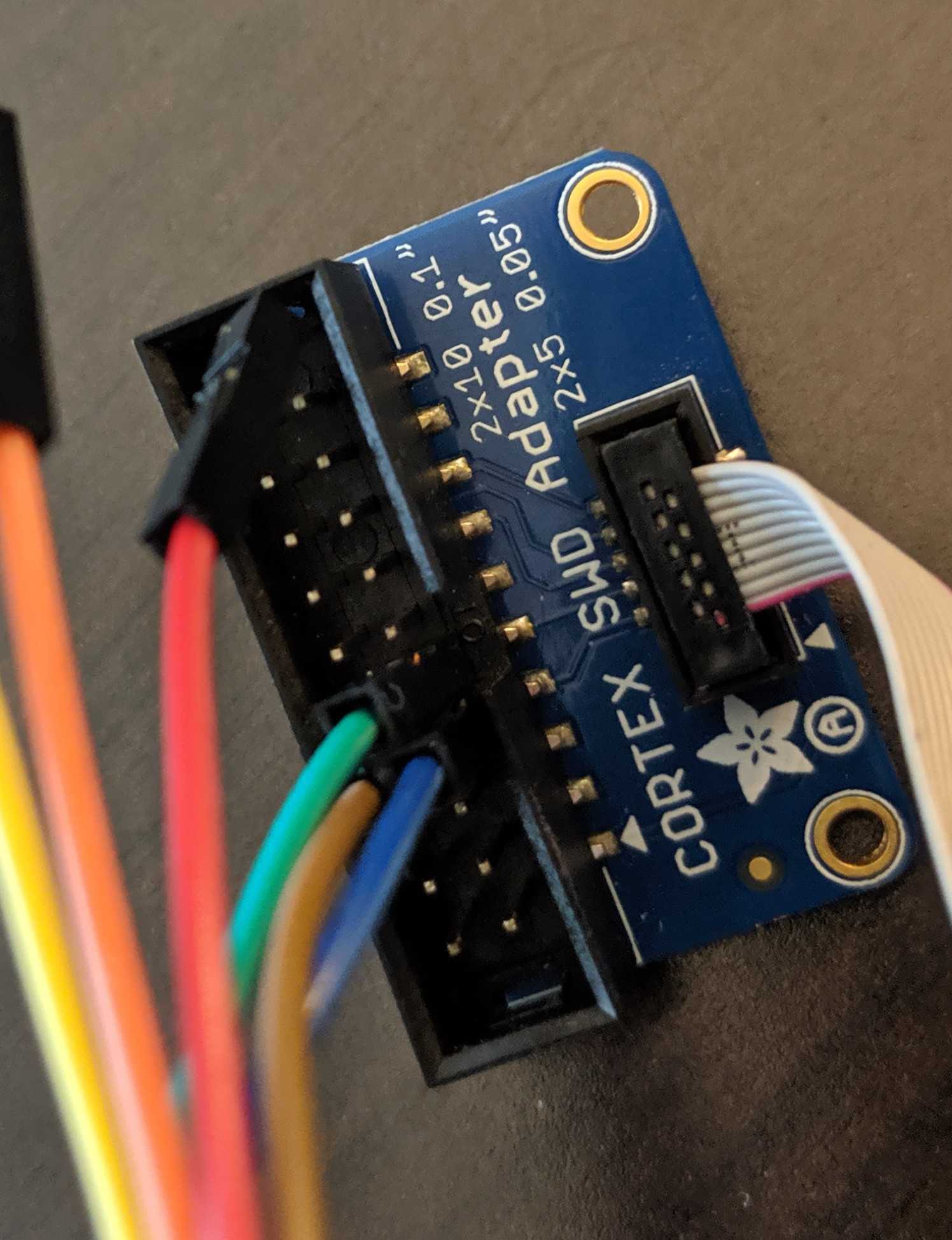
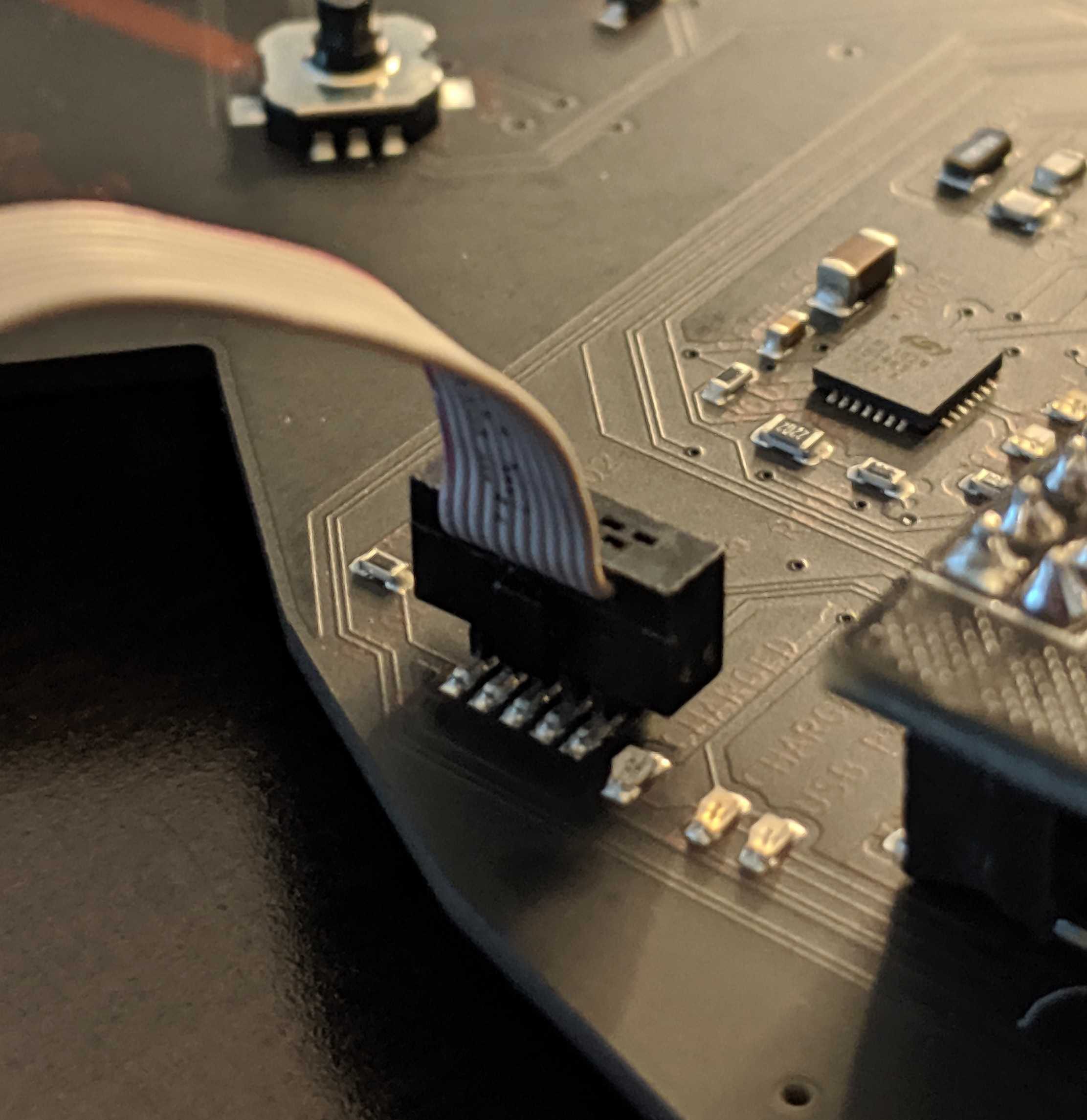
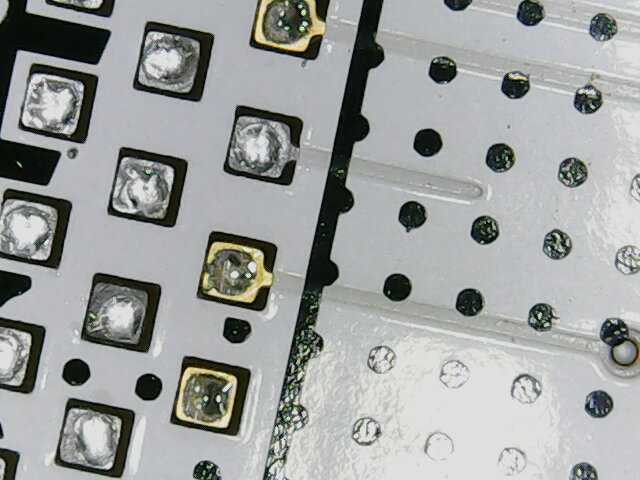
 Referring to the FT2232HL datasheet, the key channel A pins for MPSSE are TCK/SK, TDI/DO, TDO/DI (ADBUS0, ADBUS1, and ADBUS2 respectively).
Referring to the FT2232HL datasheet, the key channel A pins for MPSSE are TCK/SK, TDI/DO, TDO/DI (ADBUS0, ADBUS1, and ADBUS2 respectively). 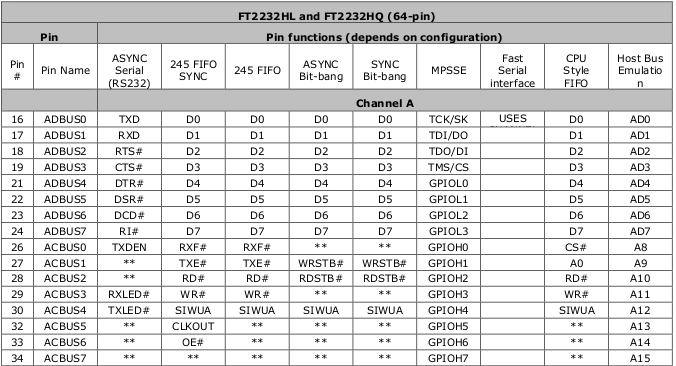 The trick is wiring TDI to TDO with a resistor and to SWDIO on the SWD interface since the SWD interface is just SWDIO and SWCLK. SWO, nRESET, and Vcc can be ignored.
The trick is wiring TDI to TDO with a resistor and to SWDIO on the SWD interface since the SWD interface is just SWDIO and SWCLK. SWO, nRESET, and Vcc can be ignored.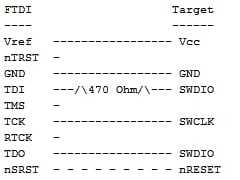 The best way, in our opinion, is to slap a 470 ohm 0805 resistor between ADBUS1 and ADBUS2.
The best way, in our opinion, is to slap a 470 ohm 0805 resistor between ADBUS1 and ADBUS2. 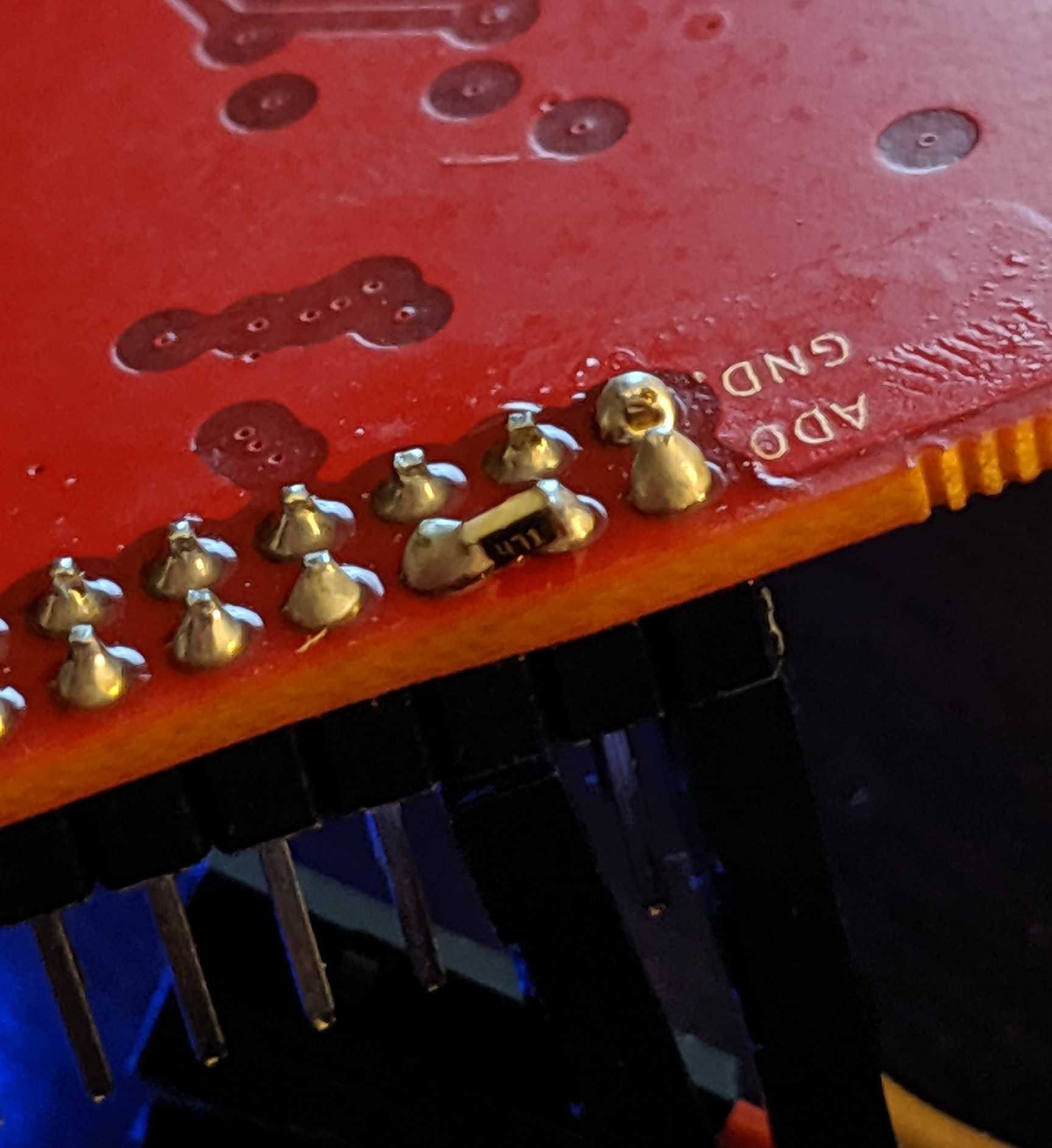
 Not so bad yet.
Not so bad yet.
 Software
Software






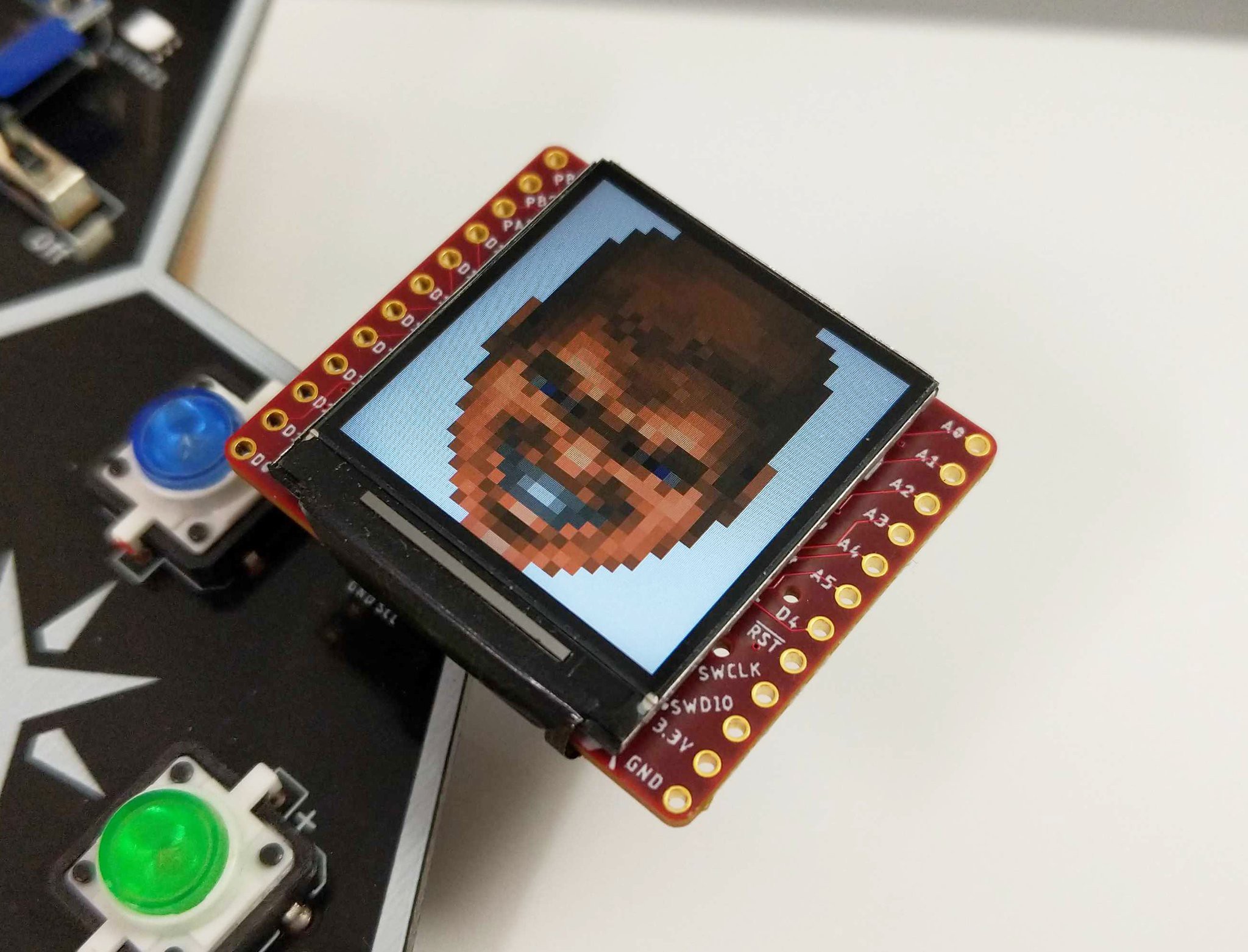
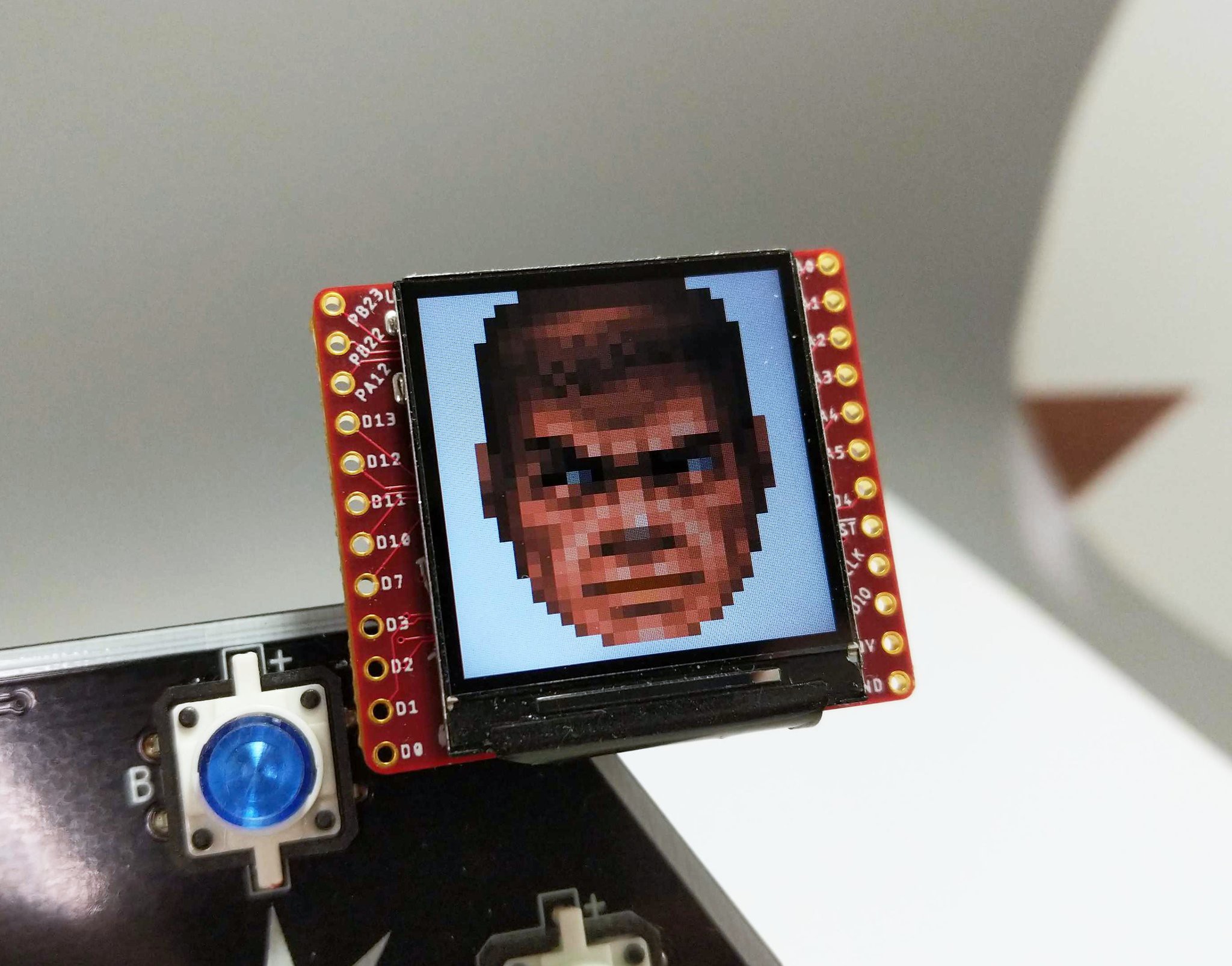
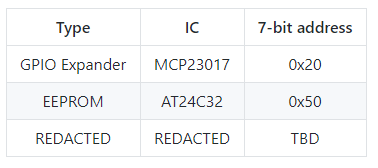
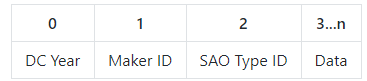









 Voja Antonic
Voja Antonic

 Arya
Arya
what are the Rigado BMD-340 (NRF52840 core), USB Type C, SAO 1.69bis Interface, LM1117 ADJ, AAT1217-3.3 and the IQS333Captouch IC used for, where can you buy the flexable Light Pipes and the HQ19-2333RGBC?